- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Understanding NAT-T with IKEv1?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
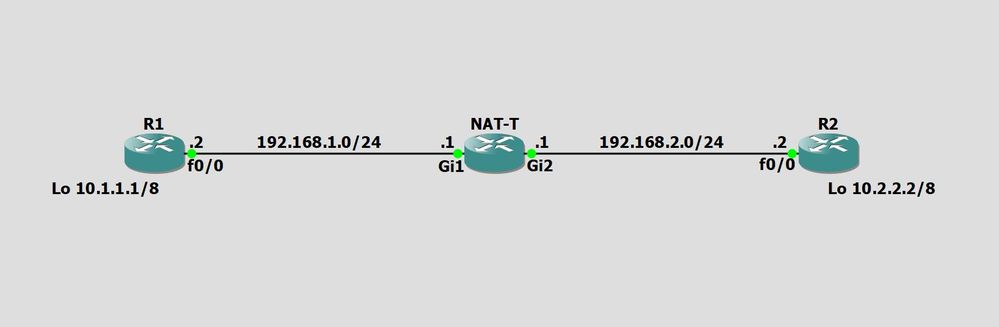
11-18-2020 08:39 AM
Hello guys, I'm trying to set up a basic site-to-site lab with NAT-T using port 4500 but I'm not sure if I'm missing a config or something needs to be removed somewhere on one of the routers or if I'm doing something wrong in general.
The loopbacks are acting as the interesting traffic LAN subnets to be encrypted and decrypted but when I ping 10.2.2.2 sourced from 10.1.1.1 on R1 I am seeing phase 1 up but phase 2 is showing send errors
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
192.168.1.2 192.168.2.2 QM_IDLE 1004 ACTIVE
IPv6 Crypto ISAKMP SA
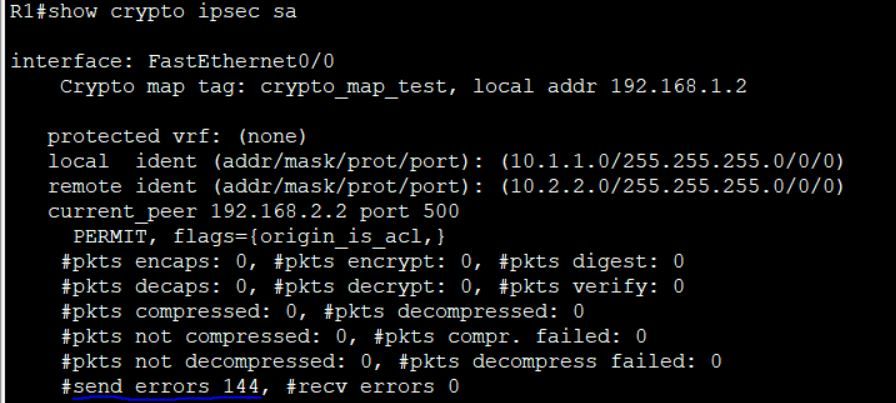
R1#show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: crypto_map_test, local addr 192.168.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.2.2.0/255.255.255.0/0/0)
current_peer 192.168.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
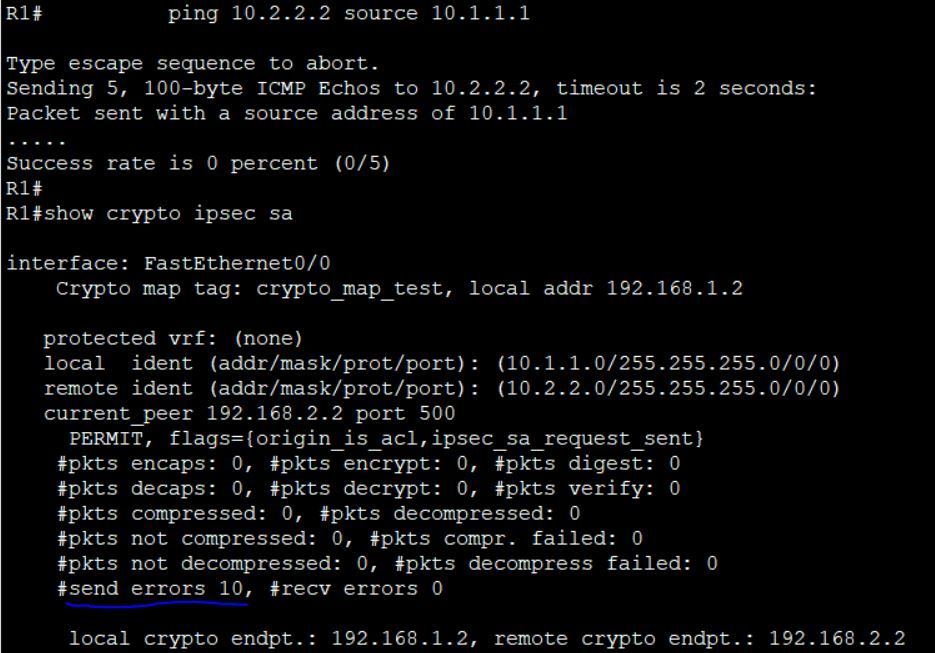
#send errors 115, #recv errors 0
local crypto endpt.: 192.168.1.2, remote crypto endpt.: 192.168.2.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
R1#
On R2 I'm seeing this
R2# show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
192.168.2.2 192.168.2.1 QM_IDLE 1004 ACTIVE
IPv6 Crypto ISAKMP SA
R2#
Any answers or suggestions in helping me correct and understand the NAT-T functioning is greatly appreciated
Here are the configs below.
===========================================================================================
R1#sh run
Building configuration...
Current configuration : 2415 bytes
!
upgrade fpd auto
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
logging message-counter syslog
!
no aaa new-model
ip source-route
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
no ip domain lookup
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
archive
log config
hidekeys
!
crypto keyring crypto_keyring_test
local-address 192.168.1.2
pre-shared-key address 192.168.2.2 key cisco
!
crypto isakmp policy 100
encr aes 256
authentication pre-share
group 14
!
crypto isakmp policy 200
encr aes 256
authentication pre-share
group 5
lifetime 28800
!
crypto isakmp policy 300
encr aes 256
authentication pre-share
group 2
lifetime 28800
!
crypto isakmp policy 400
encr aes 256
authentication pre-share
group 5
lifetime 28800
!
crypto isakmp policy 500
encr aes 256
authentication pre-share
group 2
lifetime 28800
!
crypto isakmp policy 600
encr aes
authentication pre-share
group 2
!
crypto isakmp policy 700
encr aes
authentication pre-share
group 2
lifetime 36600
crypto isakmp keepalive 10 10
crypto isakmp profile crypto_profile_test
description test crypto profile
keyring crypto_keyring_test
self-identity address
match identity address 192.168.2.2 255.255.255.255
local-address 192.168.1.2
!
!
crypto ipsec transform-set transform_set_test esp-aes 256 esp-sha-hmac
!
crypto map crypto_map_test 1 ipsec-isakmp
description test crypto map
set peer 192.168.2.2
set transform-set transform_set_test
set reverse-route tag 100
set isakmp-profile crypto_profile_test
match address crypto_acl_test
reverse-route static
!
!
!
ip tcp synwait-time 5
!
!
!
!
interface Loopback0
ip address 10.1.1.1 255.0.0.0
!
interface FastEthernet0/0
ip address 192.168.1.2 255.255.255.0
duplex half
crypto map crypto_map_test
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 192.168.1.1
no ip http server
no ip http secure-server
!
!
!
ip access-list extended crypto_acl_test
permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
!
no cdp log mismatch duplex
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
!
end
R1#
===========================================================================================
NAT#sh run
Building configuration...
Current configuration : 1799 bytes
!
! Last configuration change at 03:09:24 UTC Wed Nov 18 2020
!
version 16.7
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
platform console serial
!
hostname NAT
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
license udi pid CSR1000V sn 997IXWXAFGO
no license smart enable
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
!
!
!
redundancy
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet1
ip address 192.168.1.1 255.255.255.0
ip nat inside
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 192.168.2.1 255.255.255.0
ip nat outside
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet4
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
ip nat inside source static udp 192.168.1.2 500 192.168.2.1 500 extendable
ip nat inside source static udp 192.168.1.2 4500 192.168.2.1 4500 extendable
ip nat inside source list PAT interface GigabitEthernet2 overload
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
ip route 0.0.0.0 0.0.0.0 192.168.2.2
ip route 10.1.0.0 255.255.0.0 192.168.1.2
!
!
!
ip access-list extended PAT
permit ip 192.168.1.0 0.0.0.255 any
permit ip 10.1.0.0 0.0.255.255 any
!
!
!
!
control-plane
!
!
!
!
!
!
line con 0
stopbits 1
line vty 0 4
login
!
wsma agent exec
!
wsma agent config
!
wsma agent filesys
!
wsma agent notify
!
!
end
NAT#
===========================================================================================
R2#sh run
Building configuration...
Current configuration : 2415 bytes
!
upgrade fpd auto
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
logging message-counter syslog
!
no aaa new-model
ip source-route
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
no ip domain lookup
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
archive
log config
hidekeys
!
crypto keyring crypto_keyring_test
local-address 192.168.2.2
pre-shared-key address 192.168.2.1 key cisco
!
crypto isakmp policy 100
encr aes 256
authentication pre-share
group 14
!
crypto isakmp policy 200
encr aes 256
authentication pre-share
group 5
lifetime 28800
!
crypto isakmp policy 300
encr aes 256
authentication pre-share
group 2
lifetime 28800
!
crypto isakmp policy 400
encr aes 256
authentication pre-share
group 5
lifetime 28800
!
crypto isakmp policy 500
encr aes 256
authentication pre-share
group 2
lifetime 28800
!
crypto isakmp policy 600
encr aes
authentication pre-share
group 2
!
crypto isakmp policy 700
encr aes
authentication pre-share
group 2
lifetime 36600
crypto isakmp keepalive 10 10
crypto isakmp profile crypto_profile_test
description test crypto profile
keyring crypto_keyring_test
self-identity address
match identity address 192.168.2.1 255.255.255.255
local-address 192.168.2.2
!
!
crypto ipsec transform-set transform_set_test esp-aes 256 esp-sha-hmac
!
crypto map crypto_map_test 1 ipsec-isakmp
description test crypto map
set peer 192.168.2.1
set transform-set transform_set_test
set reverse-route tag 100
set isakmp-profile crypto_profile_test
match address crypto_acl_test
reverse-route static
!
!
!
ip tcp synwait-time 5
!
!
!
!
interface Loopback0
ip address 10.2.2.2 255.0.0.0
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
duplex half
crypto map crypto_map_test
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 192.168.2.1
no ip http server
no ip http secure-server
!
!
!
ip access-list extended crypto_acl_test
permit ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255
!
no cdp log mismatch duplex
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
!
end
R2#
===========================================================================================
Solved! Go to Solution.
- Labels:
-
IPSEC
-
Other VPN Topics
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2020 02:31 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 08:47 AM
Hi @EM_Chris
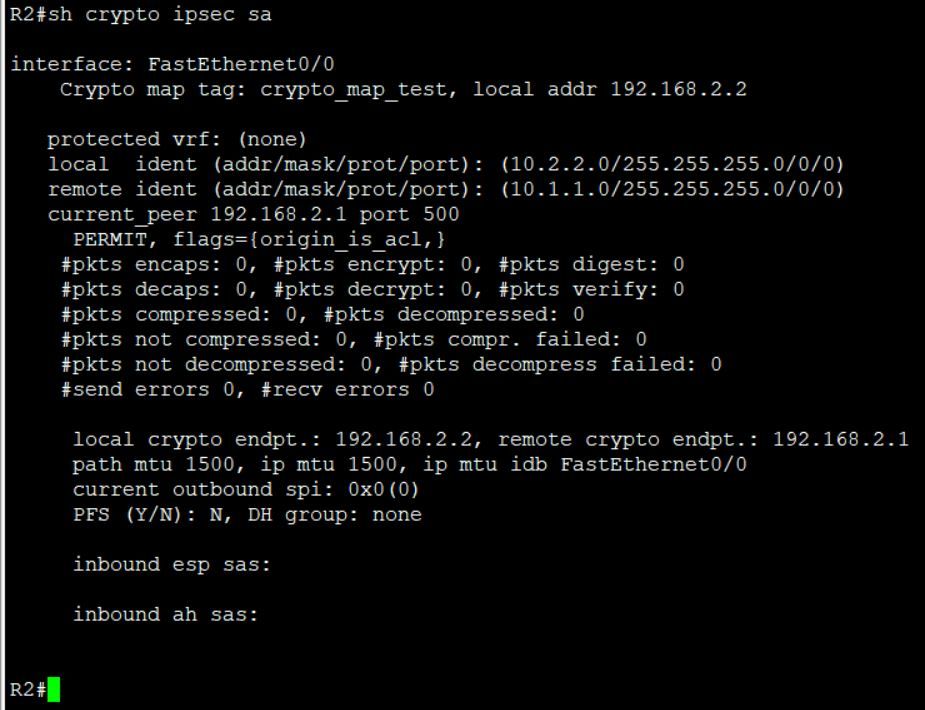
You IPSec SA are not formed, you have no inbound or outbound sas.
Check your nat configuration, you need to ensure traffic between the interesting traffic networks 10.1.1.0 and 10.2.2.0 is not natted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 09:22 AM
Thanks for the suggestion Rob.
I removed this line below from the NAT router
!
ip access-list extended PAT
permit ip 192.168.1.0 0.0.0.255 any
permit ip 10.1.0.0 0.0.255.255 any <--------- Removed
!
and then I went to R1 to do a ping sourced from Loopback0
but did still did not see any success just more "send errors"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 09:30 AM - edited 11-18-2020 09:41 AM
Yes, that rule was not required, traffic would only originate from the outside interface of the router.
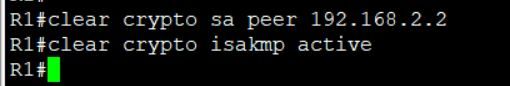
Can you turn on isakmp and ipsec debugs are provide the output for review.
clear crypto ipsec sa
clear crypto isakmp sa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 09:57 AM - edited 11-18-2020 10:04 AM
Okay I will run a debug, This R1 router doesn't have those specified clearing commands but it did have these here which I just ran
and then when I tested again I received the following results
I also tried it a second time with the following results. Does the configurations of the NAT device look valid?
Debug Output Below
R1#debug crypto isa
R1#debug crypto isakmp
Crypto ISAKMP debugging is on
R1#debug crypto ipsec
Crypto IPSEC debugging is on
R1#ping 10.2.2.2 source l0 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 10.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
*Nov 18 17:58:34.940: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 192.168.1.2, remote= 192.168.2.2,
local_proxy= 10.1.1.0/255.255.255.0/0/0 (type=4),
remote_proxy= 10.2.2.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-aes 256 esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
*Nov 18 17:58:34.940: ISAKMP: set new node 0 to QM_IDLE
*Nov 18 17:58:34.944: SA has outstanding requests (local 103.129.109.64 port 4500, remote 103.129.109.36 port 4500)
*Nov 18 17:58:34.944: ISAKMP:(1008): sitting IDLE. Starting QM immediately (QM_IDLE )
*Nov 18 17:58:34.944: ISAKMP:(1008):beginning Quick Mode exchange, M-ID of 1810344721
*Nov 18 17:58:34.948: ISAKMP:(1008):QM Initiator gets spi
*Nov 18 17:58:34.952: ISAKMP:(1008): sending packet to 192.168.2.2 my_port 4500 peer_port 4500 (I) QM_IDLE
*Nov 18 17:58:34.952: ISAKMP:(1008):Sending an IKE IPv4 Packet.
*Nov 18 17:58:34.956: ISAKMP:(1008):Node 1810344721, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Nov 18 17:58:34.956: ISAKMP:(1008):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Nov 18 17:58:34.976: ISAKMP (1008): received packet from 192.168.2.2 dport 4500 sport 4500 Global (I) QM_IDLE
*Nov 18 17:58:34.976: ISAKMP: set new node -222642591 to QM_IDLE
*Nov 18 17:58:34.976: ISAKMP:(1008): processing HASH payload. message ID = -222642591
*Nov 18 17:58:34.976: ISAKMP:(1008): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 749448050, message ID = -222642591, sa = 67816BBC
*Nov 18 17:58:34.976: ISAKMP:(1008): deleting spi 749448050 message ID = 1810344721
*Nov 18 17:58:34.976: ISAKMP:(1008):deleting node 1810344721 error TRUE reason "Delete Larval"
*Nov 18 17:58:34.976: ISAKMP:(1008):deleting node -222642591 error FALSE reason "Informational (in) state 1"
*Nov 18 17:58:34.976: ISAKMP:(1008):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
*Nov 18 17:58:34.976: ISAKMP:(1008):Old .State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
..............
*Nov 18 17:59:04.940: IPSEC(key_engine): request timer fired: count = 1,
(identity) local= 192.168.1.2, remote= 192.168.2.2,
local_proxy= 10.1.1.0/255.255.255.0/0/0 (type=4),
remote_proxy= 10.2.2.0/255.255.255.0/0/0 (type=4)
*Nov 18 17:59:04.944: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 192.168.1.2, remote= 192.168.2.2,
local_proxy= 10.1.1.0/255.255.255.0/0/0 (type=4),
remote_proxy= 10.2.2.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-aes 256 esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
*Nov 18 17:59:04.952: ISAKMP: set new node 0 to QM_IDLE
*Nov 18 17:59:04.952: SA has outstanding requests (local 103.129.109.64 port 4500, remote 103.129.109.36 port 4500)
*Nov 18 17:59:04.956: ISAKMP:(1008): sitting IDLE. Starting QM immediately (QM_IDLE )
*Nov 18 17:59:04.956: ISAKMP:(1008):beginning Quick Mode exchange, M-ID of 1930379786
*Nov 18 17:59:04.956: ISAKMP:(1008):QM Initiator gets spi
*Nov 18 17:59:04.960: ISAKMP:(1008): sending packet to 192.168.2.2 my_port 4500 peer_port 4500 (I) QM_IDLE
*Nov 18 17:59:04.964: ISAKMP:(1008):Sending an IKE IPv4 Packet.
*Nov 18 17:59:04.964: ISAKMP:(1008):Node 1930379786, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Nov 18 17:59:04.964: ISAKMP:(1008):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Nov 18 17:59:04.988: ISAKMP (1008): received packet from 192.168.2.2 dport 4500 sport 4500 Global (I) QM_IDLE
*Nov 18 17:59:04.988: ISAKMP: set new node 398554867 to QM_IDLE
*Nov 18 17:59:04.988: ISAKMP:(1008): processing HASH payload. message ID = 398554867
*Nov 18 17:59:04.988: ISAKMP:(1008): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 116095332, message ID = 398554867, sa = 67816BBC
*Nov 18 17:59:04.988: ISAKMP:(1008): deleting spi 116095332 message ID = 1930379786
*Nov 18 17:59:04.988: ISAKMP:(1008):deleting node 1930379786 error TRUE reason "Delete La.rval"
*Nov 18 17:59:04.988: ISAKMP:(1008):deleting node 398554867 error FALSE reason "Informational (in) state 1"
*Nov 18 17:59:04.988: ISAKMP:(1008):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
*Nov 18 17:59:04.988: ISAKMP:(1008):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
.........
*Nov 18 17:59:24.976: ISAKMP:(1008):purging node 1810344721
*Nov 18 17:59:24.976: ISAKMP:(1008):purging node -222642591.....
*Nov 18 17:59:34.944: IPSEC(key_engine): request timer fired: count = 2,
(identity) local= 192.168.1.2, remote= 192.168.2.2,
local_proxy= 10.1.1.0/255.255.255.0/0/0 (type=4),
remote_proxy= 10.2.2.0/255.255.255.0/0/0 (type=4).
*Nov 18 17:59:36.940: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 192.168.1.2, remote= 192.168.2.2,
local_proxy= 10.1.1.0/255.255.255.0/0/0 (type=4),
remote_proxy= 10.2.2.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-aes 256 esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
*Nov 18 17:59:36.948: ISAKMP: set new node 0 to QM_IDLE
*Nov 18 17:59:36.948: SA has outstanding requests (local 103.129.109.64 port 4500, remote 103.129.109.36 port 4500)
*Nov 18 17:59:36.952: ISAKMP:(1008): sitting IDLE. Starting QM immediately (QM_IDLE )
*Nov 18 17:59:36.952: ISAKMP:(1008):beginning Quick Mode exchange, M-ID of -2020606337
*Nov 18 17:59:36.952: ISAKMP:(1008):QM Initiator gets spi
*Nov 18 17:59:36.956: ISAKMP:(1008): sending packet to 192.168.2.2 my_port 4500 peer_port 4500 (I) QM_IDLE
*Nov 18 17:59:36.960: ISAKMP:(1008):Sending an IKE IPv4 Packet.
*Nov 18 17:59:36.960: ISAKMP:(1008):Node -2020606337, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Nov 18 17:59:36.960: ISAKMP:(1008):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Nov 18 17:59:36.980: ISAKMP (1008): received packet from 192.168.2.2 dport 4500 sport 4500 Global (I) QM_IDLE
*Nov 18 17:59:36.980: ISAKMP: set new node 2134774115 to QM_IDLE
*Nov 18 17:59:36.984: ISAKMP:(1008): processing HASH payload. message ID = 2134774115
*Nov 18 17:59:36.984: ISAKMP:(1008): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 4110640970, message ID = 2134774115, sa = 67816BBC
*Nov 18 17:59:36.984: ISAKMP:(1008): deleting spi 4110640970 message ID = -2020606337
*Nov 18 17:59:36.984: ISAKMP:(1008):deleting node -2020606337 error TRUE reason "Delete Larval"
*Nov 18 17:59:36.984: ISAKMP:(1008):deleting node 2134774115 error FALSE reason "Informational (in) state 1"
*Nov 18 17:59:36.984: ISAKMP:(1008):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
*Nov 18 17:59:36.984: ISAKMP:(1008.):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
........
*Nov 18 17:59:54.988: ISAKMP:(1008):purging node 1930379786
*Nov 18 17:59:54.988: ISAKMP:(1008):purging node 398554867......
*Nov 18 18:00:06.940: IPSEC(key_engine): request timer fired: count = 1,
(identity) local= 192.168.1.2, remote= 192.168.2.2,
local_proxy= 10.1.1.0/255.255.255.0/0/0 (type=4),
remote_proxy= 10.2.2.0/255.255.255.0/0/0 (type=4)
*Nov 18 18:00:06.944: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 192.168.1.2, remote= 192.168.2.2,
local_proxy= 10.1.1.0/255.255.255.0/0/0 (type=4),
remote_proxy= 10.2.2.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-aes 256 esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
*Nov 18 18:00:06.944: ISAKMP: set new node 0 to QM_IDLE
*Nov 18 18:00:06.944: SA has outstanding requests (local 103.129.109.64 port 4500, remote 103.129.109.36 port 4500)
*Nov 18 18:00:06.944: ISAKMP:(1008): sitting IDLE. Starting QM immediately (QM_IDLE )
*Nov 18 18:00:06.944: ISAKMP:(1008):beginning Quick Mode exchange, M-ID of 617611798
*Nov 18 18:00:06.944: ISAKMP:(1008):QM Initiator gets spi
*Nov 18 18:00:06.944: ISAKMP:(1008): sending packet to 192.168.2.2 my_port 4500 peer_port 4500 (I) QM_IDLE
*Nov 18 18:00:06.944: ISAKMP:(1008):Sending an IKE IPv4 Packet.
*Nov 18 18:00:06.944: ISAKMP:(1008):Node 617611798, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Nov 18 18:00:06.944: ISAKMP:(1008):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Nov 18 18:00:06.964: ISAKMP (1008): received packet from 192.168.2.2 dport 4500 sport 4500 Global (I) QM_IDLE
*Nov 18 18:00:06.964: ISAKMP: set new node 985509224 to QM_IDLE
*Nov 18 18:00:06.968: ISAKMP:(1008): processing HASH payload. message ID = 985509224
*Nov 18 18:00:06.968: ISAKMP:(1008): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 3833883651, message ID = 985509224, sa = 67816BBC
*Nov 18 18:00:06.968: ISAKMP:(1008): deleting spi 3833883651 message ID = 617611798
*Nov 18 18:00:06.968: ISAKMP:(1008):deleting node 617611798 error TRUE reason "Delete Larv.al"
*Nov 18 18:00:06.968: ISAKMP:(1008):deleting node 985509224 error FALSE reason "Informational (in) state 1"
*Nov 18 18:00:06.968: ISAKMP:(1008):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
*Nov 18 18:00:06.968: ISAKMP:(1008):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
...
Success rate is 0 percent (0/50)
R1#no deb
R1#no debug all
All possible debugging has been turned off
R1#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 05:55 PM
I've attached the debug output.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 08:47 AM
try ping using source
ping 10.1.1.1 source 10.2.2.2
not using source make router use outgoing interface ip not ip that you config in acl match.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 09:25 AM
Thanks for the suggestion MHM.
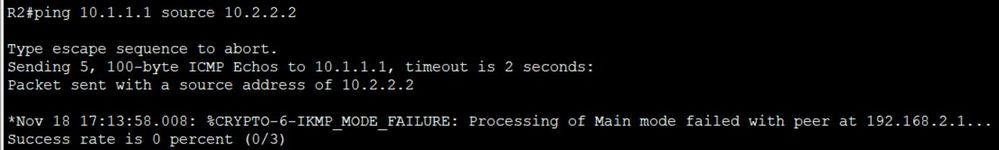
When I went on R1 and pinged 10.2.2.2 sourced from 10.1.1.1 a message popped up about main mode failing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 10:41 AM - edited 11-19-2020 04:10 PM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 05:09 PM - edited 11-19-2020 07:30 PM
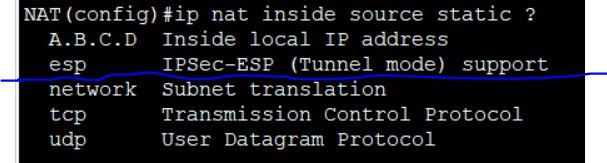
Thank you for the explanation I not actually seeing any esp packets in the trace though.
and for configuring nat with esp is it done with this option here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2020 12:51 PM
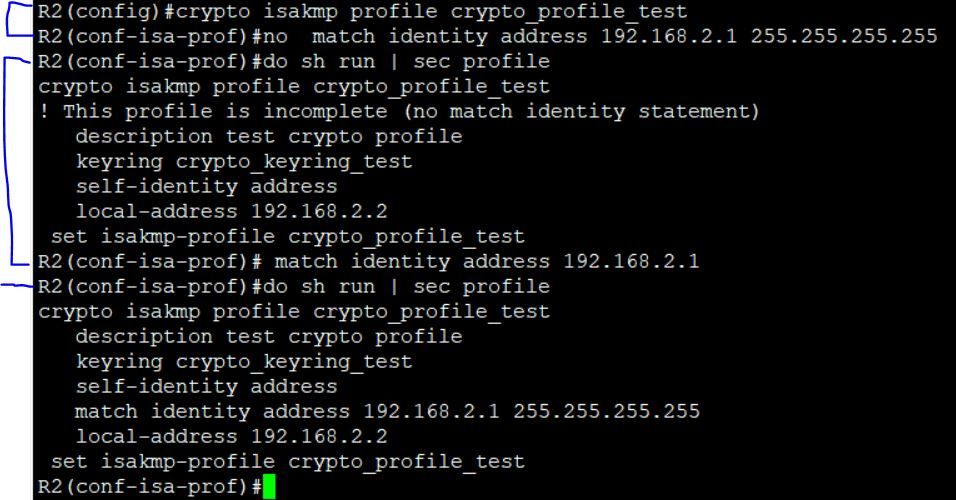
change this in R2
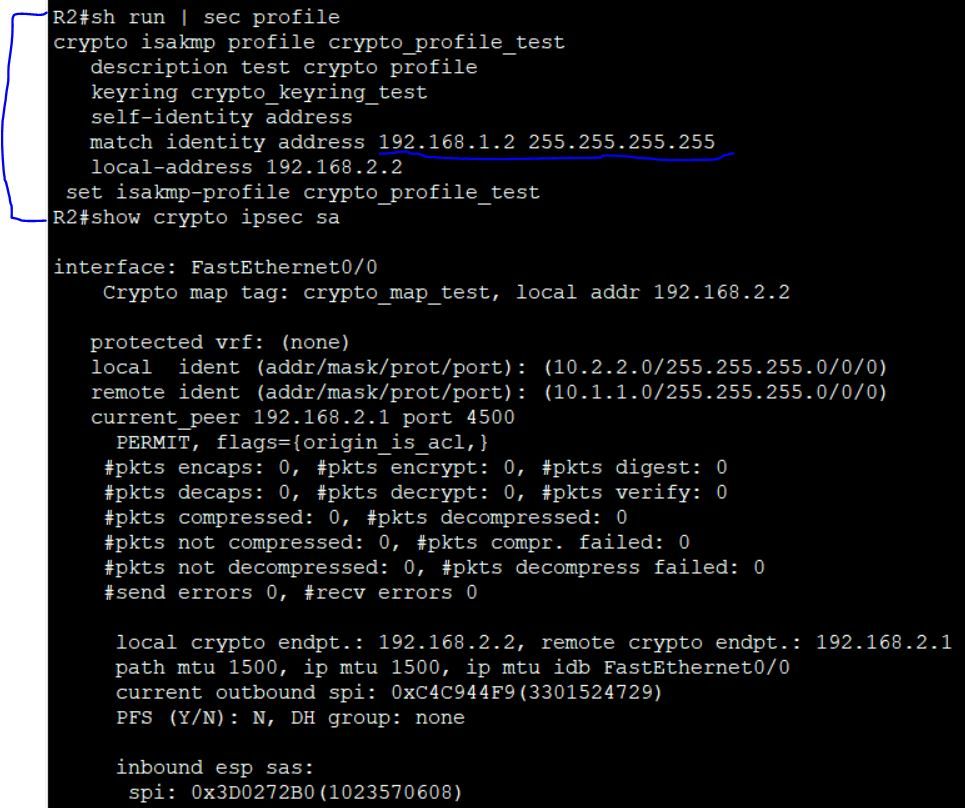
match identity address 192.168.2.1 255.255.255.255->change identity to be 192.168.1.2
and check again
show me the
show crypto ipsec sa
for both R1 & R2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2020 02:11 PM
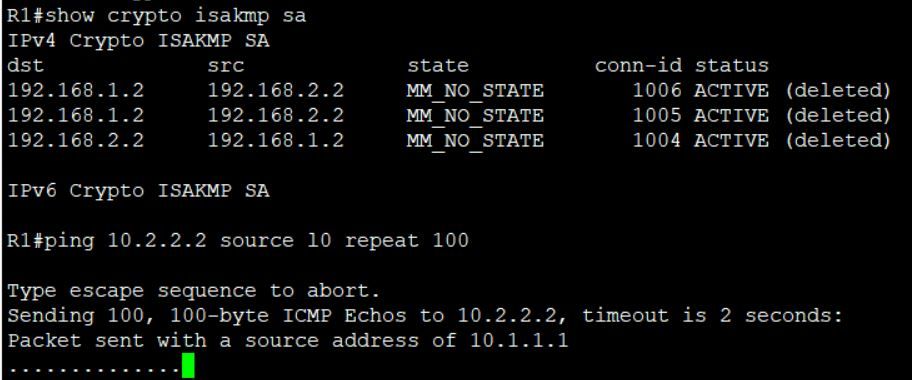
I removed that statement from the profile in R2 and then I added it back as you specified without the mask. As you can see once I added it back it automatically added the mask back.
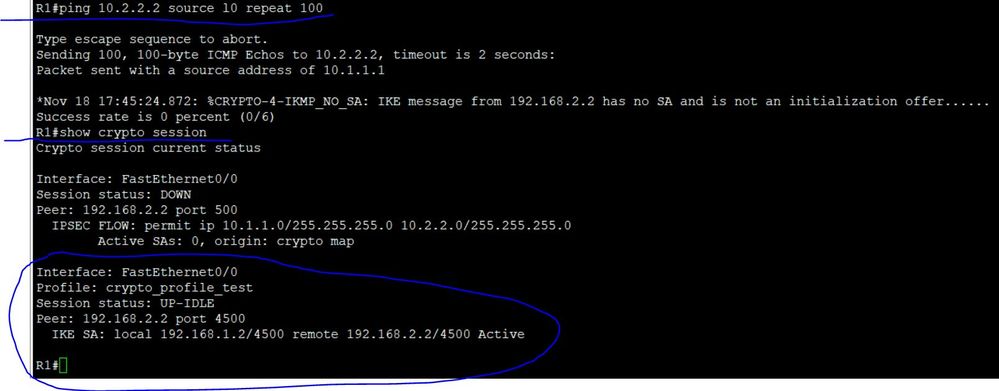
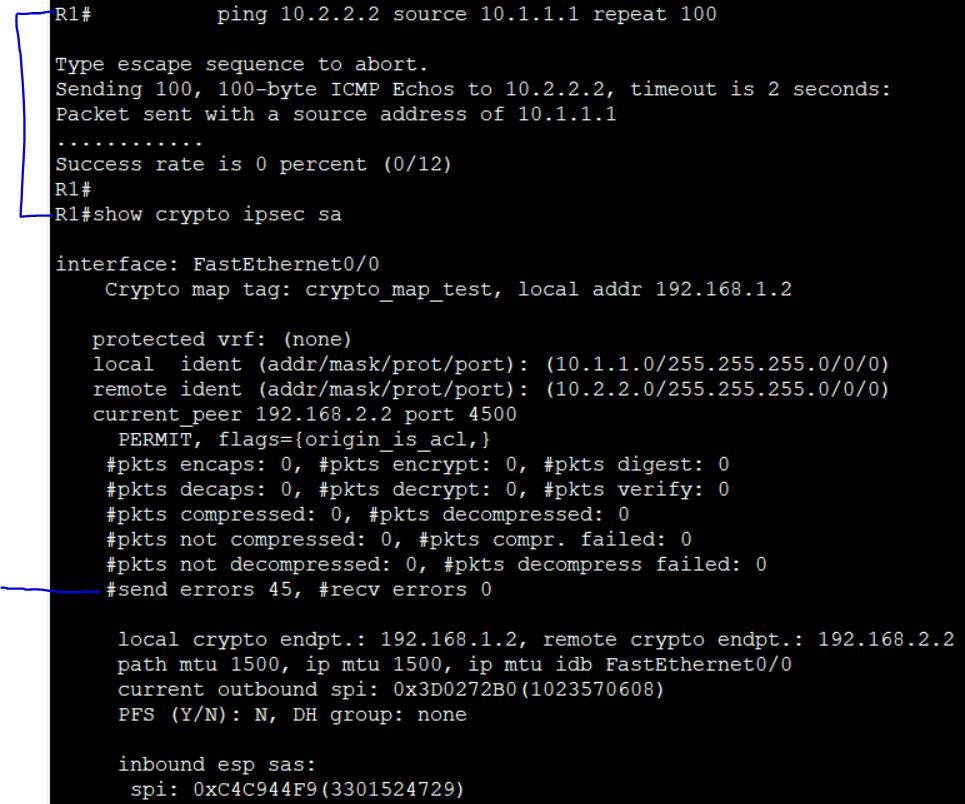
Then I ran a ping test on R1 followed by "show crypto ipsec sa" command
On R2 "show crypto ipsec sa" command
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2020 02:31 PM
It was 2.1 and now 2.1
i want to change this be 1.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2020 02:41 PM
Oh okay sorry here are the results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2020 02:52 PM - edited 11-20-2020 02:58 PM
Any change in ipsec need to
first clear crypto sa
clear crypto isakmp
second do change
third test.
so now only clear and do test again
also if you can check wireshark>isakmp you must get 9 message (6 mm and 3 Qm)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide