- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- How to use Authorization Profile for different WLAN SSID?
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-26-2013 07:16 AM - edited 11-18-2020 03:05 AM
Introduction
In this document, we will discuss scenario where user is "Trying to setup the two different authorization profiles for two different WLAN SSID users".
Problem Description
We have two valid users: user1, user2, they both may use SSID 1 and SSID 2 which is broadcasted in all areas. (area 1, Area 2, area 3)
In area 1, only user1 allows to login SSID 1 and SSID 2.
In area2, only user2 can login SSID1 and SSID2.
In area 3 allows them all for SSID 1 and SSID2.
Problem Category
Wireless
Problem Subcategory
Cisco Wireless LAN Controller (WLAN)
Cisco ACS (Access Control Server)
Software
WLC running 7.x
ACS 4.x
Hardware
Wireless LAN - WLC-5500
Solution
WLC can send the SSID as part of the Called station ID attribute:
(Cisco Controller) >config radius callStationIDtype ?
ipaddr Sets Call Station Id Type to the system's IP Address
macaddr Sets Call Station Id Type to the system's MAC Address
ap-macaddr-only Sets Call Station Id Type to the AP's MAC Address
ap-macaddr-ssid Sets Call Station Id Type to the format <AP MAC address>:<SSID>
This can be used later in a NAR policy in ACS, with restrictions per user or group
There is a documented config example here:
Restrict WLAN Access based on SSID with WLC and Cisco Secure ACS Configuration Example
Logs
When user made the suggested changes in the configuration: WLC radius callStationidType from ipaddr to ap-macaddr-ssid, the radius summary did not show the correct call station id type:
The call station id type became undefined.
Before
(WLC-5500) >show radius summary
Vendor Id Backward Compatibility................. Disabled
Call Station Id Case............................. lower
Call Station Id Type............................. IP Address
Aggressive Failover.............................. Enabled
Keywrap.......................................... Disabled
After:
(WLC-5500) config>radius callStationIdType ap-macaddr-ssid
(WLC-5500) config>end
After
(WLC-5500) >show radius summary
Vendor Id Backward Compatibility................. Disabled
Call Station Id Case............................. lower
Call Station Id Type............................. Undefined
Aggressive Failover.............................. Enabled
Keywrap.......................................... Disabled
More Information
This is known bug, fixed on 7.0.116.0: CSCti02734 J-MR-Radius CallStationIdType show undefined for ap-macaddr-ssid
Network Setup
In this example setup, WLC is registered to the LAP. Two WLANs are used. One WLAN is for the Admin department users and the other WLAN is for the Sales department users. Wireless client A1 (Admin user) and S1 (Sales user) connect to the wireless network. You need to configure the WLC and the RADIUS server in such a way that the Admin user A1 is able to access only the WLAN Admin and is restricted access to the WLAN Sales and the Sales user S1 should be able to access the WLAN Sales and should have restricted access to the WLAN Admin. All users use LEAP authentication as a Layer 2 authentication method.

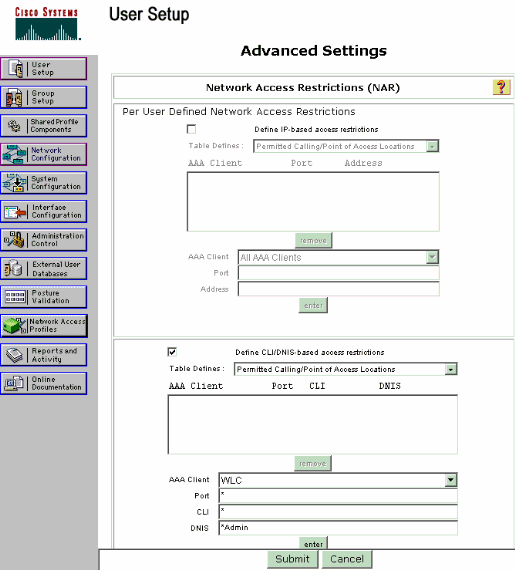
Information on NAR
Cisco Secure ACS supports two types of NAR filters:
- IP-based filters—IP-based NAR filters limit access based upon the IP addresses of the end-user client and the AAA client. Refer to About IP-based NAR Filters for more information on this type of NAR filter.
- Non-IP-based filters—Non-IP-based NAR filters limit access based upon simple string comparison of a value sent from the AAA client. The value can be the calling line ID (CLI) number, the Dialed Number Identification Service (DNIS) number, the MAC address, or other value that originates from the client. For this type of NAR to operate, the value in the NAR description must exactly match what is sent from the client, including whatever format is used. For example, (217) 555-4534 does not match 217-555-4534. Refer to About Non-IP-based NAR Filters for more information on this type of NAR filter.
If you use RADIUS, the NAR fields listed here use these values:
- AAA client—The NAS-IP-address (attribute 4) or, if NAS-IP-address does not exist, NAS-identifier (RADIUS attribute 32) is used.
- Port—The NAS-port (attribute 5) or, if NAS-port does not exist, NAS-port-ID (attribute 87) is used.
- CLI—The calling-station-ID (attribute 31) is used.
- DNIS—The called-station-ID (attribute 30) is used.
Refer to
for more information on the usage of NAR.Since the WLC sends in the DNIS attribute and the SSID name, you can create per-user SSID restrictions. In the case of the WLC, the NAR fields have these values:
- AAA client—WLC IP address
- port—*
- CLI —*
- DNIS—*ssidname
Reference
Restrict WLAN Access based on SSID with WLC and Cisco Secure ACS Configuration Example
This document was generated from the following discussion: How to use authorization profile for different WLAN SSID?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: