- Cisco Community
- Technology and Support
- Security
- VPN
- VPN IPSEC Site-to-Site
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN IPSEC Site-to-Site
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2012 11:34 AM - edited 02-21-2020 06:10 PM
Hello, i was trying to set VPN connection encrypted via IPSEC in packet tracer between two Routers.
If i use extend ping from Router2 to Router1 (192.168.2.254 --> 192.168.1.254) command 'show crypto ipsec sa' show me
pkts encaps: 4
pkts decaps: 4
pkts encrypt: 4
pkts decrypt: 4
pkts digest: 0
pkts verify: 0
shouldnt be digest and verify 4 too ? Where could be a problem ?
Here is my network diagram
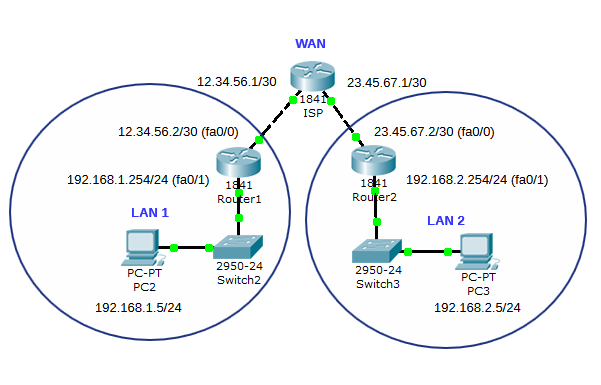
Here is result of extended ping

Here is behaviour if i ping from LAN1-PC2 to LAN2-PC3 (there should be an IPSEC protocol instead of ICMP right ?)
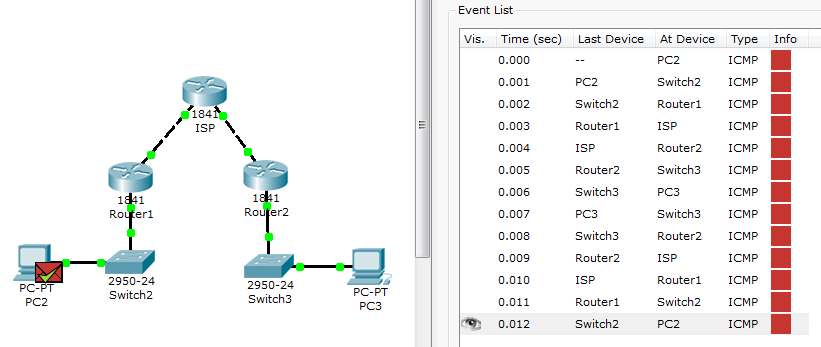
My packet tracer .pkt is attached here or it can be downloaded at
http://php-testing.wz.cz/vpn_ipsec_site-to-site.pkt
Example of configuration steps at Router2
Router>en
Router#config t
Router(config)#hostname R2
R2(config)#int f0/1
R2(config-if)#ip address 192.168.2.254 255.255.255.0
R1(config-if)#no shut
R2(config-if)#int f0/0
R2(config-if)#no shut
R2(config-if)#ip address 23.45.67.2 255.255.255.252
R2(config-if)#ip route 0.0.0.0 0.0.0.0 23.45.67.1
R2(config)#do ping 12.34.56.2 //mely by jsme PINGnout R1
R2(config)#crypto isakmp policy 1
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#encryption aes
R2(config-isakmp)#hash sha
R2(config-isakmp)#group 5
R2(config-isakmp)#crypto isakmp key t4jneheslo address 12.34.56.2
R2(config)#crypto ipsec transform-set esp-aes-sha esp-aes esp-sha-hmac
R2(config)#access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
R2(config)#crypto map vpn 10 ipsec-isakmp
R2(config-crypto-map)#match address 101
R2(config-crypto-map)#set transform-set esp-aes-sha
R2(config-crypto-map)#set peer 12.34.56.2
R2(config-crypto-map)#exit
R2(config)#int fa0/0
R2(config-if)#crypto map vpn
-----------------------------------------------------------------------------------------------------------------------
Please help me, if you will need more informations i will give it to you and this is important to me but im not so good in networking.
thank you
Muflix
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2012 01:47 PM
Dear Muflix,
The tunnel is up and I can see encaps and decaps.
I would recommend try this on real equipment or even on GNS3 if you want to see it fully working, PKT is a powerful tool but it is kind of limited on some functions.
I hope it helps.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2012 02:40 PM
If the config shown is really the one that was used for the output, then you should see also the same amount of packets with digest and verify. Your transform-set has an encryption-transform and an authentication-transform so you really should see sem. The digest/verify should only be "0" if no authentication-transform is used. But that's not a best practice although there are many examples from Cisco configuring it that way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2012 03:55 PM
I totally agree with you Karsten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2012 09:38 PM
Thank you for answers, im going to italy but then i will try it in GNS3 and check it with wireshark what is real traffic. But im glad config seems ok to you :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2012 12:12 AM
Thanks for the heads up!
I hope you have a nice trip! Take care
Please rate any post you find helpful
Sent from Cisco Technical Support Android App
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

