- Cisco Community
- Technology and Support
- Security
- VPN
- Remote VPN not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Remote VPN not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2011 02:05 AM
Regards,
I have Cisco 1812 connected to ISP's router Cisco 870. Both routers have switch module and when I'm connected with PC to 870 I can connect via VPN to remote location.
When I'm connected to 1812 remote VPN doesn't work.
Client computers are connected to 1812 and they can surf on internet just fine.
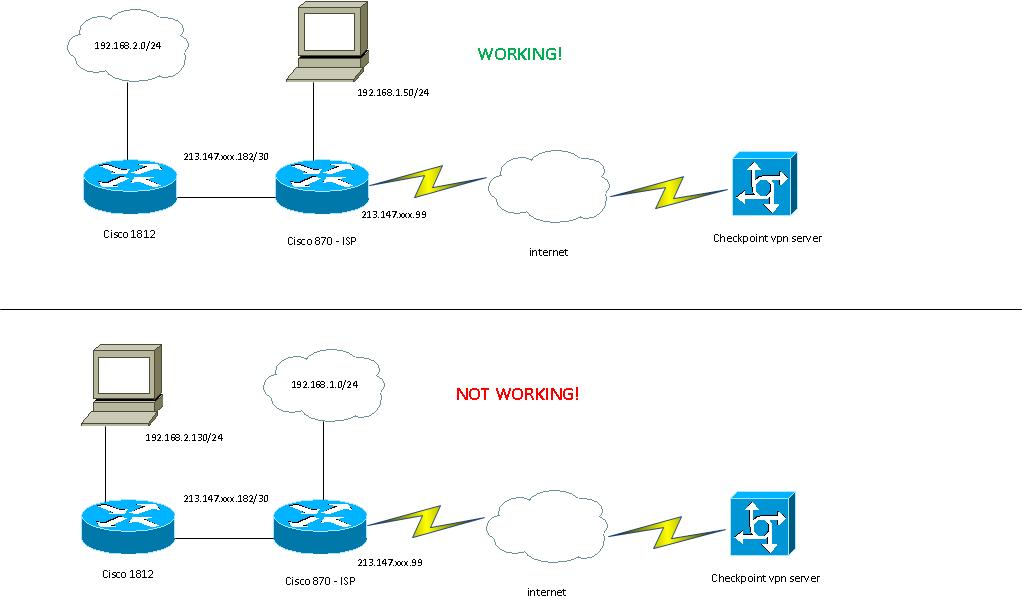
Cisco 870 DHCP scope is 192.168.1.0/24
Cisco 1812 DHCP scope is 192.168.2.0/24
Cisco 870 and Cisco 1812 are directly connected via
213.147.xxx.182/30 and address on outside interface od cisco 870 is 213.147.xxx.99.
I also have configured site2site VPN via 1812 which is working just fine.
I tried changing MTU but nothing helps
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2011 06:42 AM
I discovered that this is common nat problem. Cisco 1812 is configured with pat and site2site VPN...
here is my configuration:
ip dhcp excluded-address 192.168.2.1 192.168.2.99
ip dhcp excluded-address 192.168.2.200 192.168.2.254
!
ip dhcp pool company
network 192.168.2.0 255.255.255.0
dns-server 192.168.2.2
default-router 192.168.2.1
!
crypto isakmp policy 1
encr 3des
authentication pre-share
lifetime 28800
crypto isakmp key company-headquarters address 80.80.xxx.2 no-xauth
crypto isakmp nat keepalive 20
!
!
crypto ipsec transform-set SDM_TRANSFORMSET_1 esp-3des esp-sha-hmac
crypto ipsec transform-set Cisco esp-3des esp-sha-hmac
!
crypto map company-location1 1 ipsec-isakmp
set peer 80.80.xxx.2
set security-association lifetime seconds 28800
set transform-set SDM_TRANSFORMSET_1
set pfs group2
match address 100
!
!
interface FastEthernet0
ip address 213.147.xxx.182 255.255.255.252
ip nat outside
ip virtual-reassembly
no ip mroute-cache
duplex auto
speed auto
crypto map company-location1
!
interface FastEthernet1
no ip address
no ip mroute-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet2
!
interface FastEthernet9
!
interface Vlan1
ip address 192.168.2.1 255.255.255.0
no ip proxy-arp
ip nat inside
ip virtual-reassembly
!
ip route 0.0.0.0 0.0.0.0 213.147.xxx.181
!
!ip nat inside source route-map SDM_RMAP_1 interface FastEthernet0 overload
!
access-list 1 remark SDM_ACL Category=16
access-list 1 permit 192.168.2.0 0.0.0.255
access-list 98 permit 192.168.2.0 0.0.0.255
access-list 98 permit 80.80.xxx.0 0.0.0.63
access-list 100 remark SDM_ACL Category=4
access-list 100 permit ip 192.168.2.0 0.0.0.255 10.254.0.0 0.0.255.255
access-list 101 remark SDM_ACL Category=2
access-list 101 deny ip 192.168.2.0 0.0.0.255 10.254.0.0 0.0.255.255
access-list 101 permit ip 192.168.2.0 0.0.0.255 any
!
route-map SDM_RMAP_1 permit 1
match ip address 101
Does anyone has a solution or proposal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2011 10:44 AM
Are you running a VPN client on the PC, try making ACL 101 have a deny statement in the top that says:
deny source: client address dest: checkpoint firewall address
telling the router *not* to nat the traffic when your client initiates a connection to the checkpoint gateway, letting your 871 handle it as needed.
Do you have the config of the 871?
HTH
Jason
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 12:45 AM
871 is ISP's router and I have no access to it.
hm, that makes sense.
I changed my access list from:
access-list 101 deny ip 192.168.2.0 0.0.0.255 10.254.0.0 0.0.255.255
access-list 101 permit ip 192.168.2.0 0.0.0.255 any
to:
access-list 101 deny ip 192.168.2.0 0.0.0.255 host 194.152.xxx.2
access-list 101 deny ip 192.168.2.0 0.0.0.255 10.254.0.0 0.0.255.255
access-list 101 permit ip 192.168.2.0 0.0.0.255 any
now, my VPN client gets blocked by access-list? vpn client output:
Checking network connectivity...
Preparing connection...
Connecting to gateway...
Gateway not responding
Connection failed
is something wrong in my ACL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 04:06 AM
I managed to get ISP's configuration from 871
version 12.4
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime year
service timestamps log datetime msec localtime year
service password-encryption
!
no ip source-route
ip arp proxy disable
ip cef
!
!
no ip dhcp use vrf connected
no ip dhcp conflict logging
!
ip dhcp pool PC
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
dns-server 213.147.xxx.51 213.147.xxx.52
lease 7
!
!
no ip domain lookup
ip domain name ISP
!
!
interface Loopback1500
ip address 213.147.xxx.99 255.255.255.255
!
interface FastEthernet0
switchport access vlan 100
!
interface FastEthernet2
switchport access vlan 200
!
interface FastEthernet3
switchport access vlan 100
!
!
interface FastEthernet4.1500
description Internet
encapsulation dot1Q 1500
ip address x.y.w.z 255.255.240.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip virtual-reassembly
rate-limit input 4000000 750000 1500000 conform-action transmit exceed-action drop
service-policy output SHAPE
!
interface Vlan1
no ip address
shutdown
!
interface Vlan100
ip address 192.168.1.1 255.255.255.0
no ip redirects
no ip unreachables
ip nat inside
ip virtual-reassembly
no snmp trap link-status
!
interface Vlan200
description Site to site VPN
ip address 213.147.xxx.181 255.255.255.252
no ip redirects
no ip unreachables
ip nat inside
ip virtual-reassembly
no snmp trap link-status
!
ip route 0.0.0.0 0.0.0.0 x.y.w.z
.......
!
!
access-list 10 permit 192.168.1.0 0.0.0.255
access-list 88 permit x
access-list 88 deny any
access-list 100 permit ip host x any
access-list 100 permit ip host x any
access-list 100 permit ip x any
access-list 100 deny ip any any log
!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide