- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- How to configure Wireless Lan Controller (WLC) for Lightweight Directory Access Protocol (LDAP) auth...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-22-2012 11:16 PM - edited 11-18-2020 02:59 AM
Introduction
What is LDAP?
Lightweight Directory Access Protocol is ued to access directory servers. A directory server is a hierarchical, object oriented database (DB) (try to stay awake!). A simple example is the telephone directory, which consists of a list of names (of either persons or organizations) organized alphabetically, with each name having an address and phone number associated with it. Objects contain data comprised of attributes which are a set of key/value pairs. Refer to a DB as a tree. Distinguished Name (DN) is a unique name used to refer to a particular object in the DB tree. A DN is not an object!
A base DN is the base of the DB and is most commonly a DNS domain.
cn - Common Name
ou - Organizational Unit
dc - Domain Component
Containers – containers, OU’s, or domains and can “contain” other objects like user objects, group objects, and computer objects.
So for a user named John Smith…
cn=John Smith,ou=East,dc=company,dc=com - Distinguished Name for the user .
cn=John Smith - Relative Distinguished Name
dc=company,dc=com - DNS domain name (company.com)
ou=East - Organizational Unit where user "John Smith" resides
Default MS Containers
The default CN=Users and CN=Computers containers that are created when Active Directory is installed are not organizational units (OUs). Objects in the default containers are more difficult to manage because Group Policy cannot be applied directly to them. New user accounts, computer accounts, and security groups that are created by using earlier versions of user interface and command-line management tools, such as the net user and net computer commands, the net group command, the netdom add command where the /ou command is either not specified or supported, or Windows NT 4.0 tools such as User Manager for Domains, do not allow administrators to specify a target organizational unit and therefore create these objects in either the CN=Computers container or the CN=User container by default.
So if all of the users are in the “Users” Container, be aware that it would be CN=Users (the common name for the container Users) and not OU=Users.
How do I know what to query for?
The hardest part of this is configuring the LDAP server parameters correctly on the WLC. Our documents make a lot of assumptions that someone not familiar with LDAP will not understand right away. Use an LDAP browsing tool to get this information
LDAP Tools
It is important to have some sort of LDAP browsing tool. You can download lots of free LDAP browsers from the Internet. Examples include LDP which is included on the MS Server CD in the support\tools dir (or just Google it) as well as LDAP Admin by SourceForce http://ldapadmin.sourceforge.net/download/ldapadmin.html (AAA uses this one a lot).
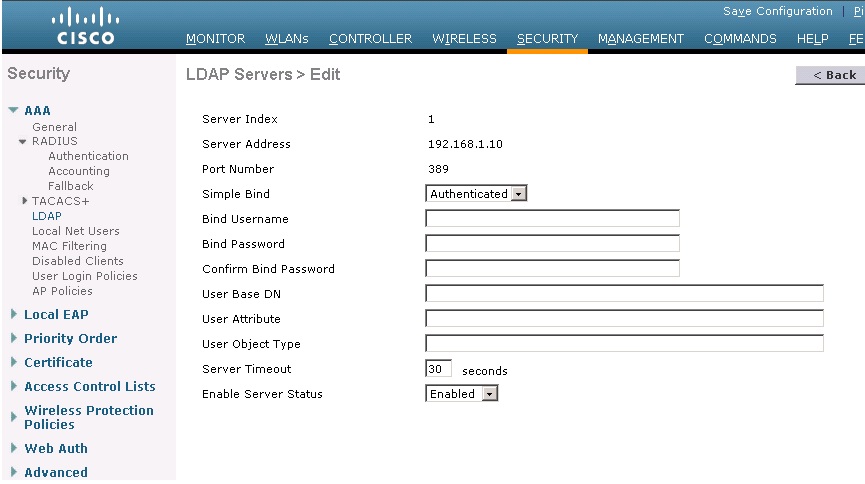
You can also do an anonymous bind, but almost no one does that.
Using LDP
Most want authenticated bind so that is what we are going to do! Once LDP is installed, you can just go to START>Run and type ‘ldp’.
You then want to select Connection>Bind
Have the customer bind using domain admin account credentials.
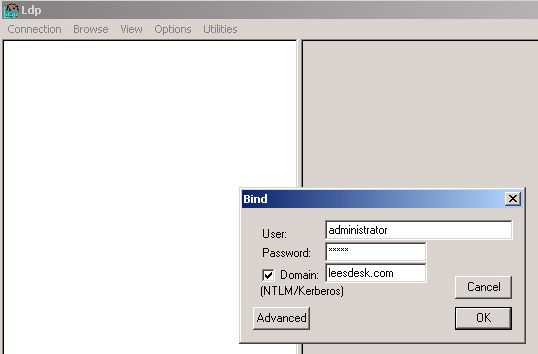
Once they have done that, you should see a screen similar to the following
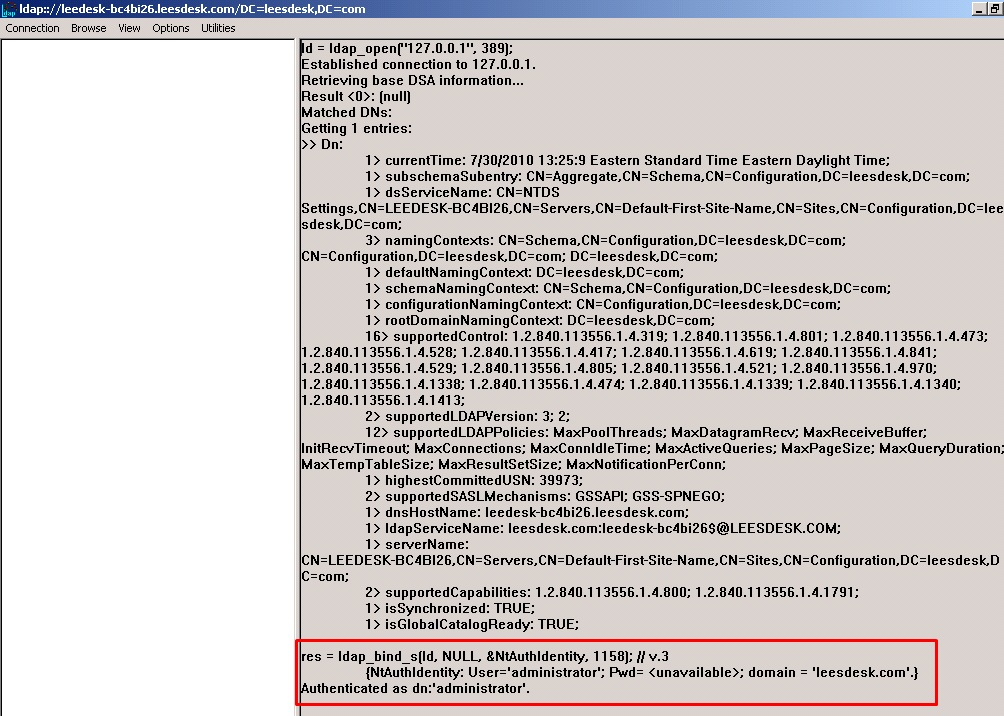
Then select View>Tree and enter the correct Base DN and click OK.
In this example, the Base DN is DC=leesdeck, DC=com.
So if the customer’s AD setup is ‘company.com’ then the Base DN would be DC=company, DC=com.
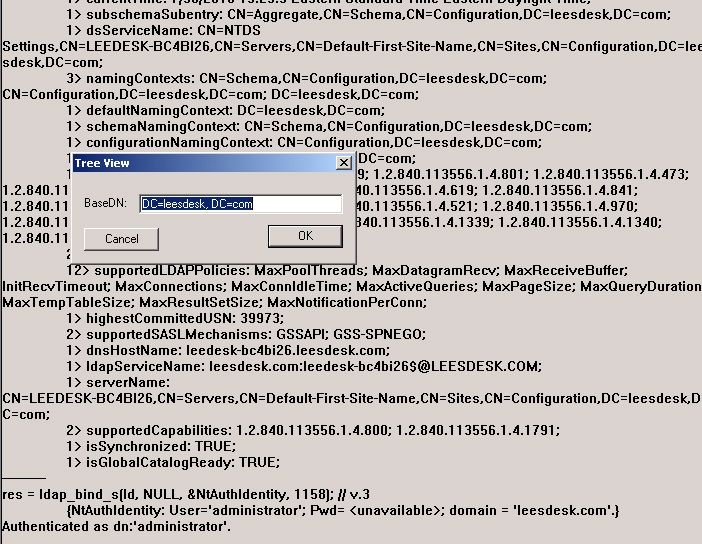
Once you have done that, you should see the Base DN in the upper left-hand side of LDP and be able to expand it out to find where the account you are going to use to bind to the LDAP server on the WLC.
In this example, we are using an account called ‘ldap’.
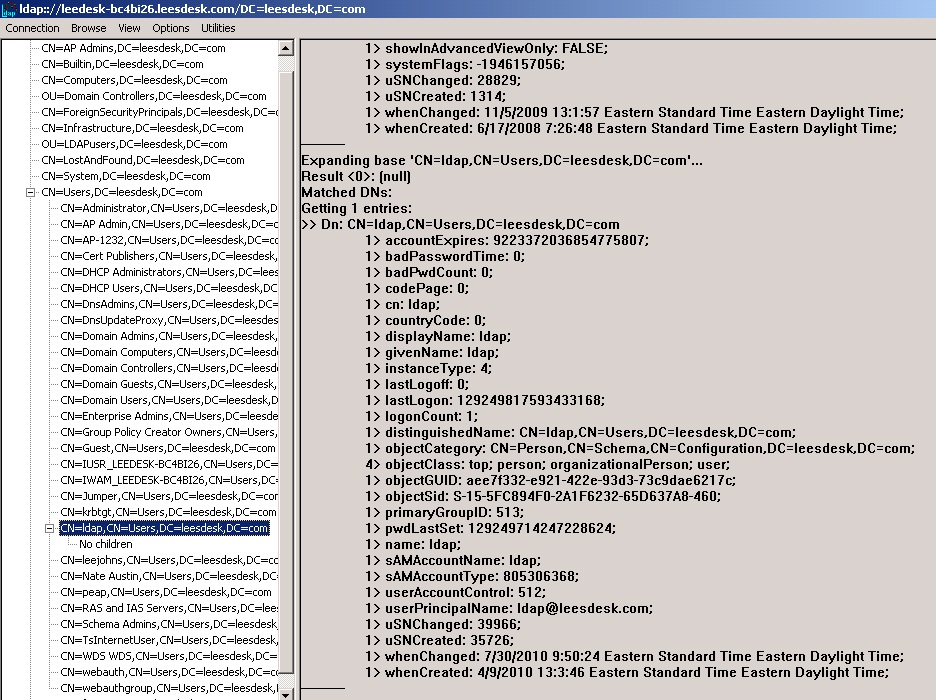
From this, we can see that the account resides under Users. Again, notice that Users is a CN and not an OU.
We know the base DN for the users is CN=Users,DC=leesdesk,DC=com.
A common user attribute is the sAMAccountName. Case Sensitive!!!!
Object type is Person (notice in the ldp output is says objectClass.
You could use other attributes and object types, but these work.

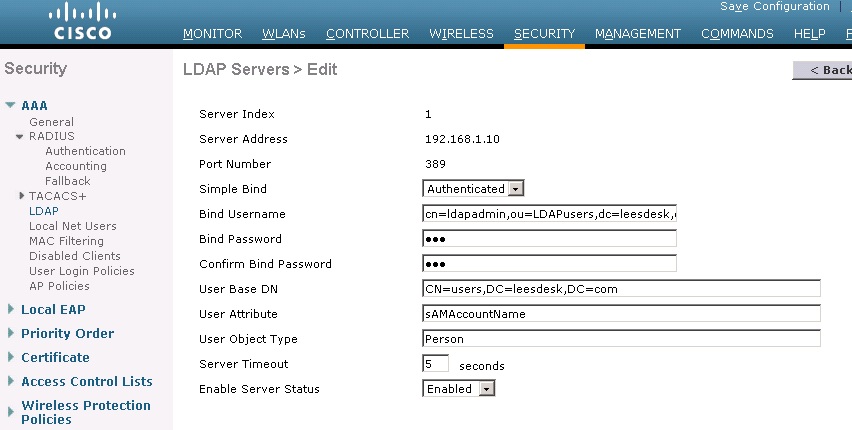
What if I want to bind with an account that is not in the same container as my users?
You need to modify the bind username to reflect the location of the binding account
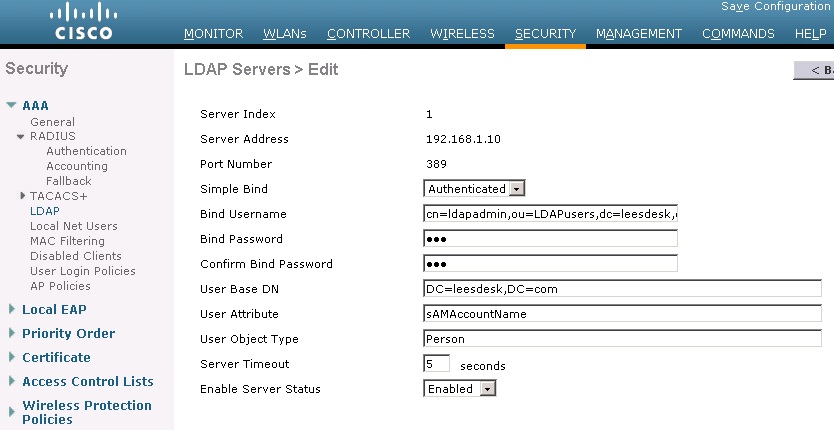
What if I have users in different containers? Do I have to have all of my wireless LDAP users in the same container?
No, you can search the base DN
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hello:
I am implementing WEB AUTH with LDAP in a Cisco 2500 WLC version 7.0, I could help with the syntax (user base DN) in order to reach every user in the next tree active directory
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
LDAP not connecting followed all the steps of the tutorial. help me friend
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How do you allow multiple user attributes; in other words a user might choose to enter sAMAccountName or mail so how to you make it match the first one; then if it fails the second one and only then produce auth failure? Listing multiple LDAP servers with different user attributes does NOT work!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
there are missing steps about how to associate ldap server to wian also what we have to do in the wireless client in order to get connected to this wlan.... please complete your tutorial!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello .... Did anyone get this working? I am having such a hard time getting this to work.
Any pointers will be great. Thanks!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
of course not; this tutorial is defective. I did get it to work but it ONLY authenticates on ONE LDAP attribute such as sMAccountName or ProxyAddress or whatever else you pick which is stupid and useless. Most any other non-Cisco WLC will parse multiple attributes and accept them as the end-user could put any crazy thing such as e-mail alias; APN (account principle name) or who knows what else but still credible attributes associated with one's account. All but ONE will fail with Cisco. So in summary -- good luck. If you have a specific question I would be happy to try to help.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for your reply ... If you could please share the steps on how you got it working with sMAccountName, not really flexible but at least we can get it going.
Thanks again.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello bbiandov,
Just wondering if you are still able to share the process you followed for getting the sMAccountName to work.
Thanks,
Alberto
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Alberto
Sure, so the setup is simple: web auth against AD. That means once the user joins SSID the first web page they attempt to access re-directs to the WLC login screen. Here they provide APN (account principle name). You get that from AD. It is NOT the user's e-mail address but it could be based on how you populate your AD.
NO special software on the AD side. WLC is simply pointed to the IP of one of the DCs.
YOU MUST provide credentials of an admin account so that WLC can bind. It will not just work. You see that on the screen shot
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks ... I continue to get the following error every time I attempt to authenticate. Is it complaining about the bind account or my credentials?
Apr 06 17:49:17.653: [ERROR] ews.c 871: ewsRun: Bad State - should be suspended: 0x0
*ewmwebWebauth1: Apr 06 17:49:17.652: #LOG-3-Q_IND: ldap_db.c:1067 Could not connect to LDAP server 1, reason: 49 (Invalid credentials).[...It occurred 2 times.!]
*LDAP DB Task 1: Apr 06 17:49:17.647: #AAA-3-LDAP_CONNECT_SERVER_FAILED: ldap_db.c:1067 Could not connect to LDAP server 1, reason: 49 (Invalid credentials).
Previous message occurred 2 times.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So it sounds like either the account/password which is specified as the LDAP bind account isn't correct or the account which you provide during the web portal login at WLC isn't correct. One or the other or both.
Both must be correct for the thing to work!
Or the path (the base DN) to the account object isn't correct; remember that the path to account must be accurate; that means OU= ...etc
There isn't any magic to this; it is very simple as long as the 2 accounts match. Try right clicking on the accounts in ADUC and then go to the property of the object to copy its location and account principle name
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks ... I think the issue is with the Web Auth configuration, since I am not getting any binding error. I am going to have the network admin double the config, since I saw noticed some funky things. I will write back once we figure out what the issue is. I notice the whole Web Auth has many moving parts.
Thanks again!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I found the issue to be related to the container where the service account was located. It appears it was too deep into AD tree directory, so it was not authenticate properly. Once I moved it up, it worked. Thanks for your help!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
is it possible to call multiple OU in a single LDAP server configuration, something like Multiple OU User Search Base
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: