- Cisco Community
- Technology and Support
- Security
- VPN
- Site2Site Tunnel issue PSEC(epa_des_crypt): decrypted packet failed SA identity check
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site2Site Tunnel issue PSEC(epa_des_crypt): decrypted packet failed SA identity check
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2013 04:16 AM
Hi,
I have a slight issue I'm having some problems resolving..
The scenario is as follows;
I have an external provider which connects to me via VPN to a Juniper SSG firewall, that works fine.
I then have an external site, which does NOT reside in my MPLS cloud, so I have to deploy IPSec via Internet to reach it.
That also works fine and I have multiple SA's running on that site with no issues or problems.
The external provider has a small network device deployed on the external site which monitor cooling values in one of our warehouses.
The external site which is connect via IPSEC has a Cisco 1921 and a numerous Cisco 3550 deployed.
The VLAN for the cooling provider is vlan 150 and is setup with 10.150.4.0/24 where .1 is the def gw and .10 is the cooling monitor device.
The external provider's servers are located within 192.168.220.0/24 subnet.
As of right now, we can reach the Cisco 1921 through the whole IPsec tunnel from 192.168.220.182 with all services, ping, telnet whatnot, but we are unable to ping the cooling device from 192.168.220.0/24.
However from the Cisco 1921, we can ping both 192.168.220.0/24 and the locally connected 10.150.4.10
So basicly it seems to be the last bit when the traffic goes through the 1921 and to the switch where it fails and I can't for the life of me figure out why.
Network diagram attached.. any ideas?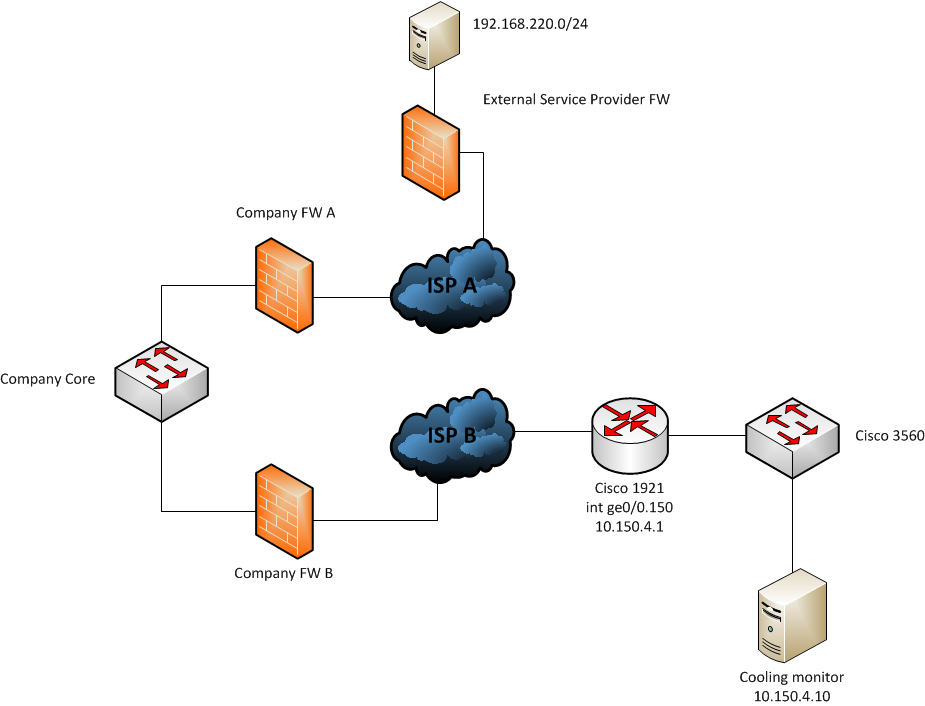
This is the 1921 config:
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime
service timestamps log datetime msec localtime
service password-encryption
!
hostname bergen-vpn-gw
!
boot-start-marker
boot system flash flash:c1841-adventerprisek9-mz.124-25d.bin
boot-end-marker
!
logging buffered 50000
!
aaa new-model
!
!
aaa authentication login default local
aaa authentication enable default enable
!
!
!
!
!
aaa session-id common
!
!
!
clock timezone CET 1
clock summer-time CET recurring last Sun Mar 2:00 last Sun Oct 3:00
!
no ipv6 cef
no ip source-route
ip cef
no ip bootp server
no ip domain lookup
ip domain name xxxxx
!
multilink bundle-name authenticated
!
!
!
license udi pid CISCO1921/K9 sn FCZ1508C1P4
license boot module c1900 technology-package securityk9
license boot module c1900 technology-package datak9
!
!
vtp mode client
!
redundancy
!
!
!
!
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
crypto isakmp key harakiri address 1.2.3.4
!
!
crypto ipsec transform-set 3DES-SHA esp-3des esp-sha-hmac
!
crypto map VPN 10 ipsec-isakmp
set peer 1.2.3.4
set transform-set 3DES-SHA
match address VPN
!
!
!
!
!
interface GigabitEthernet0/0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
no ip route-cache cef
no ip route-cache
duplex auto
speed auto
!
!
interface GigabitEthernet0/0.99
description *** Test VLAN To be removed ***
encapsulation dot1Q 99
ip address 10.90.90.1 255.255.255.0
no ip route-cache
!
interface GigabitEthernet0/0.112
encapsulation dot1Q 112
ip address 192.168.112.1 255.255.255.0
ip helper-address 172.30.1.223
no ip route-cache
!
interface GigabitEthernet0/0.150
encapsulation dot1Q 150
ip address 10.150.4.1 255.255.255.0
no ip redirects
no ip proxy-arp
no ip route-cache
!
interface GigabitEthernet0/0.178
encapsulation dot1Q 178
ip address 192.168.178.1 255.255.255.0
ip helper-address 172.30.1.223
no ip redirects
no ip proxy-arp
no ip route-cache
!
interface GigabitEthernet0/0.999
encapsulation dot1Q 999
no ip route-cache
!
interface GigabitEthernet0/1
ip address 1.2.3.4 255.255.255.252
no ip redirects
no ip proxy-arp
!
no ip route-cache cef
no ip route-cache
duplex auto
speed auto
crypto map VPN
!
!
interface FastEthernet0/0/0
switchport access vlan 99
!
!
interface FastEthernet0/0/1
!
!
interface FastEthernet0/0/2
!
!
interface FastEthernet0/0/3
!
!
interface Vlan1
no ip address
!
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 85.200.203.29
!
ip access-list extended VPN
permit ip 10.90.90.0 0.0.0.255 172.30.1.0 0.0.0.255
permit ip 10.90.90.0 0.0.0.255 172.22.0.0 0.0.255.255
permit ip 10.90.90.0 0.0.0.255 172.18.5.0 0.0.0.255
permit ip 10.90.90.0 0.0.0.255 10.50.0.0 0.0.255.255
permit ip 192.168.112.0 0.0.0.255 172.30.1.0 0.0.0.255
permit ip 192.168.112.0 0.0.0.255 172.22.0.0 0.0.255.255
permit ip 192.168.112.0 0.0.0.255 172.18.5.0 0.0.0.255
permit ip 192.168.112.0 0.0.0.255 10.50.0.0 0.0.255.255
permit ip 192.168.178.0 0.0.0.255 172.30.1.0 0.0.0.255
permit ip 192.168.178.0 0.0.0.255 172.22.0.0 0.0.255.255
permit ip 192.168.178.0 0.0.0.255 172.18.5.0 0.0.0.255
permit ip 192.168.178.0 0.0.0.255 10.50.0.0 0.0.255.255
permit ip 192.168.112.0 0.0.0.255 172.30.240.0 0.0.0.255
permit ip 192.168.178.0 0.0.0.255 172.30.240.0 0.0.0.255
permit ip 192.168.112.0 0.0.0.255 10.70.0.0 0.0.0.255
permit ip 192.168.178.0 0.0.0.255 10.70.0.0 0.0.0.255
permit ip 10.150.4.0 0.0.0.255 192.168.220.0 0.0.0.255 log
!
ip sla 1
icmp-echo 172.30.1.223 source-interface GigabitEthernet0/0.178
threshold 20
frequency 120
ip sla schedule 1 start-time now
ip sla 2
icmp-echo 10.50.1.200 source-interface GigabitEthernet0/0.178
threshold 20
frequency 120
ip sla schedule 2 start-time now
ip sla 3
icmp-echo 172.18.5.121 source-interface GigabitEthernet0/0.178
threshold 20
frequency 120
ip sla schedule 3 start-time now
ip sla 4
icmp-echo 172.22.0.140 source-interface GigabitEthernet0/0.178
threshold 20
frequency 120
ip sla schedule 4 start-time now
ip sla 5
icmp-echo 172.30.240.40 source-interface GigabitEthernet0/0.178
threshold 20
frequency 120
ip sla schedule 5 start-time now
ip sla 6
icmp-echo 10.70.0.200 source-interface GigabitEthernet0/0.178
threshold 20
frequency 120
ip sla schedule 6 start-time now
!
cdp source-interface GigabitEthernet0/0.112
!
!
!
!
snmp-server community bamacomro RO
cdp source-interface GigabitEthernet0/0.112
!
!
!
!
snmp-server community bamacomro RO
snmp-server community bamacomrw RW
!
control-plane
!
!
banner motd ^CCC-----------------------------------------------------------------------------
This system is solely for the use of authorised users for official purposes.
You have no expectation of privacy in its use and to ensure that the system
is functioning properly, individuals using this computer system are subject
to having all their activities monitored and recorded by system personell.
Use of this system evidence an express consent to such monitoring and
agreement that if such monitoring reveals evidence of possible abuse or
criminal activity, system personell may provide the result of such
monitoring to appropiate officials.
-----------------------------------------------------------------------------^C
!
line con 0
exec-timeout 5 0
logging synchronous
line aux 0
line vty 0 4
access-class telnet in
exec-timeout 180 0
logging synchronous
transport input telnet ssh
line vty 5 15
access-class telnet in
exec-timeout 180 0
password 7 094F471A1A0A
logging synchronous
transport input telnet ssh
!
scheduler allocate 20000 1000
end
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2013 01:09 PM
Please add static Routes for VPN ACL Destination IP. Hope it will work.
*** Do Rate Helpful Posts***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2013 05:57 PM
Hi Jawad,
I'm afraid you'll have to give me an example of what you are taking about there, I didn't quiet get that.
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2013 12:29 AM
I had that issue 1 year go
"decrypted packet failed SA identity check" means that we have decrypted a traffic that does not match the proxy ID negotiated
Juniper is violating RFC4301. there is nothing we can do against RFC violation
As mentioned in Section 4.4.1, "The Security Policy Database (SPD)",
the SPD (or associated caches) MUST be consulted during the
processing of all traffic that crosses the IPsec protection boundary,
including IPsec management traffic. If no policy is found in the SPD
that matches a packet (for either inbound or outbound traffic), the
packet MUST be discarded.
I know JNPR can do 2 vpn modes. There is one where we could use a VTI instead of a crypto map on the Cisco side. That was the solution to the problem we had.
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2013 01:19 AM
Hi and thanks for the suggestion, allthougj I dont think that is the issue here.
Frist of all, as you can see from the config, the 1921 contains multiple SAs and everone of them except the one for 10.150.4.0<->192.168.220.0 works and they are all configured the ssme om both ends
Second, I asume by vti you mean virtuel tunnel interface right? Well, thats how the juniper is configured already, I dont think I've used the cryptomap option on juniper for over 5 years
It must be something else
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2013 10:54 PM
Hello
The only thing I can say... This counter will increase only if a packet fails the SPD check after decryption [ eg like if the remote device encrypt with the wrong SPI]
Cheers.
decrypted packet failed SA identity check
decrypted packet failed SA identity chec
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide