- Cisco Community
- Technology and Support
- Security
- VPN
- Site to Site Tunnel Access Vendor print to Customer Printer tcp\9100
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 05:45 AM
What are the specifics necessary for Vendor Site to Site tunnel access to print to customer printer through the customer's ASA.
For example VendorA 10.10.20.10 needs to send reports over Tcp\9100 through customer ASA to internal system 192.168.5.10 whish is a printer
VPN Is already confirmed established. NAT is defined for the tunnel as follows
Inside Source Interface Inside 192.168.5.10 Destination Interface Any Vendor Destination 10.10.20.10 Service Any
Disable Proxy Arp Lookup Route
With the above NAT in place and Tunnel up what is necessary for Outside ACL & Inside ACL to allow Vendor 10.10.20.10 to initiate and send reports to Inside printer 192.168.5.10 over tcp\9100
I want to ensure I am not adding unneeded entries to my ACL's. Since the VPN is established do you even need an ACL on the Outside interface stating source 10.10.20.10 192.168.5.10 TCP\9100
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 09:50 AM
""I remember site to site tunnels usually being NAT Exempt. I don't recall ever where a S2S needed to be translated. I am now curious why one need this.""
L2L (S2S) not need NAT exempt except the case you have run NAT in interface you run crypto map under it.
why we need NAT for S2S one case is overlapping in both side of VPN peers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 10:05 AM
@keithcclark71 if you have a Dynamic NAT/PAT rule configured you'd likely need a NAT exemption rule to ensure the VPN traffic is not unintentially translated.
Run packet-tracer from the CLI to determine what NAT rules traffic matches.
Which side initiates the traffic, inside or outside?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 05:49 AM - edited 12-27-2022 05:50 AM
Hi @keithcclark71 do you actually need NAT to translate traffic or a NAT exemption rule to ensure traffic is not unintentially translated?
Normally on the ASA VPN traffic usually bypasses the interface ACL, so all VPN traffic would be allowed. If you wish to restrict this traffic you may want to look at using a VPN Filter, to restrict just this traffic. https://www.cisco.com/c/en/us/support/docs/security/pix-500-series-security-appliances/99103-pix-asa-vpn-filter.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 09:44 AM - edited 12-27-2022 09:49 AM
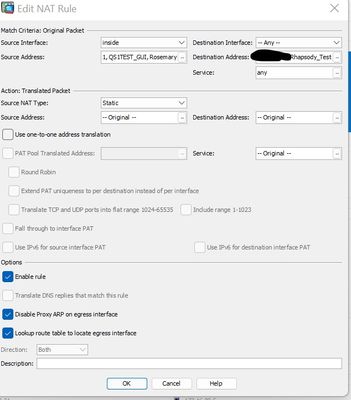
Hey Rob in older ASA ASDM it showed NAT Exempt but in latest ASDM that I am looking at on this particular ASA there is no longer NAT Exempt listings. I believe the screenshot shows NAT Exempt because source address says original and destination address says original ? Would that be accurate?
I remember site to site tunnels usually being NAT Exempt. I don't recall ever where a S2S needed to be translated. I am now curious why one need this.
The below NAT is based upon established VPN where source address is accessed by destination addressed network objects. Therefore no Outside ACL entry necessary??? If I am restricting outbound traffic from the inside interface then would I need an ACL entry for the inside interface specifying an allow for the source address objects to access the destination objects or would I write that entry in reverse so that the destination address objects are specified as source on the inside interface and destination address object would be the source object?
Ex: Inside interface Source Rhapsody_Test permit Destination QS1Test_GUI , Rosemary or should it be
Ex: Inside interface Source QS1Test_GUI , Rosemary permit Destination Rhapsody_Test
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 09:50 AM
""I remember site to site tunnels usually being NAT Exempt. I don't recall ever where a S2S needed to be translated. I am now curious why one need this.""
L2L (S2S) not need NAT exempt except the case you have run NAT in interface you run crypto map under it.
why we need NAT for S2S one case is overlapping in both side of VPN peers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 10:05 AM
@keithcclark71 if you have a Dynamic NAT/PAT rule configured you'd likely need a NAT exemption rule to ensure the VPN traffic is not unintentially translated.
Run packet-tracer from the CLI to determine what NAT rules traffic matches.
Which side initiates the traffic, inside or outside?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 05:50 AM - edited 12-27-2022 05:52 AM
for VPN the traffic is permit by default no need ACL if you run ASA FW.
traffic allow from OUT-to-IN
if you have ACL in INside with direction IN then you need ACL to allow traffic.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide