- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN with NAT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN with NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 02:59 AM
Hello Everyone,
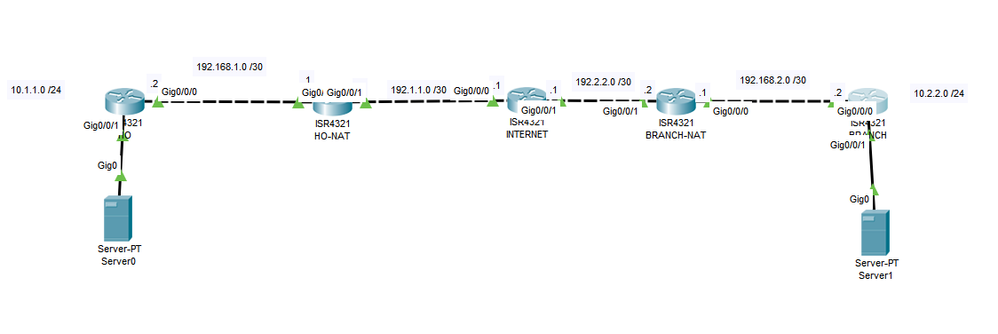
I'm trying to configure IPSEC thru NAT but it seems not it's not working. I've attached the file of packet tracer. I hope someone can help me with this.
Thank you
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 05:07 AM - edited 02-14-2020 05:18 AM
Hello, As per your diagram, i suppose that your HeadOffice Router is connected with internet via Gig 0/0/1 using IP 192.168.1.1 & your branch office router is connected over internet using Gig 0/0/1 using IP 192.168.2.1. We also suppose that HO and Branch office router can reach each other over these IPs, now your IPSEC configurations will be look like this.
R1-HO(config)# crypto isakmp policy 1
R1-HO(config-isakmp)# encr 3des
R1-HO(config-isakmp)# hash md5
R1-HO(config-isakmp)# authentication pre-share
R1-HO(config-isakmp)# group 2
R1-HO(config-isakmp)# lifetime 86400
R1-HO(config)# crypto isakmp key Cisco123 address 192.168.2.1
R1-HO(config)# ip access-list extended VPN-TRAFFIC
R1-HO(config-ext-nacl)# permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
R1-HO(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac
R1-HO(config)# crypto map CMAP 10 ipsec-isakmp
R1-HO(config-crypto-map)# set peer 192.168.2.1
R1-HO(config-crypto-map)# set transform-set TS
R1-HO(config-crypto-map)# match address VPN-TRAFFIC
R1-HO(config)# interface Gig 0/0/1
R1-HO(config- if)# crypto map CMAP
R2-Branch(config)# crypto isakmp policy 1
R2-Branch(config-isakmp)# encr 3des
R2-Branch(config-isakmp)# hash md5
R2-Branch(config-isakmp)# authentication pre-share
R2-Branch(config-isakmp)# group 2
R2-Branch(config-isakmp)# lifetime 86400
R2-Branch(config)# crypto isakmp key Cisco123 address 192.168.1.1
R2-Branch(config)# ip access-list extended VPN-TRAFFIC
R2-Branch(config-ext-nacl)# permit ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255
R2-Branch(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac
R2-Branch(config)# crypto map CMAP 10 ipsec-isakmp
R2-Branch(config-crypto-map)# set peer 192.168.1.1
R2-Branch(config-crypto-map)# set transform-set TS
R2-Branch(config-crypto-map)# match address VPN-TRAFFIC
R2-Branch(config)# interface Gig 0/0/1
R2-Branch(config- if)# crypto map CMAP
Now regarding your NAT requirements, It is most likely to be configured to provide Internet access to internal hosts. When configuring a Site-to-Site VPN tunnel, it is imperative to instruct the router not to perform NAT (deny NAT) on packets destined to the remote VPN network(s) and this can be done by inserting a deny statement at the beginning of the NAT access lists as shown below:
For Head office router:
R1-HO(config)# ip nat inside source list 100 interface Gig 0/0/1 overload
R1-HO(config)# access-list 100 remark -=[Define NAT Service]=-
R1-HO(config)# access-list 100 deny ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
R1-HO(config)# access-list 100 permit ip 10.1.1.0 0.0.0.255 any
R1-HO(config)# access-list 100 remark
And Site 2’s router:
R2-Branch(config)# ip nat inside source list 100 interface fastethernet0/1 overload
R2-Branch(config)# access-list 100 remark -=[Define NAT Service]=-
R2-Branch(config)# access-list 100 deny ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255
R2-Branch(config)# access-list 100 permit ip 10.2.2.0 0.0.0.255 any
R2-Branch(config)# access-list 100 remark
Please press star if you think it address your question or circle back with more details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 07:08 AM
Thank you for quick response. As per your recommendation I've added the
deny on my access-list but still the same issue. ACTIVE(Deleted) is the
status of ISAKMP. HEre is my config,
HO Config
---------------------------------------------------------
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
!
crypto isakmp key cisco123 address 192.2.2.2
!
crypto ipsec transform-set TSET esp-3des esp-md5-hmac
!
crypto map CMAP 1 ipsec-isakmp
set peer 192.2.2.2
set transform-set TSET
match address 101
interface GigabitEthernet0/0/0
ip address 192.168.1.2 255.255.255.252
duplex auto
speed auto
crypto map CMAP
interface GigabitEthernet0/0/1
ip address 10.1.1.1 255.255.255.0
duplex auto
speed auto
ip route 0.0.0.0 0.0.0.0 192.168.1.1
access-list 101 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
---------------------------------------------------------------
HO-NAT
----------------------------------------------------------------
interface GigabitEthernet0/0/0
ip address 192.168.1.1 255.255.255.252
ip nat inside
duplex auto
speed auto
!
interface GigabitEthernet0/0/1
ip address 192.1.1.2 255.255.255.252
ip nat outside
duplex auto
speed auto
!
ip nat inside source list 100 interface GigabitEthernet0/0/1 overload
ip nat inside source static udp 192.168.1.2 500 192.1.1.2 500
ip nat inside source static udp 192.168.1.2 4500 192.1.1.2 4500
access-list 100 remark NAT
access-list 100 deny ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
access-list 100 permit ip 10.2.2.0 0.0.0.255 any
ip route 0.0.0.0 0.0.0.0 192.1.1.1
--------------------------------------------------------------------
INTERNET
------------------------------------------------------------------
interface GigabitEthernet0/0/0
ip address 192.1.1.1 255.255.255.252
duplex auto
speed auto
!
interface GigabitEthernet0/0/1
ip address 192.2.2.1 255.255.255.252
duplex auto
speed auto
------------------------------------------------------------------
BRANCH-NAT
-----------------------------------------------------------------
interface GigabitEthernet0/0/0
ip address 192.168.2.1 255.255.255.252
ip nat inside
duplex auto
speed auto
!
interface GigabitEthernet0/0/1
ip address 192.2.2.2 255.255.255.252
ip nat outside
duplex auto
speed auto
!
ip nat inside source list 100 interface GigabitEthernet0/0/1 overload
ip nat inside source static udp 192.168.2.2 500 192.2.2.2 500
ip nat inside source static udp 192.168.2.2 4500 192.2.2.2 4500
ip route 0.0.0.0 0.0.0.0 192.2.2.1
access-list 100 remark NAT
access-list 100 deny ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255
access-list 100 permit ip 10.2.2.0 0.0.0.255 any
---------------------------------------------------------------------
BRANCH
---------------------------------------------------------------------
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
!
crypto isakmp key cisco123 address 192.1.1.2
!
!
!
crypto ipsec transform-set TSET esp-3des esp-md5-hmac
!
crypto map CMAP 1 ipsec-isakmp
set peer 192.1.1.2
set transform-set TSET
match address 101
!
interface GigabitEthernet0/0/0
ip address 192.168.2.2 255.255.255.252
duplex auto
speed auto
crypto map CMAP
!
interface GigabitEthernet0/0/1
ip address 10.2.2.1 255.255.255.0
duplex auto
speed auto
ip route 0.0.0.0 0.0.0.0 192.168.2.1
!
ip flow-export version 9
!
!
access-list 101 permit ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 10:47 AM
Please check your ACL on HO NAT router, ACL 100 Line 3, source IP network is in-correct you can even replace it with
access-list 100 permit ip any any
Please initiate some traffic and share debug logs.
debug crypto isakmp
debug crypto IPsec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 12:22 PM
Hello Muhammad,
I really appreciate your quick response, after some changes on my config the ISAKMP and IPSEC was up. As you can see on the IPSEC SA it's encrypting packet but not decrypting. So i tried to simulate on both side and saw the problem on the HO-NAT and BRANCH-NAT. The IP Address is not translated to it's Global IP Address. If I send a packet from 10.2.2.2 it will go until HO-NAT and be dropped.
By the way i remove this in my config,
ip nat inside source static udp X.X.X.X 500 X.X.X.X 500
ip nat inside source static udp X.X.X.X 4500 X.X.X.X 4500
and replace it with
ip nat inside source static X.X.X.X X.X.X.X
then the IPSEC was up.
ISAKMP:(1039):Old State = IKE_QM_I_QM1 New State = IKE_QM_PHASE2_COMPLETE
HO>
HO>
HO>
HO>en
HO#sh cr
HO#sh crypto isa
HO#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
192.2.2.2 192.168.1.2 QM_IDLE 1039 0 ACTIVE
IPv6 Crypto ISAKMP SA
HO#sh cr
HO#sh crypto ip
interface: GigabitEthernet0/0/0
Crypto map tag: CMAP, local addr 192.168.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.2.2.0/255.255.255.0/0/0)
current_peer 192.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 192.168.1.2, remote crypto endpt.:192.2.2.2
path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0/0
current outbound spi: 0x1F6E0A36(527305270)
inbound esp sas:
spi: 0x5AD50EB9(1523912377)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2000, flow_id: FPGA:1, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4525504/3340)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x1F6E0A36(527305270)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: FPGA:1, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4525504/3340)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide