- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN split tunnel issues with 1811W and IAS RADIUS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2011 07:02 AM
I am very new to setting up an IPSEC VPN with a Cisco Router. I am very familiar on how to do this with a PIX/ASA, but the commands are a little different in IOS, hence my issues. Here is what is happening, I can connect to the VPN with the Cisco VPN Client. I get assigned an address from my ip pool that I have created, but when I try to access the remote network in any way, I cannot. I ran a tracert and what is really strange is I am getting the external IP of the 1811W as my first hop when I list an internal IP address of the remote network (it also resolves the FQDN of the device, so I know my DNS configuration is correct). I am going to list my config of the 1811W along with the screenshot of the tracert. I have removed all encrypted passwords, but they are there in the config on the router and I am able to connect to the network and hit the IAS server behind it. Please excuse the config as we took this over from another IT provider so it may have some extra entries that may not be needed that I have no cleaned up yet.
Tracert:
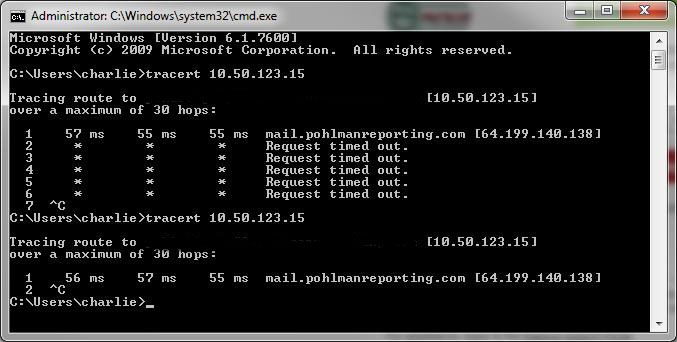
And here is the full config:
Building configuration...
Current configuration : 9320 bytes
!
version 12.4
no service pad
service timestamps debug datetime msec
service timestamps log datetime localtime show-timezone
service password-encryption
!
hostname RTR01
!
boot-start-marker
boot-end-marker
!
logging buffered 8192
enable password 7
!
aaa new-model
!
!
aaa authentication login userauthen group radius local
aaa authorization network groupauthor local
!
!
aaa session-id common
clock timezone Central -6
!
dot11 ssid internal
vlan 5
authentication open
authentication key-management wpa
guest-mode
wpa-psk ascii 7
!
dot11 ssid public-access
vlan 10
authentication open
!
!
!
ip cef
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.1.1 192.168.1.10
ip dhcp excluded-address 192.168.1.20 192.168.1.254
!
ip dhcp pool public
import all
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
dns-server 10.50.123.15 207.69.188.186
!
!
no ip domain lookup
ip domain name pohlmanreporting.com
!
multilink bundle-name authenticated
!
crypto pki trustpoint TP-self-signed-3986412950
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3986412950
revocation-check none
rsakeypair TP-self-signed-3986412950
!
!
crypto pki certificate chain TP-self-signed-3986412950
certificate self-signed 01
quit
!
!
username admin privilege 15 password 7
username cisco password 7
username ssetech privilege 15 secret 5
archive
log config
!
!
!
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
!
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
!
crypto isakmp client configuration group VPNGROUP
key
dns 10.50.123.15
domain domain.com
pool VPNPOOL
acl 110
include-local-lan
!
!
crypto ipsec transform-set esp-3des-md5 esp-3des esp-md5-hmac
crypto ipsec transform-set esp-des-md5 esp-des esp-md5-hmac
crypto ipsec transform-set TRANS_3DES_SHA esp-3des esp-sha-hmac
crypto ipsec transform-set myset esp-3des esp-sha-hmac
!
crypto dynamic-map EXA_DYNAMIC_MAP 10
set transform-set myset
reverse-route
!
!
crypto map EXT_MAP client authentication list userauthen
crypto map EXT_MAP isakmp authorization list groupauthor
crypto map EXT_MAP client configuration address respond
crypto map EXT_MAP 10 ipsec-isakmp dynamic EXA_DYNAMIC_MAP
!
!
!
bridge irb
!
!
!
interface FastEthernet0
ip address 64.199.140.138 255.255.255.248
ip access-group deny-hack-attack in
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip virtual-reassembly
ip route-cache flow
duplex auto
speed auto
no cdp enable
crypto map EXT_MAP
!
interface FastEthernet1
description REDUNDANT INET CONNECTION
no ip address
duplex auto
speed auto
!
interface FastEthernet2
!
interface FastEthernet3
!
interface FastEthernet4
!
interface FastEthernet5
!
interface FastEthernet6
!
interface FastEthernet7
!
interface FastEthernet8
!
interface FastEthernet9
!
interface Dot11Radio0
description 802.11B/G interface
no ip address
!
encryption vlan 5 mode ciphers tkip
!
ssid internal
!
ssid public-access
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0
channel 2462
station-role root
!
interface Dot11Radio0.5
encapsulation dot1Q 5
no cdp enable
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 spanning-disabled
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
!
interface Dot11Radio0.10
encapsulation dot1Q 10
ip address 192.168.1.1 255.255.255.0
ip access-group 130 in
ip nat inside
ip virtual-reassembly
no cdp enable
!
interface Dot11Radio1
description 802.11A interface
no ip address
shutdown
speed basic-6.0 9.0 basic-12.0 18.0 basic-24.0 36.0 48.0 54.0
station-role root
!
interface Vlan1
no ip address
bridge-group 1
!
interface Async1
no ip address
encapsulation slip
!
interface BVI1
ip address 10.50.123.1 255.255.255.0
ip access-group 105 in
ip nat inside
ip virtual-reassembly
ip tcp adjust-mss 1452
!
ip local pool VPNPOOL 192.168.130.1 192.168.130.50
ip route 0.0.0.0 0.0.0.0 64.199.140.137
ip route 10.60.52.0 255.255.255.0 10.50.123.2
!
!
ip http server
ip http authentication local
ip http secure-server
ip http timeout-policy idle 600 life 86400 requests 10000
ip nat pool POOL 64.199.140.138 64.199.140.142 netmask 255.255.255.248
ip nat inside source list 120 interface FastEthernet0 overload
ip nat inside source route-map do-nat interface FastEthernet0 overload
ip nat inside source static tcp 10.50.123.14 21 64.199.140.138 21 extendable
ip nat inside source static tcp 10.50.123.11 25 64.199.140.138 25 extendable
ip nat inside source static tcp 10.50.123.11 80 64.199.140.138 80 extendable
ip nat inside source static tcp 10.50.123.11 143 64.199.140.138 143 extendable
ip nat inside source static tcp 10.50.123.11 443 64.199.140.138 443 extendable
ip nat inside source static tcp 10.50.123.10 1723 64.199.140.138 1723 extendable
ip nat inside source static tcp 10.50.123.14 21 64.199.140.139 21 extendable
ip nat inside source static tcp 10.50.123.18 80 64.199.140.139 80 extendable
ip nat inside source static tcp 10.50.123.18 443 64.199.140.139 443 extendable
ip nat inside source static tcp 10.50.123.18 3389 64.199.140.139 3389 extendable
ip nat inside source static tcp 10.50.123.14 80 64.199.140.141 80 extendable
ip nat inside source static tcp 10.50.123.14 443 64.199.140.141 443 extendable
ip nat inside source static 10.50.123.40 64.199.140.142 extendable
!
ip access-list extended deny-hack-attack
permit udp 10.0.0.0 0.255.255.255 any eq snmp
deny udp any any eq snmp
deny udp any any eq tftp
deny udp any any eq bootpc
deny udp any any eq bootps
deny ip 172.16.0.0 0.15.255.255 any
deny ip 192.168.0.0 0.0.255.255 any
permit ip any any
!
logging trap debugging
logging 10.50.123.15
access-list 99 permit 10.0.0.0 0.255.255.255
access-list 99 permit 69.63.100.0 0.0.1.255
access-list 102 permit ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 105 deny ip any host 69.63.101.225
access-list 105 permit ip any any
access-list 110 permit ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.10.0.0 0.0.255.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 111 permit ip 10.50.123.0 0.0.0.255 any
access-list 112 deny ip 10.50.123.0 0.0.0.255 172.0.0.0 0.0.0.255
access-list 112 permit ip any any
access-list 120 permit ip 192.168.1.0 0.0.0.255 any
access-list 130 permit udp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq domain
access-list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq domain
access-list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq www
access-list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq 443
access-list 130 deny ip any 10.0.0.0 0.255.255.255
access-list 130 permit ip any any
snmp-server community none RO
!
!
!
route-map do-nat permit 10
match ip address 111
!
!
!
radius-server host 10.50.123.13 auth-port 1645 acct-port 1646 key 7
!
control-plane
!
bridge 1 protocol ieee
bridge 1 route ip
!
line con 0
exec-timeout 120 0
line 1
modem InOut
stopbits 1
speed 115200
flowcontrol hardware
line aux 0
line vty 0 4
location ** Virtual Terminal access allowed only from internal network **
access-class 99 in
exec-timeout 0 0
login authentication userauthen
transport input telnet ssh
!
scheduler max-task-time 5000
!
webvpn cef
!
webvpn context Default_context
ssl authenticate verify all
!
no inservice
!
!
end
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2011 08:35 PM
You would need to also create NAT exemption for traffic between your internal network towards the VPN Client pool.
You have the following 2 NAT statements:
ip nat inside source list 120 interface FastEthernet0 overload
ip nat inside source route-map do-nat interface FastEthernet0 overload
For access-list 120, please add the following:
ip access-list extended 120
1 deny ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Route-map "do-nat" uses ACL 111, please also add the following:
ip access-list extended 111
1 deny ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Then "clear ip nat trans *" after the above changes, and try to connect again.
Hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2011 08:35 PM
You would need to also create NAT exemption for traffic between your internal network towards the VPN Client pool.
You have the following 2 NAT statements:
ip nat inside source list 120 interface FastEthernet0 overload
ip nat inside source route-map do-nat interface FastEthernet0 overload
For access-list 120, please add the following:
ip access-list extended 120
1 deny ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Route-map "do-nat" uses ACL 111, please also add the following:
ip access-list extended 111
1 deny ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Then "clear ip nat trans *" after the above changes, and try to connect again.
Hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2011 08:56 PM
Jennifer, I knew it would be something simple. This worked perfectly! Thank you very much!!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

