- Cisco Community
- Technology and Support
- Security
- VPN
- Remote Access VPN - No connectivity to Internal Network !
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2012 06:30 AM - edited 02-21-2020 06:27 PM
Hi Experts ,
I can understand that this is a very common issue when considering IPSec Remote Access VPN implementations using Cisco VPN Client. But for the past six months , I have been trying to setup Remote Access VPN at so many client sites and gets stuck up with the very same issue !
-The Remote VPN Client connects , authenticates successfully from local user database (to make things easier , I used local user authentication ) , the tunnel gets established ( I could see from the output of #show isakmp sa as AM_ACTIVE ) . So I think the encryption/authentication settings for Phase 1 /Phase 2 should be working fine since tunnel is getting successfully established
-Now comes the issue , No connectivity to internal network. I have tried all possible resolutions I could find online.
1. The most common problem is NAT - Traversal not enabled
-Enabled NAT-T with default keepalive time of 20
2. No NAT configurations for exempting Remote VPN traffic
-Ensured that No Nat configurations are present in the configurations and the VPN traffic from Internal Network 192.168.1.X to VPN Networks 192.168.5.X /192.168.10.X was being exempted from NAT
3- Split tunnel configurations
-Reconfigured Split tunnel configurations from Standard access list to Extended access list (Even though not required as a Standard Access list is more than enouugh ,if I am correct ) to permit selected traffic from 192.168.1.X to 192.168.5.X/192.168.10.X which will create Secured routes on Client enabling VPN client users to simultaneously access VPN resources and access Internet. The Split Tunnel network group was added again to Group Policy.
4. Enabled /Disabled Perfect Forward Secrecy (PFS)
. As this can be additional overhead, it was disabled /enabled
5. Reverse Route Injection
-Ensured that a temporary reverse route was injected to routing table by enabling Reverse Route Injection for automatically inserting temporary static routes to remote tunnel networks using set reverse route command
A few more interesting things were noted :
Encrypted and Bypassed packets were found incrementing when a continous ping is put to the ASA inside interface.
No Decryption is happening on VPN Client statistics which means there is no reply traffic back from the network.
Decryption happens and the packets are found to be increasing when I try to ping the IP released to the client (192.168.0.10) from the ASA . But on the ASA I am not getting any reply back and showing as ????? . So that would mean that there is communication from ASA to the client through the VPN tunnel whereas no communication is happening from internal network back to client
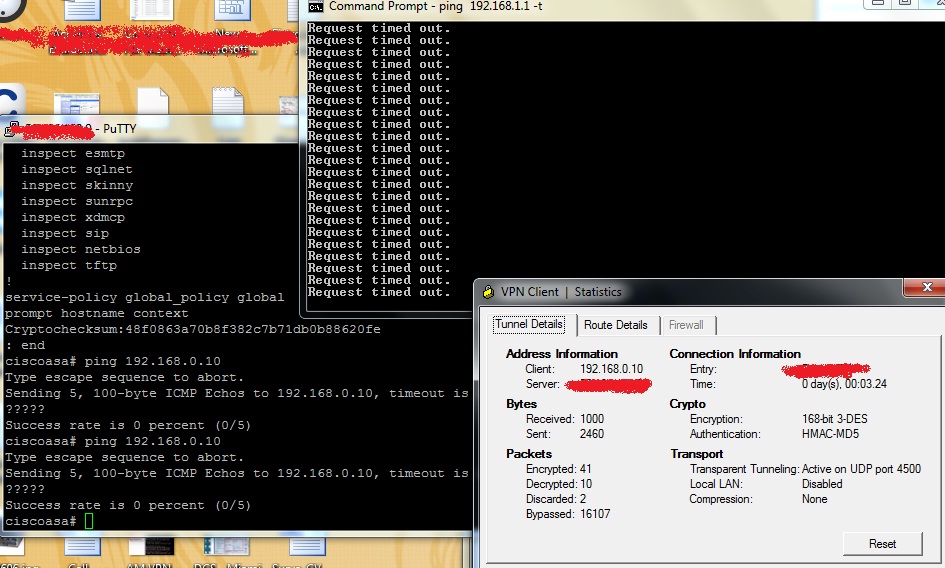
The entire configuration is shown below
ASA Version 8.2(1)
!
hostname ciscoasa
enable password AS3P3A8i0l6.JxwD encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address X.X.X.X 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
access-list NONAT extended permit ip 192.168.1.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list ST1 extended permit ip 192.168.1.0 255.255.255.0 192.168.0.0 255.255.255.0
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside 1500
ip local pool testpool 192.168.0.10-192.168.0.15
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list NONAT
nat (inside) 1 0.0.0.0 0.0.0.0
route outside 0.0.0.0 0.0.0.0 X.X.X.X 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
aaa authentication enable console LOCAL
aaa authentication http console LOCAL
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
http 0.0.0.0 0.0.0.0 inside
http 0.0.0.0 0.0.0.0 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set FirstSet esp-3des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map dyn1 1 set transform-set FirstSet
crypto dynamic-map dyn1 1 set reverse-route
crypto map mymap 1 ipsec-isakmp dynamic dyn1
crypto map mymap interface outside
crypto ca server
smtp from-address admin@ciscoasa.null
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 43200
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 outside
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 5
console timeout 0
dhcpd auto_config outside
!
dhcpd address 192.168.1.10-192.168.1.132 inside
dhcpd dns 8.8.8.8 4.4.4.4 interface inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy RAVPN internal
group-policy RAVPN attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ST1
address-pools value testpool
username dk password Z6zukyDvwVjP7o24 encrypted privilege 15
username sv password i1gRUVsEALixX3ei encrypted
tunnel-group testgroup type remote-access
tunnel-group testgroup general-attributes
address-pool testpool
default-group-policy RAVPN
tunnel-group testgroup ipsec-attributes
pre-shared-key *
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:48f0863a70b8f382c7b71db0b88620fe
: end
----
Could you please help me identifying where am I going wrong . Its been some long time I have trying to figure it out but nothing seems to work out ! ;-(
Please HELP !
Thanks ,
Anup
Anup
Solved! Go to Solution.
- Labels:
-
Remote Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2012 01:55 PM
1) Pls change the split tunnel ACL to standard ACL as follows:
no access-list ST1 extended permit ip 192.168.1.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list ST1 permit 192.168.1.0 255.255.255.0
2) Add icmp inspection:
policy-map global_policy
class inspection_default
inspect icmp
3) Lastly, add the following so you can ping the ASA inside interface:
management-access inside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2012 01:55 PM
1) Pls change the split tunnel ACL to standard ACL as follows:
no access-list ST1 extended permit ip 192.168.1.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list ST1 permit 192.168.1.0 255.255.255.0
2) Add icmp inspection:
policy-map global_policy
class inspection_default
inspect icmp
3) Lastly, add the following so you can ping the ASA inside interface:
management-access inside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2012 04:54 AM
Hi Jennifer ,
It worked ! Now I'm able to ping to ASA Inside interface after enabling ICMP inspection and setting management as inside. Thanks a ton ! :)
Standard ACL which defines the traffic to inside network is enough ? The destination does not matter ?
I'm not aware of any other inside IP addresses but since there is connectivity to ASA inside , we can be sure that the internal network is accessible , right ?
Sent from Cisco Technical Support Android App
Anup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2012 04:57 AM
Excellent, that is great news.
Yes, if you can access the ASA inside interface, most probably the inside network should work too.
Try to check the arp table on the ASA: sh arp, perhaps there is ip address that you can try to ping.
Sometimes you also have to be aware that some hosts have firewall on, that might prevent inbound access from different subnet, and by turning the firewall off, or adding rules on the host firewall to allow traffic from the vpn pool subnet, access will be successful.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

