- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Unstable IPSEC tunnel between Fortigate 200D and ASA5506-X
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 03:11 PM - edited 03-07-2022 03:13 PM
Hi Everyone,
We are struggling with setting up a stable IPSEC tunnel between FWs mentioned in the subject.
Tunnel itself is up all the time, allowing bidirectional communication to start with, but then, in random times, stops passing traffic while the tunnel is still showed as UP in Monitoring section in ASDM (also ping traffic is being generated constantly).
Logging out the tunnel and bringing it up again restores the 2-way flow immediately.
We have verified all timers on bot sides and they are identical.
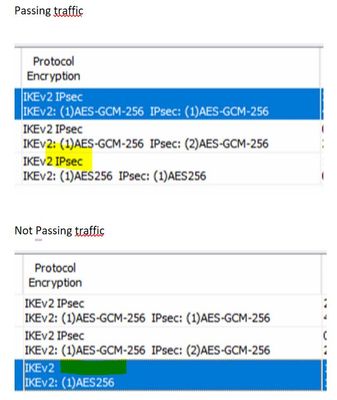
One thing I noticed is that in ASDM 'Monitoring' section for VPN Sessions:
- when traffic is passing through then the Protocol Encryption column for that tunnel says IKEv2 IPSEC
- when traffic is not passing it says just IKEv2 (w/o IPSEC part)
Does it indicate any specific issue? any misconfig that we have missed in our verification?
I will soon provide configuration from both sides but first would like to clarify that Monitoring status. Thanks in advance
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 04:01 PM
Rekey is not done, ikev2 use rekey after tunnel is up and both peer use key, after specific time the rekey is need otherwise the traffic not pass.
Config pfs in both peer
config dh group for both phase1 and phase 2
above is recommend from the AWS, but still it make sense to test it for fortigate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 04:01 PM
Rekey is not done, ikev2 use rekey after tunnel is up and both peer use key, after specific time the rekey is need otherwise the traffic not pass.
Config pfs in both peer
config dh group for both phase1 and phase 2
above is recommend from the AWS, but still it make sense to test it for fortigate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 11:32 PM
Thanks a lot for a quick response @MHM Cisco World - indeed PFS was not enabled on cisco side. I did now ask to do the same on Fortigate peer. Will verify and report here if it fixed the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2022 05:19 AM
Hi again! I am happy to inform that enabling PFS solved the stability issue - it has been stable for the last 24 hours. Thanks again @MHM Cisco World
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2022 05:51 AM
You are so welcome.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide