- Cisco Community
- Technology and Support
- Security
- VPN
- VPN via NAT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2023 08:54 PM
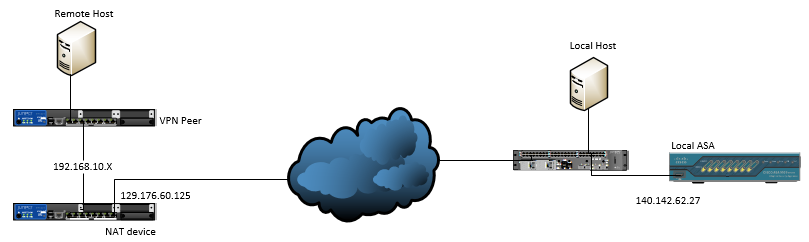
I have the following topology
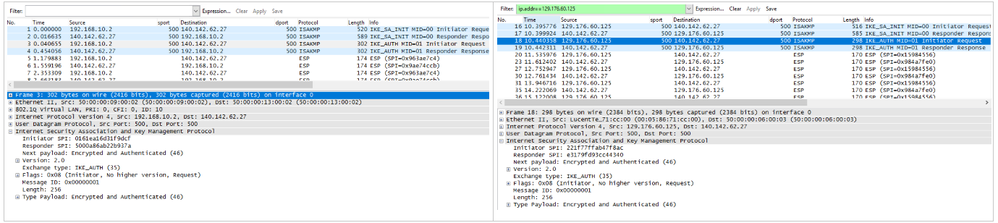
with NAT-T disabled on Cisco ASA (no crypto isakmp nat-traversal 20), I got the following
I thought the VPN should fail. What did I miss here ?
thanks a lot !!
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 07:18 AM
@gongya with NAT-T disabled on either device, a VPN can be established when using Static NAT.
If using PAT this is when you need NAT-T on both devices, as ESP does not have ports to be translated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 08:55 AM
You are so so welcome
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 02:45 AM
I dont get what you ask here ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 06:26 AM
Sorry. What I like to ask is
1. NAT-T must be enabled on both ends to bring VPN up?
2. The test above only has NAT-T enabled on the remote peer, ASA has NAT-T disabled globally. The VPN is up.
3. It might be relate to that NAT I configured. The NAT above is static NAT.
I will try PAT to see whether VPN requires NAT-T enabled on both ends.
thanks so much !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 07:18 AM
@gongya with NAT-T disabled on either device, a VPN can be established when using Static NAT.
If using PAT this is when you need NAT-T on both devices, as ESP does not have ports to be translated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 08:39 AM
thanks a lot ! Clear now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 07:42 AM
I think you misconfig the peer in crypto map,
the static NAT work if you disable NAT-T.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 08:40 AM
thanks a lot !! clear now !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 08:55 AM
You are so so welcome
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 10:22 AM - edited 01-15-2023 10:31 AM
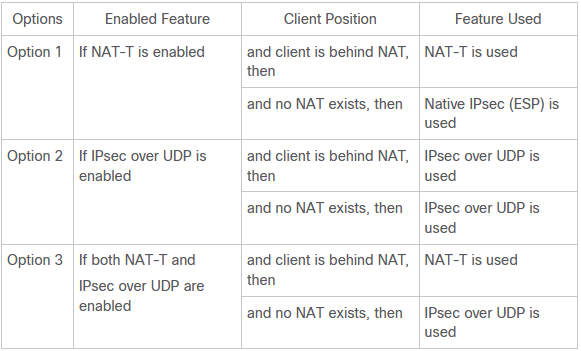
One more question to bother.
crypto isakmp nat-traversal 20
Does this command achieve both option 1 and option 2? or there are separate commands for either option ?
thanks so much !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 11:01 AM
@gongya I've never used it, but it seems to be related to IKEv1 remote access VPN connections.
It's uses a different command to NAT-T to configure. To enable IPsec over UDP, configure the ipsec-udp command with the enable keyword in group-policy configuration mode, as follows:
hostname(config-group-policy)# ipsec-udp {enable | disable }
hostname(config-group-policy)# no ipsec-udp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2023 11:04 AM
thanks so much !!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide