- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN IPsec issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN IPsec issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2020 11:01 PM
I am configuring VPN between cisco and checkpoint, phase 1 came up but in phase 2 packets are not encrypted and are not decrypted, I have attached my configuration, please anyone could help on this I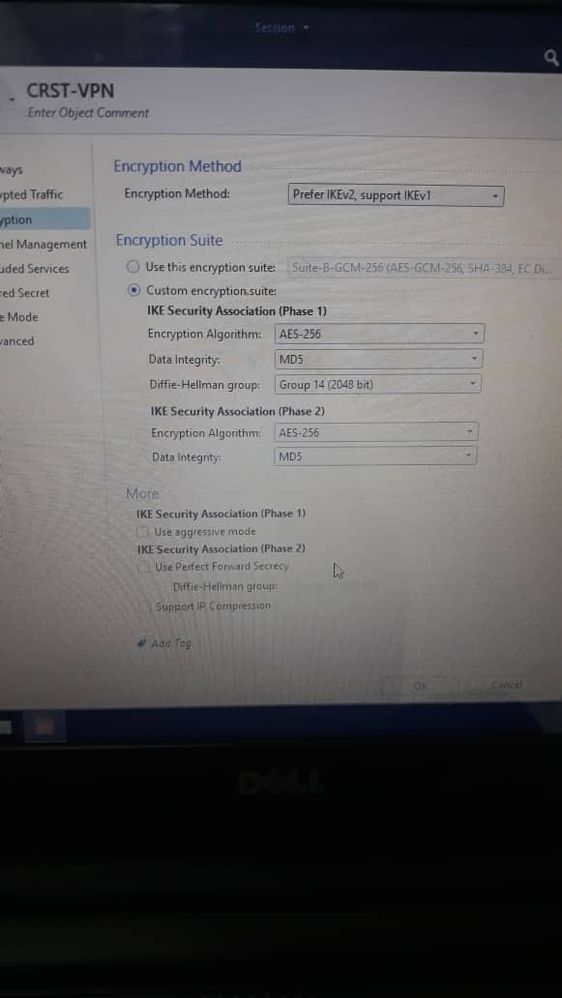
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 12:27 AM
Hi,
You have PFS (Perfect Forward Secrecy) configured on the cisco router with the command "set pfs group14" but you do not have the tick box "Use Perfect Forward Secrecy) enabled on the Check Point firewall.
Either disable PFS on the router (no set pfs group14) or enable it on the Check Point firewall, ensure the same group is defined (group14).
Aside from that MD5 is weak and insecure, consider using SHA instead.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 12:37 AM
Thanks, will try once and if issue still persist will revert to sir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 02:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 03:02 AM
*Jun 1 08:33:48.509: ISAKMP:(1394): phase 2 SA policy not acceptable!
*Jun 1 08:33:49.093: IKE Dispatcher: IKEv2 version 2 detected, Dropping packet!
*Jun 1 08:33:58.781: IKE Dispatcher: IKEv2 version 2 detected, Dropping packet!
*Jun 1 08:34:03.861: IKE Dispatcher: IKEv2 version 2 detected, Dropping packet!
*Jun 1 08:34:11.861: IKE Dispatcher: IKEv2 version 2 detected, Dropping packet!
*Jun 1 08:34:23.173: IKE Dispatcher: IKEv2 version 2 detected, Dropping packet!
Change the Check Point configuration to use IKEv1 only instead of "Prefer IKEv2, support IKEv1".
Double check your IPSec/Phase 2 configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 03:32 AM
when I change ACL to any any, am able to ping other ends global IP but couldn't ping local IP and internet also not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 04:03 AM
Dear ,
Find below mentioned artical
When you are going to create Site2Site vpn from cisco router you should create Route map for No NAT (Subnet which you want to access by VPN)
SO please understand below artical
Search ACL 101
once you will do this configuration you should also check no nat rule should be configured in Checkpoint Also
post please check connectivity it should work
I hope you got your answer
Regards,
Harmesh Yadav
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 03:37 AM
The issues still coming, couldn't bring up phase 2, please kindly assist us in resolving the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 10:05 AM
Please recheck access list Informaiton and phase 2 parameter it must match both side as per your debug msg you should check access list and other parameter
Please recheck all phase 2 information and access list with subnet
we need to check checkpoint and Router configuration
Regards,
Harmesh Yadav
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2020 10:10 PM
Dear ,
What is the status of Tunnel and in cisco Phase 2 showing up or not
check this command
show crypto isakmp sa
show crypto ipsec sa
in second command output check all subnet showing or not
And one more thing if you have created access lit in cisco router - In that access list any services should have selected other wise itwill not support
and for checkpoint you should check where packet stuck
check nating part if checkpoint is doing nating or not
and do you configured proper subnet in VPN domain or not
CHeckpoint Policy also you have to check
Regards,
Harmesh Yadav
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2020 10:54 PM
Hi,
Along with can you check your ACL configuration as
ip access-list extended CRST-ACL
permit ip 10.x.x.0 0.0.0.0 172.x.x0.0 0.0.0.255I think it would be like 10.x.x.0 0.0.0.255 good answer.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



