- Cisco Community
- Technology and Support
- Security
- VPN
- Unable to ftp to AnyConnect VPN client
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unable to ftp to AnyConnect VPN client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2012 03:06 AM - edited 02-21-2020 06:30 PM
Hi all,
My VPN client is able to ftp to a server on the inside network but the server is not able to ftp to the VPN client. This happens when I enable the VPN filter in the group policy.
The error i get will be
access-list SSL_VPN-ACL denied tcp for user '<unknown>' DMZ/192.168.2.2(1376) -> DMZ/172.16.121.4(21) hit-cnt 1 first hit [0x3146b31b, 0x0]
When i disable the VPN filter, i will not encounter such a problem. I have 2 ASA in the network. 1 of them is acting as a firewall and the other is acting as the VPN concentrator. The VPN filter has been created to allow 192.168.2.2 to 172.16.121.0/29 on ftp and vice versa for FTP as well.
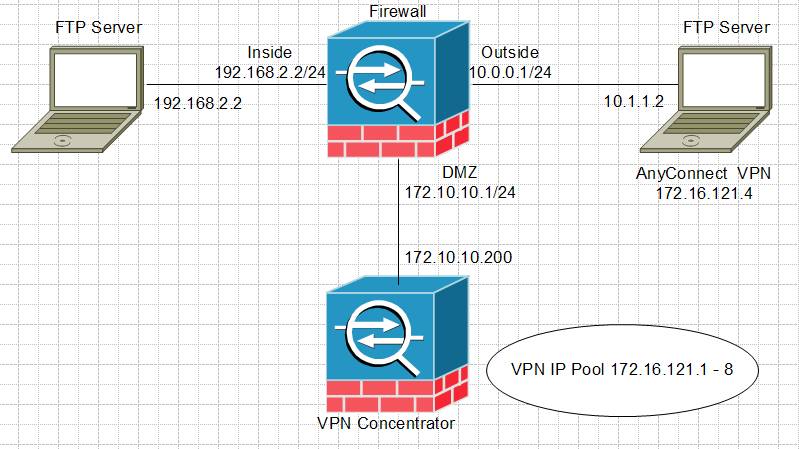
Anyone could advise me why the ftp from the inside ftp server to the vpn client ftp server fails when the filter is enabled in the group policy?
Thank you.
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2012 01:09 AM
Hi,
To my understanding VPN filter list for VPN Client connections are configured the same way like any other access-list on the firewall.
L2L VPN connections have their own Filter configuration. In that configuration the remote address is always the "source" address in the rules.
Though seems you are using VPN Client so I'm not sure what the problem is. Would seem that there is something wrong with the Filter rule since removing makes it work.
Can you copy/paste some configurations here. Atleast the Filter ACL used for the VPN Client connection
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 04:48 PM
Hi Journi,
Thanks for the reply.
same-security-traffic permit intra-interface
object network NETWORK_OBJ_172.16.121.0_27
subnet 172.16.121.0 255.255.255.224
object network Test_PC
host 192.168.2.2
access-list Split-Tunnel standard permit 192.168.2.0 255.255.255.0
access-list Split-Tunnel standard permit 192.168.1.0 255.255.255.0
access-list SSL_VPN-ACL extended permit tcp object NETWORK_OBJ_172.16.121.0_27 object Test_PC eq ftp
access-list SSL_VPN-ACL extended permit tcp object Test_PC object NETWORK_OBJ_172.16.121.0_27 eq ftp
access-list SSL_VPN-ACL extended deny ip any any
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map DMZ_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map DMZ_map interface DMZ
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable DMZ client-services port 443
crypto ikev2 remote-access trustpoint ASDM_TrustPoint0
webvpn
enable DMZ
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-3.1.01065-k9.pkg 1
anyconnect profiles Test_SSL_VPN_client_profile disk0:/Test_SSL_VPN_client_profile.xml
anyconnect enable
tunnel-group-list enable
group-policy "GroupPolicy_Test SSL VPN" internal
group-policy "GroupPolicy_Test SSL VPN" attributes
wins-server value 8.8.8.8
dns-server value 8.8.8.8
vpn-filter value SSL_VPN-ACL
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split-Tunnel
default-domain value 8.8.8.8
webvpn
anyconnect profiles value Test_SSL_VPN_client_profile type user
tunnel-group "Test SSL VPN" type remote-access
tunnel-group "Test SSL VPN" general-attributes
address-pool SSL_VPN
default-group-policy "GroupPolicy_Test SSL VPN"
tunnel-group "Test SSL VPN" webvpn-attributes
group-alias "Test SSL VPN" enable
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2012 10:16 AM
access-list SSL_VPN-ACL extended permit tcp object remote_object eq remote_port object local_object eq local_port
you don't need to mirror the ACE, it covers both directions
So you need
access-list SSL_VPN-ACL extended permit tcp object NETWORK_OBJ_172.16.121.0_27 eq ftp object Test_PC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 05:09 AM
Hi Peter,
I am able to FTP from ssl vpn client to inside host but not vice versa.
The access list is in my configuration. Without the other access list, will it resolve the problem?
The asa is not with me now so I can't try. Nevertheless,I will try once I have the chance.
Thanks.
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 08:08 AM
read it again (-:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

