- Cisco Community
- Technology and Support
- Security
- VPN
- Weak cipher suites for VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Weak cipher suites for VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2020 12:44 AM
Hello,
I use ASAv v9.12.3 for vpn handling.
I tested the certificate in the ssllabs.com and I got a score I do not like!!
It says among others that the cipher suites are weak and to disable them.
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) ECDH secp256r1 (eq. 3072 bits RSA) FS WEAK 256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) ECDH secp256r1 (eq. 3072 bits RSA) FS WEAK 128
I would like to ask what cipher suites I should use in their place?
Is there a recommendation?
When I change them in the ASDM will there be an impact on the connected users?
Thanks and regards,
Konstantinos
- Labels:
-
AnyConnect
-
Remote Access
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2020 01:34 AM
Hi,
The AES-GCM ciphers are more secure than AES-CBC, you should probably also consider using only TLS 1.2 and DTLS 1.2 (DTLS 1.2 requires AnyConnect 4.7+) as well. You would need to use a custom cipher list as the default tlsv1.2 "high" list contains the ciphers you do not wish to use.
ssl server-version tlsv1.2 dtlsv1.2
ssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-GCM-SHA384 AES256-GCM-SHA384"
ssl cipher dtlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-GCM-SHA384 AES256-GCM-SHA384"
If you need to back out, then preprend "no" and repeat the above commands.
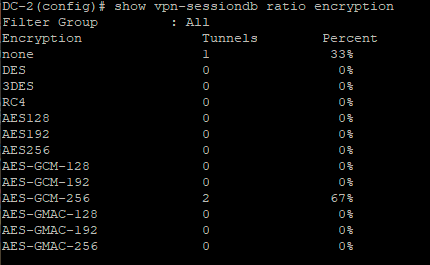
Before making the change, use the command show vpn-sessiondb ratio encryption and work out what encryption protocol your clients have currently connected using.
Make sure you are using at least AnyConnect 4.7, ideally 4.8 - determine this before you make the changes. If your client computers are using Windows 10 and AnyConnect 4.7/4.8, they are probably already connecting using AES-GCM as this is default, so you shouldn't have any issue changing the ciphers.
If you have trouble connnecting to ASDM after changing the ciphers, upgrade your java version - as your current version may not support TLS1.2.
Refer to this best practices guide for more information.
HTH
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide