- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Central Web Authentication (CWA) for guests with ISE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-11-2012 12:04 AM - edited 11-18-2020 02:59 AM
Introduction
There are multiple ways of doing Web Authentication on the WLC. The first one is Local Web Authentication. In this case, the WLC will redirect the HTTP Traffic to an internal or external server where the user will be prompted to authenticate. The WLC will then fetch this credentials (sent back via HTTP GET Request in case of external server), and make a radius authentication. In case of guest user, we need an external server (like ISE or NGS), as the portal can provide some feature like Device Registering, Self Provisionning, ...
The flow would be the following:
-User associate to the Web Auth SSID
-User starts its browser
-The WLC Redirect to the guest portal (ISE/NGS)
-The user authenticate on the portal
-The Guest Portal redirect back to the WLC with the credentials entered
-The WLC Authenticate the guest user via Radius
-The WLC Redirects back to the original URL.
That makes a lot of redirection. The new approach is to use Central Web Authentication. This works with ISE > 1.1 and WLC > 7.2.
The flow in this case would be:
-User associate to the Web Auth SSID
-User starts its browser
-The WLC Redirect to the guest portal (ISE)
-The user authenticate on the portal
-The ISE send a Radius Change Of Authorization (CoA - UDP Port 3799) to indicate to the controller that the user is valid, and eventually push radius attributes (ACL for example).
-The User is prompted to retry his original URL
Setup Used
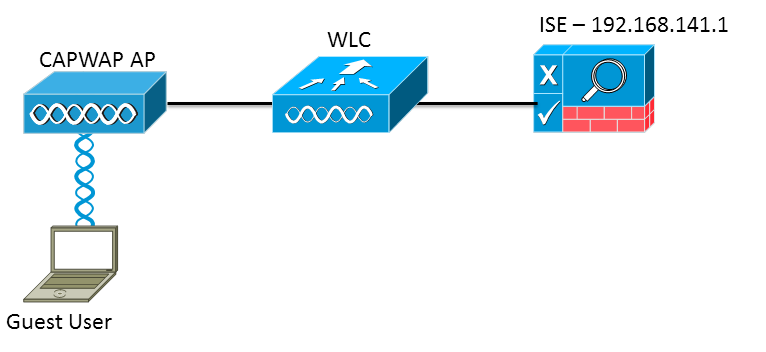
The version used are:
ISE: 1.1.1.268
WLC: 7.2.110.0
WLC Configuration
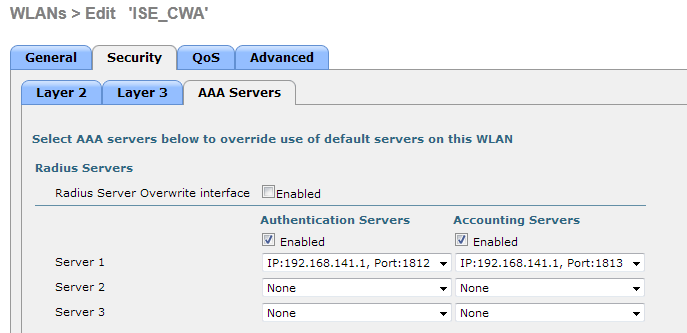
The WLC Configuration is pretty straight-forward. We uses a "trick" (same as on Switches) to get the dynamic authentication URL from the ISE (as it is using CoA, a session needs to be created, and the session ID is part of the URL). We need to configure the SSID to use MAC Filtering. We will configure the ISE to return an access-accept even if the mac address is not found, so that it will sends the redirection URL for all users.
In addition to this, we need to enable Radius NAC and AAA Override. The Radius NAC allows the ISE to send a CoA Request to indicate that the user is now authenticated and can access the network. It is also used for Posture Assessment, in which case the ISE would change the user profile based on posture result.
We need also to be sure that the radius server have RFC 3576 (CoA) enabled, which is by default.
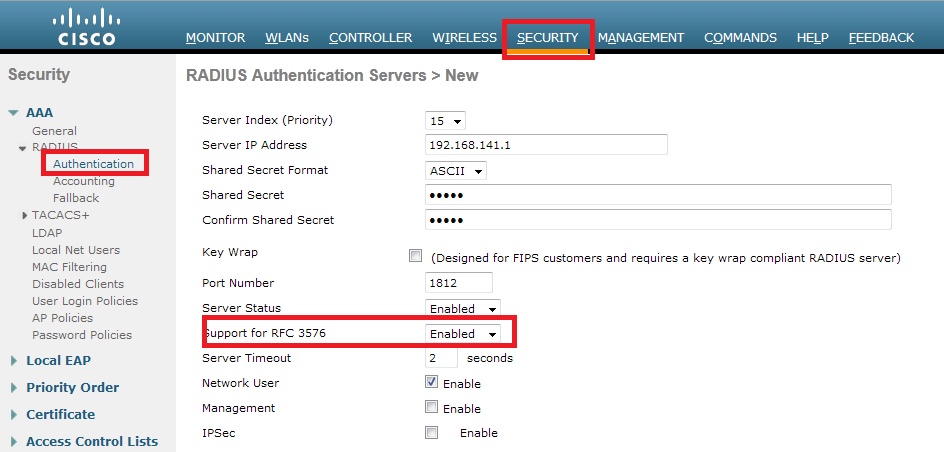
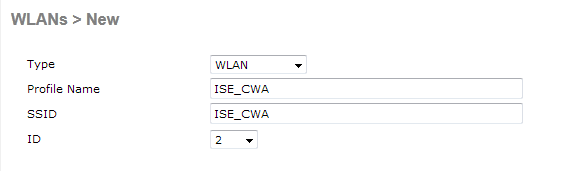
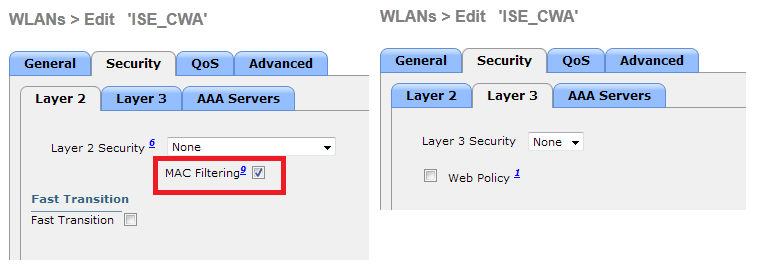
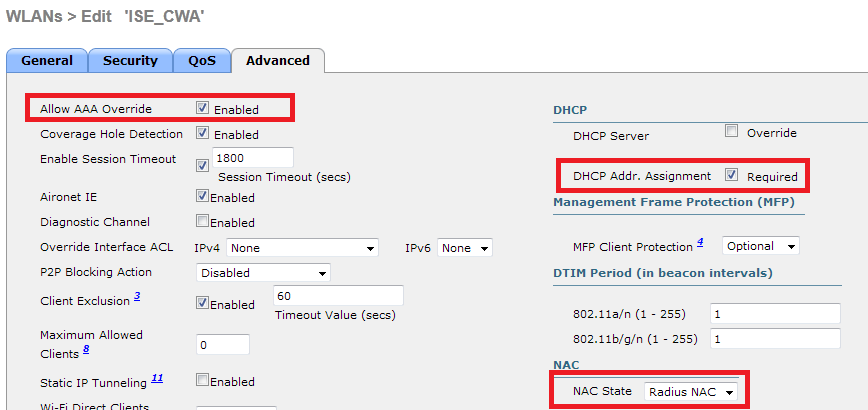
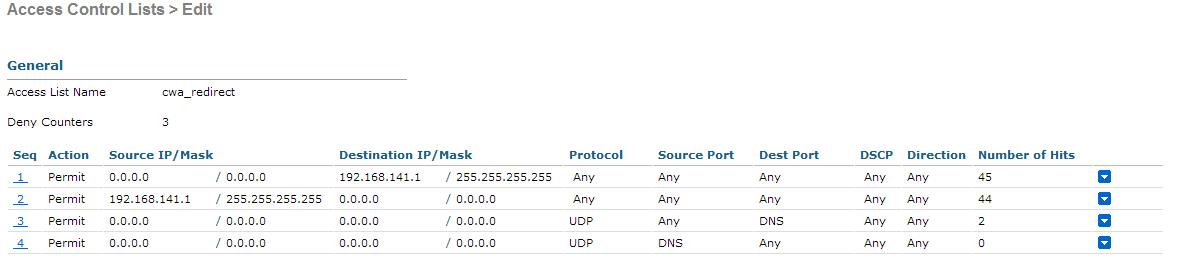
The final step is to create a Redirect-ACL. This ACL will be referenced in the access-accept of the ISE and will define what traffic should be redirected (denied by ACL), and what traffic shouldn't (permitted by the ACL). Basically, we need to permit DNS and traffic to/from ISE.
Everthing is now complete on the WLC. Let's configure the ISE
ISE Configuration
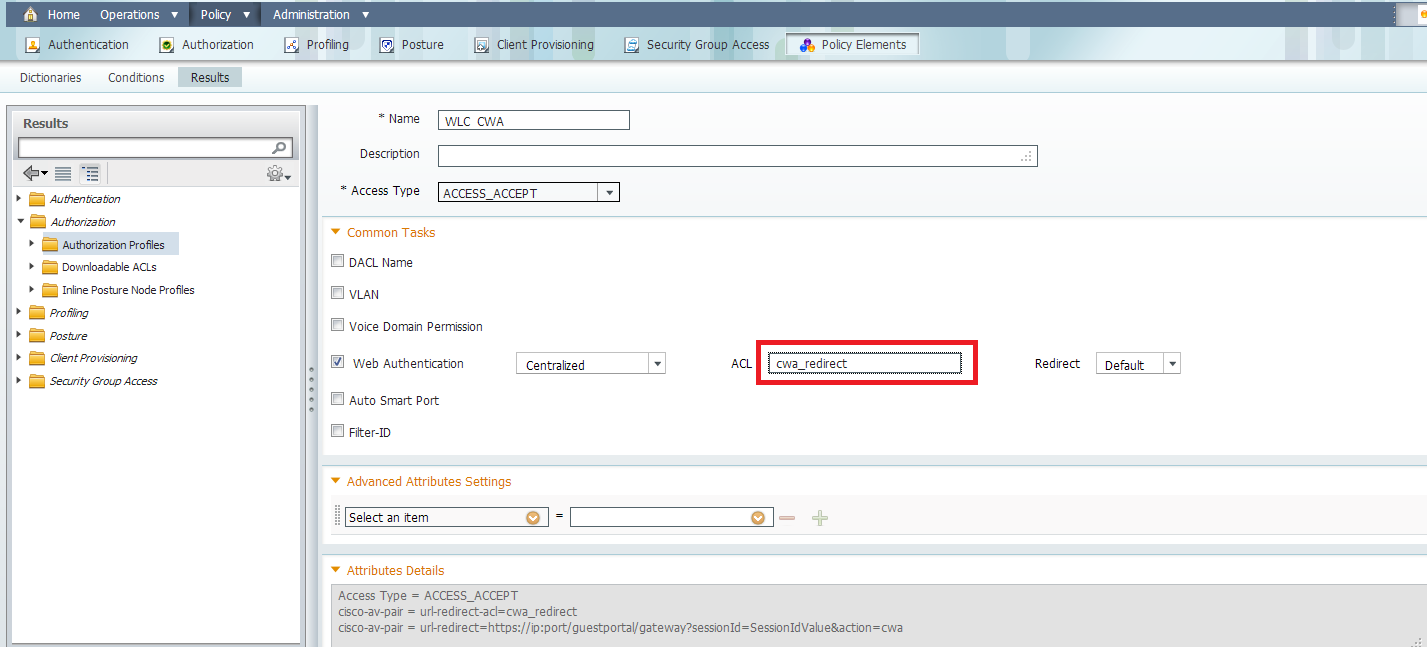
On the ISE, we need to make authorization profile, and then we can configure authentication and authorization. The WLC should already configured as a network device.
In the authorization profile, we need to put the name of the ACL has been created earlier on the WLC:
Now, we need to make sure the ISE is accepting all the MAC Authentication from the WLC and return the profile:

We can use the Built-In Wireless MAB condition, which match :
-Radius:Service-Type : Call Check (Mac Authorization use Call Check on WLC and Switches).
-Radius:NAS-Port-Type: Wireless - IEEE 802.11
Now, we need to configure the authorization. One important thing to understand is that there will be 2 authentication / authorization:
-One when the user associate to the SSID, and when we need to return the cwa profile
-Another when the user authenticate on the web portal. This one will match the default rule (internal users), in my situation (you can configure it as you want). What is important is that the authorization part doesn't match the CWA Profile again, otherwise we would have a redirection loop. We can use the attribute "Network Access:UseCase Equals Guest Flow" to match this second authentication.
The result looks like this:
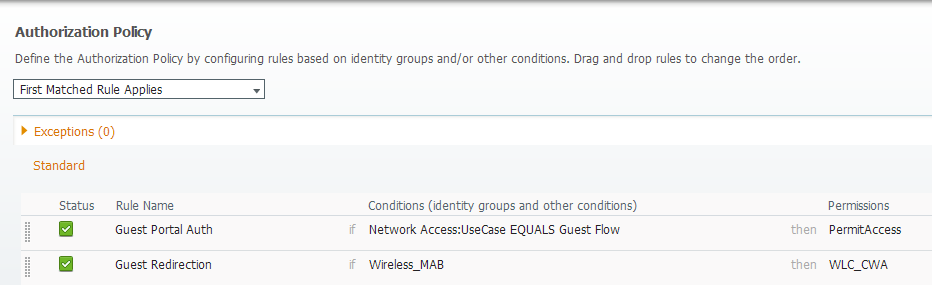
Test
Once we associate to the SSID, we can see the auth in the ISE page:
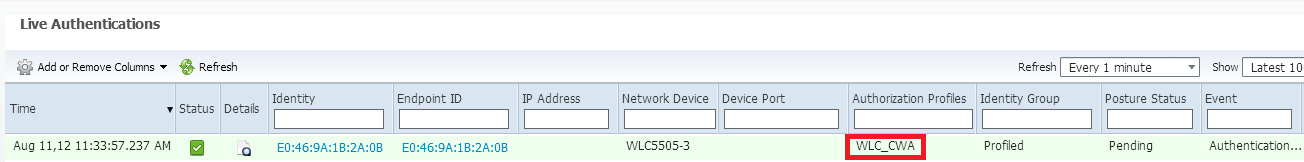
And if we check the client details in the WLC, we can see the Redirection URL and ACL are applied:
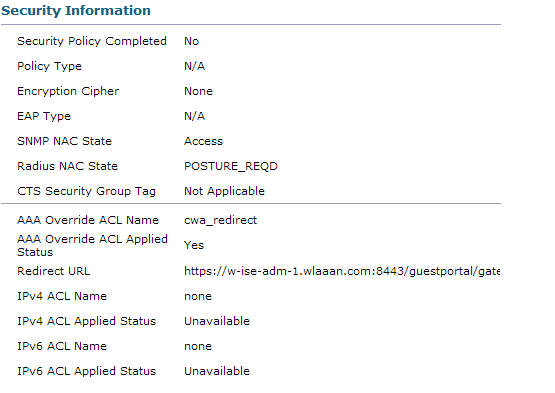
Now, when we open any address on the client, we are redirected to our ISE (be careful to have DNS setup correctly).
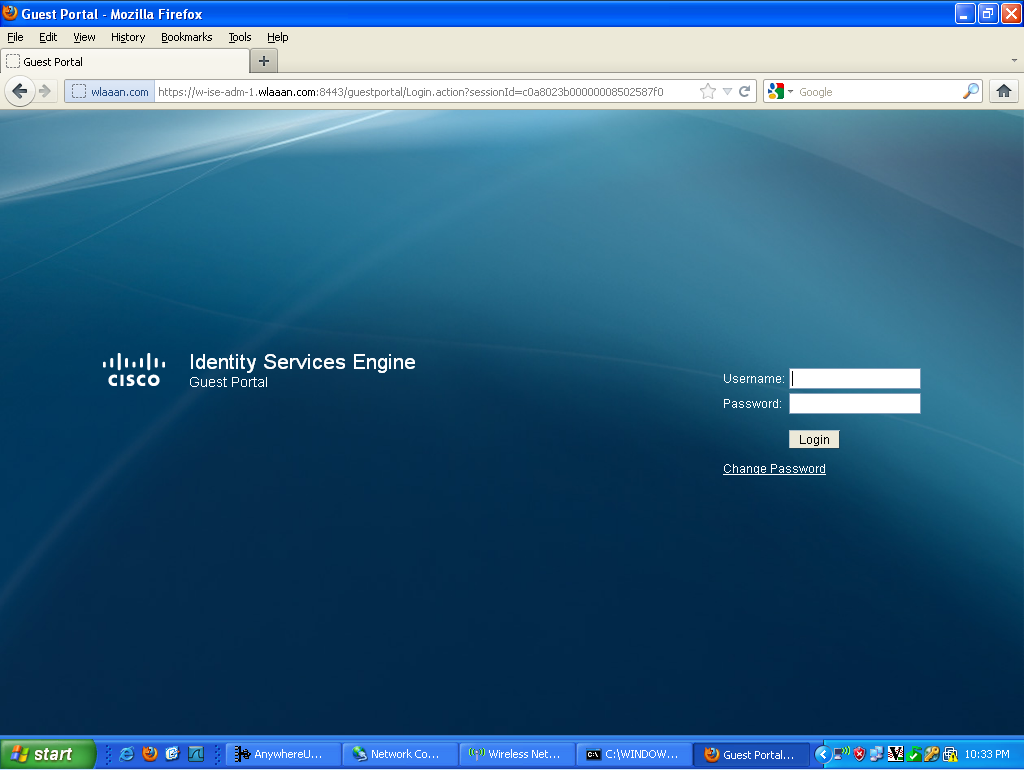
Then the user needs to accept the policies, and then it will be granted access to the network.
If we look back at my ISE, we can now see the authentication, the change of authorization, and that the profile applied is permitAccess:
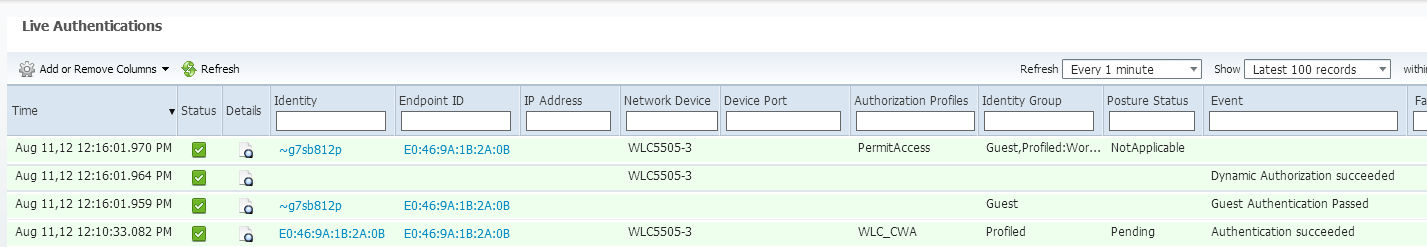
On the controller, the Policy Manager State and Radius NAC State should change from "POSTURE_REQD" to "RUN"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, i would like to know if it's possible to make https redirection in a WLC with CWA and ISE?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
Yes that is possible with WLC 8.0 and later. You need to configure
config network web-auth https-redirect enable
And that the Redirect ACL is adjusted.
More Info here:
https://supportforums.cisco.com/document/12398536/understanding-https-redirect-over-web-auth
And
http://www.cisco.com/c/en/us/support/docs/wireless-mobility/wlan-security/115951-web-auth-wlc-guide-00.html#anc7
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Bastien.
Thanks for your soon reply, i tested the command, but our client complains about the certificate error with the https redirection.
On the link you provide says that it's unavoidable, but just to confirm, is there any posible way to fix the certificate error? otherwise we gonna have to unmount the ise guest solution because of that.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Carlos,
This is not technically possible. When a device intercept SSL Connection, it has to use its own certificate which is self signed, and event it would be a CA Signed one, would not match destination website, so you will always get a SSL Warning when you want to intercept SSL connection.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So there is just a Radius communication between foreign and ISE ?
I thought with CWA the Anchor WLC handles the Radius Authentication ?
If no is there any communication between ISE and Anchor WLCs ?
Greetings
Philip
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Philip,
Foreign handles Radius, and Anchor web redirection, so it doesn't really communicate with ISE, but it rewrites HTTP Packet and traffic will go out of the anchor, with IP address of guest client.
You can check this document which is a bit more updated and complete:
http://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/115732-central-web-auth-00.html#anc11
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, Bastien,
Perhaps you can help me with understanding the Authentication Process in more detail for CWA. The setup involves:
Anchor WLC in the Outside network.
Anchor WLC owning the Guest WLAN.
Foreign WLC in the Inside network.
ISE in the Inside network.
ISE using MAB.
Sponsor Portal on ISE.
Client credentials on ISE.
1) Client connects to SSID (Layer 1).
2) Client uses DHCP.
*3) (Anchor?)(Foreign?) WLC intercepts DHCP request, and forwards MAC of client to ISE.
*4) ISE uses MAB and sends the result back to the (Foreign? Anchor?) WLC.
*5) (Anchor?)(Foreign?) WLC now relases the DHCP information to the client (assuming the WLC is the DHCP server. Might work differently for DHCP relay?).
6) Client opens a browser and enters http://www.cisco.com into the URL box.
*7) Client machine performs a DNS request -- this traffic is NOT redirected to the ISE, right?
*8) (Real) DNS server replies with the DNS-response.
*9) Client attempts TCP handshake with cisco.com over TCP/80.
*10) TCP handshake succeeds (directly with cisco.com web server).
*11) Client sends a HTTP/GET request to cisco.com.
*12) (Anchor?)(Foreign?) WLC intercepts HTTP/GET, and redirects client to ISE portal.
13) Client starts a TCP handshake with ISE over port 8443 (default).
14) After success, the client sends an HTTP/GET request for the Sponsor Portal web page.
15) ISE responds with the web portal, specifically the login page.
16) Client enters credentials into Portal.
*17) Since the ISE is the owner of the client credentials, no RADIUS comms are sent (yet). ISE authenticates the client locally, right?
*18) Upon successful authentication with the ISE, the ISE sends a CoA over RADIUS communication to the (Anchor?)(Foreign?) WLC, and also sends the policy ACL configured for client network access control.
*19a) The (Anchor?)(Foreign?) WLC updates the client attributes with the CoA and new ACL to apply (at this point, no longer using the redirect ACL).
19b) The ISE sends the client to the "success" page after login.
20) Client is now fully authenticated and can do whatever he wants, within the permissions of the Policy ACL of course.
In particular, the items marked with (*) are unclear for me, as I cannot find that kind of detailed documentation anywhere.
Any help/clarification on this is appreciated.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Zehel,
Here is the flow:
-1 Client associates to SSID. The Foreign WLC will make MAC Authentication at this time. ISE will reply with access-accept containing URL Redirect and the redirection ACL
-2 Foreign WLC sends Mobility Announce to the Anchor and client gets Anchored to the anchor in WEBAUTH_REQD state
-3 Client does DHCP and get IP address. Unless explicitely denied, DHCP and DNS are allowed through redirect ACL
-4 Client makes HTTP Request. Foreign forwards it to anchor.
-5 Anchor verify if this HTTP request can be allowed or redirected, normally it will be redirected to ISE. Anchor impersonate the destination server and sends HTTP 302 redirection to ISE Address.
-6 Client access ISE URL that contains unique session
-7 After successful login, ISE sends CoA to foreign
-8 Mobility announce is made by foreign to let anchor know client should be in run state
-9 Traffic is still forwarded from foreign to anchor, and goes out of anchor wlc
Hope this is clear.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Bastien, thanks for the quick response!
Yes -- that clears up pretty much most of my questions. Just 1 more if I may about the TCP 3-way handshake:
Between your steps #3 and #4 (between the DNS resolution and the HTTP GET request), does the WLC also intercept the TCP handshake for the initial HTTP session? I was inspecting our firewall logs, and never did see the 3-way handshake between client<>website, so I presume the WLC also intercepts the 3-way handshake by impersonating the website's real IP.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes, WLC intercept TCP Sessions.
Catalyst switches does the same if they have an SVI, otherwise they intercept and forward the request to the gateway:
http://www.cisco.com/c/dam/en/us/products/collateral/ios-nx-os-software/identity-based-networking-services/app_note_c27-577494.doc/_jcr_content/renditions/app_note_c27-577494-03.jpg
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Bastien,
many thanks for that great threat which makes live really easier and more clear ;-)
Can you tell me something about guest session caching ? How is it working? Is it made by just saving the mac address or can i also use some kind of cookie to do it ? Do i have to configure or change anything on ISE to enable it ? I am using 1.4
Greetings
Philip
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You are welcome :) If it prevent to open couple of TAC case this is win/win.
Regarding your question though I am not sure what you mean. ISE creates a unique session ID for each authentication being guest, dot1x, ...
This session ID is encoded in Radius state attribute for dot1x, or in the URL for guest authentication.
When guest is roaming, WLC reuses the state attribute in MAB requests, and ISE also correlates with mac address.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You´re right ;-) That´s definitely win/win.
I think more in direction of how long is a guest user session cache until he gets redirected to the webportal again ?
Greetings
Philip
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Basically ISE will terminate the session when it receives accounting stop (with maximum duration of 1 week), or 1 hour after session start if no accounting is received.
WLC will send accounting stop in various scenarios (non exhaustive):
-Session-timeout / idle-timeout values
-Client disconnection (user log off, screen power off of smartphone) only if client MFP enabled and supported by client
-Inter WLC Roaming (see CSCue50944 Sev6 - CWA Mobility Roam Fails to Foreign with MAC Filtering BYOD)
-...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So there how can i prevent my guests from logging in more then once per day ?
I heard something abou using cookies when creating the guest page via Online Portal Generator ?
I mean this cannot be the result to login everytime again when unlock the iphone !?
Greetings
Philip
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: