- Cisco Community
- Technology and Support
- Security
- VPN
- Site to Site VPN help!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site to Site VPN help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2011 09:20 PM
Hi,
I have been working on this for a couple days now and need some help.
I have a site to site VPN using two Cisco 2901 Routers. Example below. (IP's have been modified).
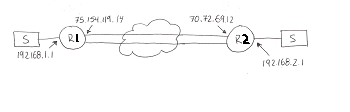
Cisco CCP verify's that I have an active vpn connection. I can ping from a client PC on R2 (192.168.2.21) to the internal address on R1 192.168.1.1
I can't ping any other address on the .1. side. (i.e. 192.168.1.2 - Server, 192.168.1.3 - WAP)
I can't ping anything on the .2. network from a client on .1 side.
I checked both routers and they are identical.
Seems like possibly a acl problem but I'm stumped.
I attached both configurations. (IP's modified). Both routers also have a VPN-Client setup but I don't believe that should affect it.
Let me know if you need any show crytos
Thanks
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2011 11:18 AM
Config looks fine. Can you try by changing the EZVPN pool IPs to different subnet than internal subnets? As a rule of thumb it is always recomended to use Remote Access pool diff from the internal subnet.
Thx
MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2011 11:35 AM
Thanks mvsheik123 for responding!
The EZVPN pool is part of the Client->Server VPN which works perfectly.
The site to site vpn which i'm having problems with uses: crypto isakmp policy 9.
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2011 01:02 PM
Yeap. It works. Based on the your initial posting, it appears to be some kind of routing issue than VPN, unless I miss something. The reason I asked you to change the EZVPN pool - when users connected to EZVPN (ex: site 192.168.1.x) and assigned with one of the pool IP, that may be popping up in your routing table as entire subnet and router may be
send the traffic to outside interface again. So first check the routing table.
Thx
MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2011 02:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2011 10:06 AM
Hi Chris,
The routing table looks fine (inside subnet Vs EZVPN ips). Have you tried debug icmp and see where the packets being dropped? Also you post 'show crypto isakmp sa' and show crypto ipsec sa (after ping remote PC).?
Thx
MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2011 02:42 PM
Hi mvsheik123,
Thanks for your continued support. It is much appreciated.
I have attached the show crypto isakmp sa, and show crypto ipsec sa outputs for both routers.
I have noticed that the ipsec sa on R2 shows a few send errors, but everything else seems good.
Also on R1 show crypot isakmp sa the source and destination seem to be opposite, not sure if that's correct. R2 seems correct.
Thanks again.
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2011 06:21 PM
No problem.Try to clear and reestablish tunnel. Also, try debug icmp. There are debug commands relates to ipsec as well, but lets try this first.
thx
MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 06:13 PM
I have enabled, debug ip icmp on both routers.
When i try to ping the one interface i can it pops up with echo reply sent, src, dst, dscp 0 topoid 0. Like it should.
When i try to ping an interface or ip I currently cant I get nothing on the debug.
How can i clear and re establish the tunnel?
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2011 07:24 PM
I guess on routers you can use : clear crypto isakmp (id) to clear the connection.
Also, check the link below for further t-shoot..
http://www.cisco.com/en/US/partner/tech/tk583/tk372/technologies_tech_note09186a00800949c5.shtml
Thx
MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 10:19 AM
Hi,
That command worked to reset tunnel. I also used the GUI to clear the tunnel and re establish it.
The tunnel seems to come up successfully each time.
I have used a few debug commands after going through the link you sent, but I have seen nothing out of the ordinary. No errors or anything.
debug crypto ipsec
debug crypto isakmp sa
debug crypto isakmp engine
Does it matter if my tunnel interfaces are dhcp and not static at the moment? would this affect it?
Thanks
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 12:50 PM
Oh..ok.. I guess you need to use dyn DNS or check this below discussion. This might help you.
https://supportforums.cisco.com/thread/343363
Thx
MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 10:40 PM
it should not be a dns issue, as it is configured with ip addresses on both ends.
***********************************************
R1 - config
crypto map 123map 10 ipsec-isakmp
set peer 70.72.69.12
set transform-set MYSET
match address 101
***********************************************
R2 - config
crypto map map123 10 ipsec-isakmp
set peer 75.154.119.14
set transform-set MYSET
match address 101
furthermore, the isakmp works (from the results of show crypto isakmp sa)
have you verify the "show crypto ipsec sa"?
if the ipsec tunnels are not up, maybe you can try to the following steps.
1-clear all tunnels and statistics/counters
2-run debug crypto isakmp ,debug crypto ipsec on both ends. (since isakmp works, you may leave it out of debug logs)
3-ping from one end to the other end
4-no debug all
5-show crypto isakmp sa, show crypto ipsec sa
[not sure if i get all the commands correct]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2011 02:38 PM
HI guys, sorry for the delay I have been busy.
I checked out the link above which brought me to: http://www.networkstraining.com/site-to-site-vpn-with-dynamic-crypto-map/
According to this site it looks like i'm missing "reverse-route" in my crypto map, I haven't seen this command before but i added it anyways to see if it would help on both routers. Any experience with this command?
crypto map map123 10 ipsec-isakmp
set peer 70.72.69.12
set transform-set MYSET
match address 101
reverse-route
crypto map map123 10 ipsec-isakmp
set peer 75.154.119.14
set transform-set MYSET
match address 101
reverse-route
I then cleared the connection and brought up the tunnel.
I can now ping from all 192.168.2.0 clients to all clients on 192.168.1.0. YA!!!!!!
I can now ping from 192.168.1.0 clients to most clients on 192.168.2.0.
A couple things that are still bothering me:
1.) I can only bring up the tunnel from 192.168.2.0 client side
If i try to bring it up by pinging 192.168.2.1 from 192.168.1.2 i get request timed out.
If i try to bring it up by pinging 192.168.1.1 from 192.168.2.23 or 192.168.2.22 it works and establishes the tunnel.
2.) There are a couple addresses on the 192.168.2.0 network that I cannot ping from 192.168.2.1. Specifically Windows 7 laptops x2.
When I run a tracert i get: 004301: *Nov 24 16:23:56.140 MDT: ICMP: time exceeded (time to live) sent to 192.168.1.2 (dest was 192.168.2.24), topology BASE, dscp 0 topoid 0
I can however reverse the ping successfully from 192.168.2.24 to 192.168.1.2. Strange?
3.) show crypto ipsec sa looks great on R1
show crypto ipsec sa is still getting a couple send errors on R2.
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
75.154.119.14 70.72.69.12 QM_IDLE 1025 ACTIVE
R2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
75.154.119.14 70.72.69.12 QM_IDLE 1001 ACTIVE
R2#show crypto ipsec sa
interface: GigabitEthernet0/1
Crypto map tag: map123, local addr 70.72.69.12
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
current_peer 75.154.119.14 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 223, #pkts encrypt: 223, #pkts digest: 223
#pkts decaps: 369, #pkts decrypt: 369, #pkts verify: 369
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 3, #recv errors 0
local crypto endpt.: 70.72.69.12, remote crypto endpt.: 75.154.119.14
path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/1
current outbound spi: 0x82108171(2182119793)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xE826C8CF(3894855887)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: Onboard VPN:5, sibling_flags 80000046, crypto map: map123
sa timing: remaining key lifetime (k/sec): (4519167/85613)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x82108171(2182119793)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2006, flow_id: Onboard VPN:6, sibling_flags 80000046, crypto map: map123
sa timing: remaining key lifetime (k/sec): (4519138/85613)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
Thanks again!
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2011 05:02 PM
bump!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide