- Cisco Community
- Technology and Support
- Security
- VPN
- S2S VPN in Cisco FTD managed by FMC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
S2S VPN in Cisco FTD managed by FMC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 12:42 AM
Hi,
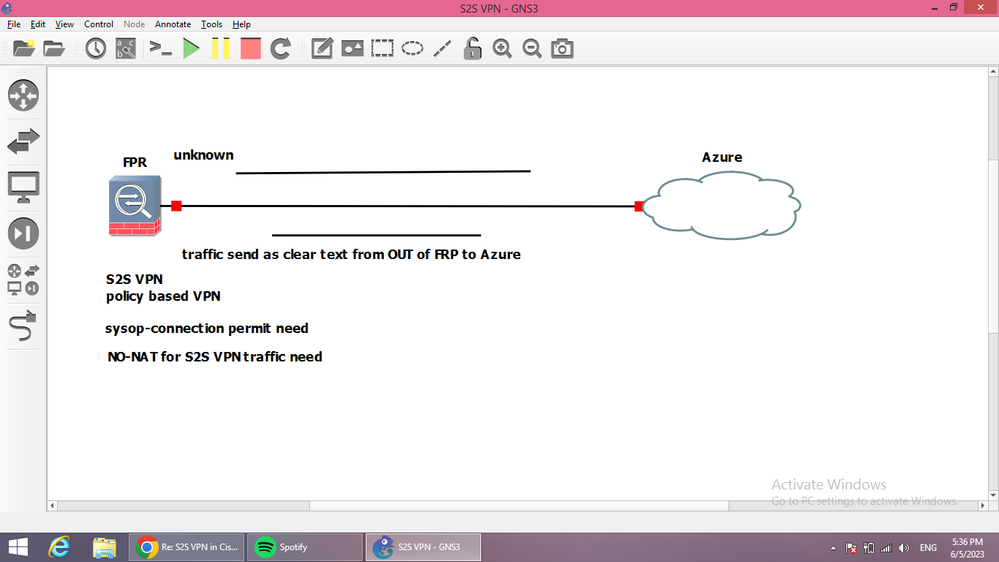
Trying to establish a S2S VPN connection from FTD to Azure. The connection is up and the encrypted and decrypted packet count keeps increasing, but the Azure side is not receiving traffic. Packet trace shows its hitting the IPSec ACL and hitting the right NAT exempt rule. Packet capture on the inside interface shows the traffic coming in from Azure side and return traffic from the protected server address. The only weird thing is when doing a packet capture on the outside interface I can see interesting traffic being sent on the outside interface with Azure side destination address and Outside interface as the source. Should I be seeing that if the traffic is going through the tunnel?
Thanks
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 01:00 AM
encrypt <<- meaning your traffic is pass the interface you config crypto map under it
decrypt <<- meaning your FTD success receive the traffic from Azure and IPsec success handle these traffic
are you see both encrypt and decrypt under same IPsec SA ? i.e. under the same IPsec toward remote Peer Azure are you see encrypt and decrypt count increase ?
if Yes
then check if there is FW Infront of your FTD that drop the packet
if NO
check if the traffic gone to wrong Peer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 01:41 AM
Hi MHM,
I am seeing encrypt and decrypt under the correct IPSec SA and there is no firewall past the FTD.
Should I be seeing traffic originating from the outside Interface to the Azure server that is meant to be encrypted? I have never checked it before but I would think that I should not be able to see it if it’s getting encrypted.
thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 02:06 AM
even if it encrypt it use UDP/500 or UDP/4500
what inside packet no matter we need to full check that traffic go out form OUTside to Azure
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 03:22 AM
I am seeing tcp/80, tcp/8080 and ICMP traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 05:46 AM
you capture in FTD side or the Azure side?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 06:48 AM
On the FTD side. Packet capture on the outside interface shows traffic from with the VPN gateway address as the source and the destination address as azure side protected server address
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 07:38 AM - edited 06-05-2023 09:22 AM
can you confirm the above
can I see show crypto ipsec sa ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide