Hi everyone:
I configured an Windows Server 2008 as an VPN L2TP server, now I'm trying to configure the necessary rules over an Cisco Router 2901/k9 so WAN VPN request goes directly to Windows Server behind it. But I'm struggling. This router has an old configuration from when it was acting as an VPN server that I think is messing with me.
This is the diagram:
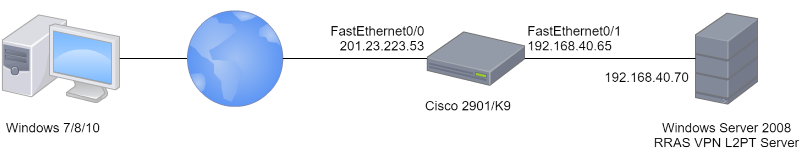
In the router I configured the IP NAT rules, the access-list for the WAN interface and the inspect rules. The Windows Server is correctly configured because in LAN works. But when I tried to connect to the VPN server (Windows) from Internet is the router who is trying to resolve the request and act as an VPN server.
Here goes the sh run
|
RTR-01#
RTR-01#show run
Building configuration...
Current configuration : 9585 bytes
!
! Last configuration change at 23:24:29 VET Thu Jun 8 2017 by latam
version 15.1
service timestamps debug datetime localtime
service timestamps log datetime localtime
service password-encryption
!
hostname RTR-01
!
boot-start-marker
boot system flash:c2800nm-advipservicesk9-mz.151-4.M6.bin
boot-end-marker
!
!
card type e1 0 1
no logging queue-limit
logging buffered 2000000
no logging rate-limit
enable secret 4 FiDVXZ00ZOmF7xG57wfDNoAq4RcQVu6m.HpjfaDIK.c
!
aaa new-model
!
!
aaa group server radius RadiusISE
server 15.20.80.55 auth-port 1812 acct-port 1813
server 15.20.80.56 auth-port 1812 acct-port 1813
!
aaa authentication login console group RadiusISE local
aaa authentication ppp default local
aaa authentication dot1x default group RadiusISE
aaa authorization console
aaa authorization exec telnet group RadiusISE local
aaa authorization network default group RadiusISE
aaa accounting exec shell
action-type start-stop
group RadiusISE
!
aaa accounting network default
action-type start-stop
group RadiusISE
!
!
!
!
!
!
aaa session-id common
!
clock timezone VET -4 30
no network-clock-participate wic 1
!
dot11 syslog
ip source-route
!
!
ip cef
ip dhcp excluded-address 192.168.40.65
ip dhcp excluded-address 192.168.40.66 192.168.40.80
ip dhcp excluded-address 192.168.40.87
!
ip dhcp pool LAN
network 192.168.40.64 255.255.255.192
default-router 192.168.40.65
dns-server 192.168.40.69 208.67.222.222 208.67.222.220
netbios-name-server 192.168.40.69
!
!
!
ip flow-cache timeout active 1
ip domain name ctnet.com
ip name-server 192.168.40.71
ip inspect tcp reassembly queue length 640
ip inspect tcp reassembly timeout 30
ip inspect name FW http
ip inspect name FW https
ip inspect name FW dns
ip inspect name FW ftp
ip inspect name FW imap
ip inspect name FW imaps
ip inspect name FW fragment maximum 256 timeout 1
ip inspect name FW rcmd
ip inspect name FW streamworks
ip inspect name FW tftp
ip inspect name FW vdolive
ip inspect name FW smtp
ip inspect name FW snmp
ip inspect name FW rtsp
ip inspect name FW icmp
ip inspect name FW ssh
ip inspect name FW ica
ip inspect name FW icabrowser
ip inspect name FW telnet
ip inspect name FW citrix
ip inspect name FW udp
ip inspect name FW tcp
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
voice-card 0
!
crypto pki token default removal timeout 0
!
!
!
!
license udi pid CISCO2811 sn FTX0937A44X
archive
log config
hidekeys
username admin privilege 15 password 7 Cisco
username LATAM privilege 15 password 7 Cisco
username rovando privilege 15 password 7 Cisco
!
redundancy
!
!
controller E1 0/1/0
channel-group 0 unframed
!
!
track 1 ip sla 1 reachability
delay up 2
!
class-map match-any ENHANCED
match ip dscp af31 af41
match protocol telnet
match protocol ssh
match protocol citrix
match protocol tftp
match protocol skinny
match protocol h323
match protocol rtp video
match protocol rtsp
match protocol icmp
match access-group name ENHANCED1
class-map match-any VOIP-BEARER
match ip dscp ef
match protocol rtp audio
class-map match-any VOIP-SIGNAL
match ip dscp cs3
match access-group name VOIP-SIGNAL1
!
!
policy-map QOS-WAN
class VOIP-BEARER
priority 384
set dscp ef
class VOIP-SIGNAL
bandwidth 128
set dscp cs3
class ENHANCED
bandwidth 384
set dscp af31
random-detect dscp-based
class class-default
fair-queue
random-detect
policy-map SHAPE-MPLS
class class-default
shape average 2000000
service-policy QOS-WAN
policy-map SHAPE-TUNNEL
class class-default
shape average 1000000
service-policy QOS-WAN
!
!
!
crypto isakmp policy 2
encr aes 256
authentication pre-share
group 2
crypto isakmp key CiscoKey address 0.0.0.0 0.0.0.0
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 20
!
!
crypto ipsec transform-set DMVPN-SET esp-aes 256 esp-sha-hmac
mode transport
!
crypto ipsec profile DMVPN-PROF
set transform-set DMVPN-SET
!
!
!
!
!
!
interface Loopback50
no ip address
!
interface Tunnel2
description DMVPN to CLE
bandwidth 1000
ip address 172.16.96.41 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication Tr1umph
ip nhrp group 4MB-SPOKE
ip nhrp map multicast 66.181.70.3
ip nhrp map 172.16.96.1 66.181.70.3
ip nhrp network-id 96
ip nhrp holdtime 300
ip nhrp nhs 172.16.96.1
ip tcp adjust-mss 1360
delay 2000
shutdown
qos pre-classify
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 200
tunnel protection ipsec profile DMVPN-PROF
!
interface FastEthernet0/0
description Caracas Internet
ip address 201.23.223.53 255.255.255.252
ip access-group FW-IN in
ip nbar protocol-discovery
ip flow ingress
ip flow egress
ip nat outside
ip inspect FW out
ip virtual-reassembly in
load-interval 60
duplex auto
speed auto
service-policy output SHAPE-TUNNEL
!
interface FastEthernet0/1
description LAN
ip address 192.168.40.65 255.255.255.192
ip flow ingress
ip flow egress
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
!
interface Serial0/0/0
description Caracas Internet
no ip address
ip access-group FW-IN in
ip nbar protocol-discovery
ip flow ingress
ip flow egress
ip nat outside
ip inspect FW out
ip virtual-reassembly in
load-interval 60
shutdown
service-policy output SHAPE-TUNNEL
!
interface Serial0/0/1
no ip address
shutdown
clock rate 2000000
!
interface Serial0/1/0:0
description Level 3 FRO2005122412VRP
ip address 172.16.99.30 255.255.255.252
ip nbar protocol-discovery
load-interval 60
shutdown
service-policy output SHAPE-MPLS
!
!
router eigrp 2000
network 172.16.96.0 0.0.0.255
network 192.168.40.64 0.0.0.63
no eigrp log-neighbor-changes
!
router bgp 65100
bgp log-neighbor-changes
bgp bestpath cost-community ignore
bgp suppress-inactive
network 172.16.99.28 mask 255.255.255.252
network 192.168.40.64 mask 255.255.255.192
neighbor 172.16.99.29 remote-as 3549
neighbor 172.16.99.29 allowas-in
neighbor 172.16.99.29 soft-reconfiguration inbound
!
ip default-gateway 200.75.128.81
ip forward-protocol nd
ip http server
no ip http secure-server
!
ip flow-export source FastEthernet0/1
ip flow-export version 5
ip flow-export destination 15.20.80.101 2055
ip flow-top-talkers
top 20
sort-by bytes
!
ip nat pool POOL 201.23.223.53 201.23.223.53 netmask 255.255.255.252
ip nat inside source list 187 pool POOL overload
ip nat inside source static tcp 192.168.40.70 21 interface FastEthernet0/0 58426
ip nat inside source static tcp 192.168.40.70 445 interface FastEthernet0/0 448
ip route 0.0.0.0 0.0.0.0 200.75.128.81 track 1
!
ip access-list extended FW-IN
permit ip host 66.181.70.2 any
permit tcp any any eq ftp
permit tcp any any eq 445
permit udp any any eq isakmp
permit udp any any eq non500-isakmp
permit ahp any any
permit esp any any
permit gre any any
permit icmp any any echo-reply
permit icmp any any packet-too-big
permit icmp any any traceroute
permit icmp any any information-reply
permit udp any any eq bootpc
permit icmp any any ttl-exceeded
permit icmp any any port-unreachable
deny ip any any
ip access-list extended VOIP-SIGNAL1
permit tcp any any eq 1720
permit tcp any any range 2000 2002
permit udp any any eq 1719
permit udp any any eq 5060
ip access-list extended vty_access_limit
permit ip 192.168.0.0 0.0.255.255 any
permit ip 10.0.0.0 0.255.255.255 any
permit ip 172.16.0.0 0.0.255.255 any
permit ip host 66.181.70.2 any
permit ip host 12.196.4.34 any
deny ip any any
!
ip radius source-interface FastEthernet0/1
ip sla 1
icmp-echo 200.75.128.81 source-ip 201.23.223.53
ip sla schedule 1 life forever start-time now
logging history informational
logging trap debugging
logging source-interface FastEthernet0/1
logging 15.20.80.101
access-list 187 deny ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255
access-list 187 deny ip 10.0.0.0 0.0.0.255 any
access-list 187 permit ip 192.168.40.64 0.0.0.63 any
!
!
!
!
snmp-server community network~elites1 RO
snmp-server ifindex persist
snmp-server trap-source FastEthernet0/1
snmp-server location Caracas, VE
snmp-server contact Leon Mantle
snmp-server enable traps tty
snmp-server enable traps eigrp
snmp-server enable traps envmon
snmp-server enable traps isdn call-information
snmp-server enable traps isdn layer2
snmp-server enable traps isdn chan-not-avail
snmp-server enable traps isdn ietf
snmp-server enable traps bgp
snmp-server enable traps config
snmp-server enable traps ipsla
snmp-server enable traps srst
snmp-server enable traps voice high-ds0-util
snmp-server host 15.20.80.101 network~elites1
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server dead-criteria time 30 tries 3
radius-server host 10.2.100.97
radius-server host 15.20.80.55 auth-port 1812 acct-port 1813
radius-server host 15.20.80.56 auth-port 1812 acct-port 1813
radius-server retransmit 2
radius-server timeout 10
radius-server deadtime 2
radius-server key 7 0519260B70591B
radius-server vsa send accounting
radius-server vsa send authentication
!
!
!
control-plane
!
!
!
mgcp fax t38 ecm
!
mgcp profile default
!
!
!
!
!
alias exec top show ip eigrp topo
!
line con 0
exec-timeout 20 0
password 7 Cisco
line aux 0
line vty 0 4
access-class vty_access_limit in
exec-timeout 20 0
privilege level 15
transport input all
transport output all
line vty 5 15
access-class vty_access_limit in
exec-timeout 20 0
privilege level 15
transport input ssh
!
scheduler allocate 20000 1000
ntp server 15.20.80.8
end
RTR-01#
RTR-01#
RTR-01#
RTR-01#
RTR-01#
RTR-01#
|
Could you please help to check what do I need to remove or change so this works? I looked over the internet but I just had found tutorials to create a new VPN using diverse protocols but no one to remove it.
Notes:
1. Obviously the external IPs and password were changed or omitted.
2. Why use the windows server and VPN server and not the Cisco router? Because, as you can see, I don't have so much experience with Cisco.
Thank you.
Best regards.
