- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- OEAP 602 Remote LAN 802.1x (Port 4) with Wired IP Phone and Laptop behind the IP Phone
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-09-2013 07:20 AM - edited 11-18-2020 03:01 AM
Introduction
OEAP 602 Remote LAN 802.1x (Port 4) with Wired IP Phone and Laptop behind the IP Phone
Components Used
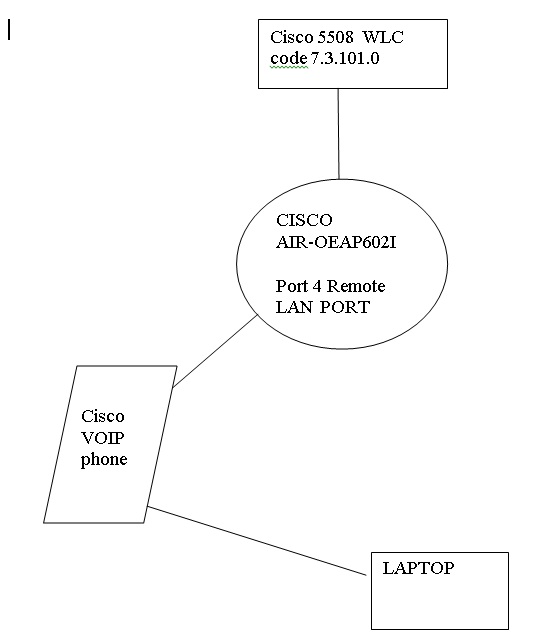
1. WLC 5508 running 7.3.101.0
2. OEAP 602I
3. Windows 7 Client
4. Cisco IP Phone 7975
5. ACS 5.2
Topology
Configuration
STEP 1:
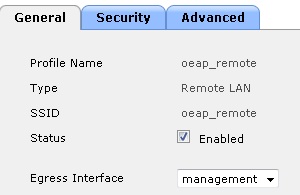
Creating a Remote LAN for OEAP Wired Clients (Port 4)

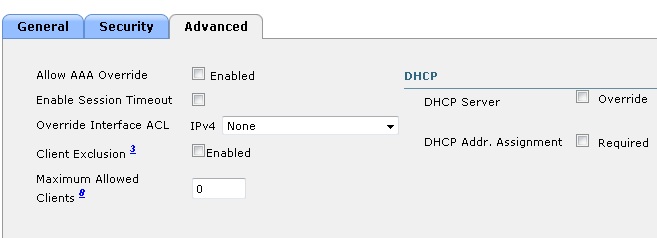
STEP 2: Setting up wired ip phone for 802.1X authentication
On the phone go to Settings > Security Configuration > 802.1X Authentication > Device Authentication > Enabled
you do not need to enable password for EAP-MD5
the Phone does EAP-TLS authentication
STEP3: Getting chained cert for the Cisco 7975 phone for EAP-TLS authentication
Note: Set the remote LAN to no security. Let the phone grab an ip address and register to the call manager. From the call manager enable the web mode. Navigate to the https page of the phone and grab the device cert of the phone using your web browser.
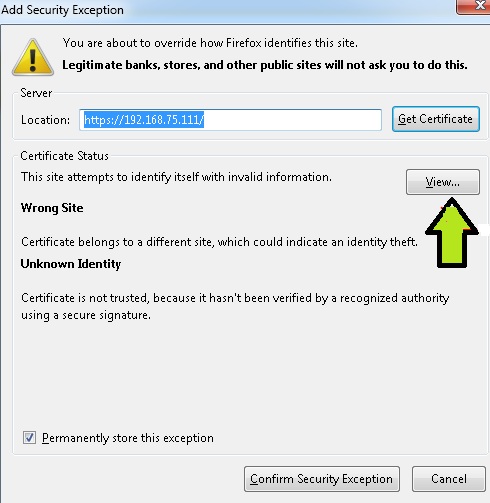
Click on the Details tab and hit Export
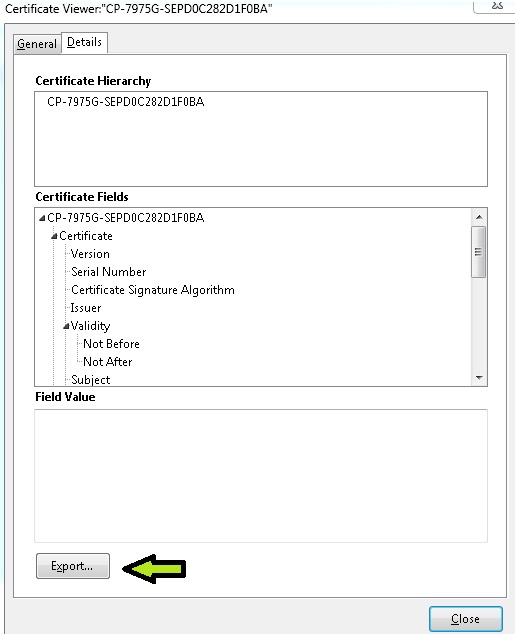
Save the cert on the local machine
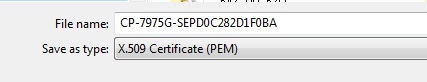
Open the cert by double clicking on it and Click on the 'Certification Path'
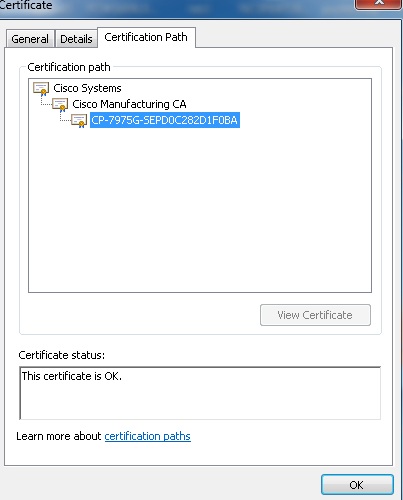
you can see the chained cert of the device. you already have the device cert. From this view save the Intermediate root and the Root CA cert.
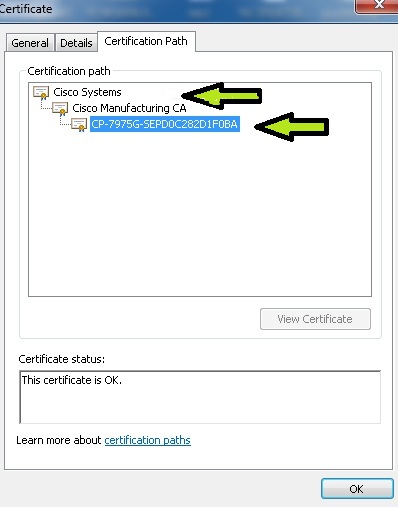
Now you have a 3 certs, CP-7975G-SEPD0C282D1F0BA, Cisco Manufacturing CA and Cisco Systems.
STEP 4: Import these certs on the ACS Certificate Authorities for EAP-TLS authentication of 7975 IP Phone.
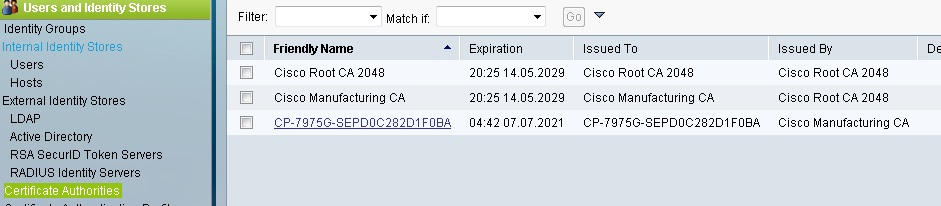
When you add the cert check the 'trust for Client with EAP-TLS' option
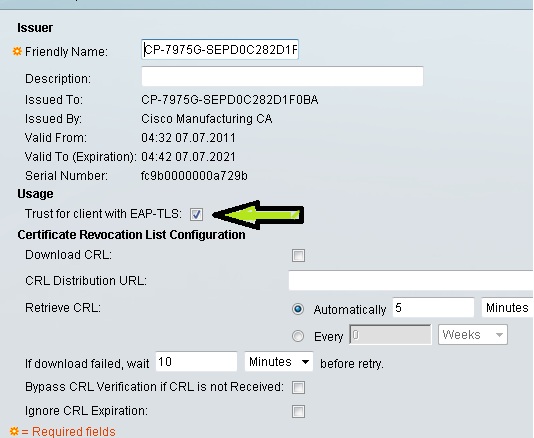
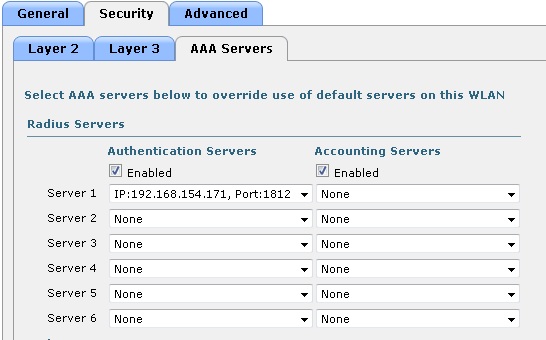
STEP 5: Configuring Access Policies on ACS
From Service Selection Rules check Rule based result selection.
I have configured Rule 1 for Radius with service set to Default Network Access and Rule 2 for TACACS with service set to Default Device Admin
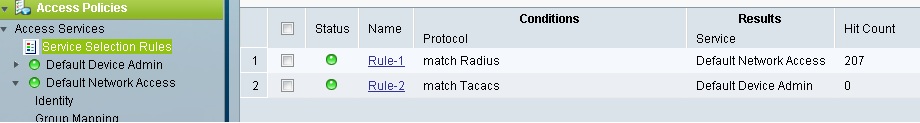
Under Default Network Access
Allow the necessary protocols
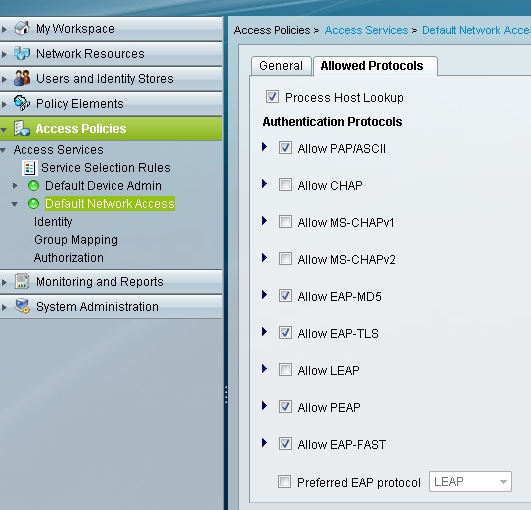
Select Default Network Access > Identity and click on Rule based result selection
Hit Customize to add 'EAP Authentication Method' and 'EAP Tunnel Building Method'
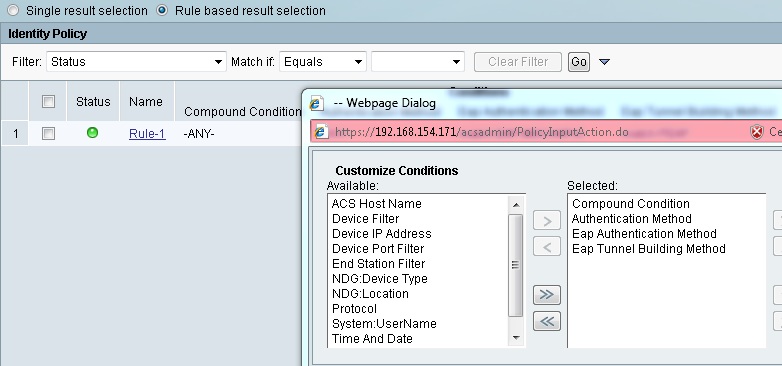
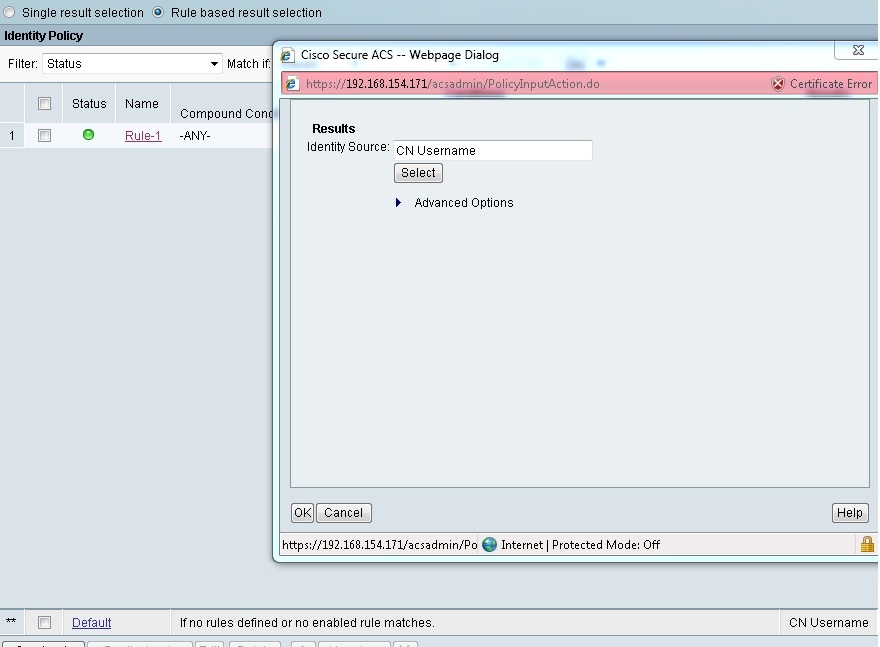
Create a new Rule which matches PEAP and MSCHAP-v2 for Windows 7 authentication which points to the Internal Users Identity Source

I have the Default rule at the end pointing to CN username for EAP-TLS authentication of the 7975 IP Phone
STEP 6: Setting up wired 802.1X authentication for Windows 7
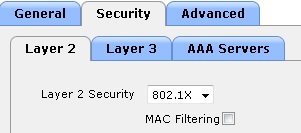
STEP 7: Enable 802.1X authentication on the Remote LAN and sit tight
Below you can see successful authentication for 7975 phone using x509_PKI and Windows 7 using PEAP (EAP-MSCHAPV2)

- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Vinay,
I cannot see the screenshots or pictures properly. Please check this & correct if any issues
Regards
Rasika
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Rasika,
Sent you a private note.
thanks,
Vinay Sharma
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
no pictures?
could you please correct this?
thanks!
BR
Konrad.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Vinay
There are no pictures.
Can you send me the document ?
Thanks
Soren Rothberg
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Vinay,
Pictures are not loading, would you please send me a copy of the document.
Thanks
Jon Sawyer
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello All,
I have attached PDF version with original Doc, hope this will help.
Thanks,
Vinay Sharma
Community Manager
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello friends,
I'm doing an 802.1X authentication implementation with a server radius using multi-host mode.
for server radius, I use windows server 2008 R2 Enterprise with installed roles like AD DS, AD CS, DNS Server, DHCP Server, Network Policy and Access Services (NPS). I use PEAP -MsChapV2 method.
for authentication when successfully will be redirected to vlan 10, and if failed will be directed to vlan 30.
for authenticator and supplicant switches, I use Cisco Catalyst 2960-CX series.
network topology:
3 clients --- g0/2, g0/3, g0/4 --- suplicant switch (switch2) --- g0/1 (supplicant switch) to g0/3 --- switch authenticator (switch1) - g0/1 - server radius.
script authenticator:
Switch1#sh run
Building configuration...
Current configuration : 3391 bytes
!
! Last configuration change at 06:17:02 UTC Fri Nov 3 2017
! NVRAM config last updated at 06:17:09 UTC Fri Nov 3 2017
!
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
aaa new-model
!
!
aaa authentication dot1x default group radius
aaa authorization network default group radius
aaa accounting network default start-stop group radius
!
!
!
!
!
!
aaa session-id common
system mtu routing 1500
!
!
!
!
!
!
!
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-3753304576
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3753304576
revocation-check none
rsakeypair TP-self-signed-3753304576
!
!
crypto pki certificate chain TP-self-signed-3753304576
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 33373533 33303435 3736301E 170D3137 31303235 30373031
31325A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D33 37353333
30343537 3630819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100C5DB 3CB9DFF2 77BDF4BA 5A9A2842 B71574A0 58FC948F EF638567 64FCCDC0
F842FB87 D1A7509F CF178E66 81578924 AA24C583 F6F82921 898DA3A5 826F81B5
4DB19C29 35ECE681 D8A60EFF 2587AA24 F87A606D B1645B14 8F8CCBA5 2441947C
2F646F38 AB657A8D 2E2A7EED F716FF61 147A875D 654C2180 3B6C5789 3618C7FE
BCF30203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 147771B2 F7F18FB4 1E7361EF E18B497D DEDDD572 CC301D06
03551D0E 04160414 7771B2F7 F18FB41E 7361EFE1 8B497DDE DDD572CC 300D0609
2A864886 F70D0101 05050003 81810085 2E8424AF 2FE7AEFC 74D07E7C BE1E141F
79F2E7EC 263877AE F6532F13 4D069CDA 80C7A219 8AEACB31 443CC054 9466502F
40317CF6 4D5F7409 D05590CE D74E29C4 F0A95E69 D4B26372 0086C7E9 14A37DBE
3DE0BBB7 355DF39B 5169479C 24BE990B 91E13BEE 99C46D24 1A00CFDC 0D5C60A0
2BEEA481 0C60152E 49A59BCC 0E7D62
quit
dot1x system-auth-control
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/1
switchport mode access
!
interface GigabitEthernet0/2
!
interface GigabitEthernet0/3
switchport mode access
authentication event fail action authorize vlan 30
authentication event no-response action authorize vlan 30
authentication host-mode multi-host
authentication port-control auto
dot1x pae authenticator
!
interface GigabitEthernet0/4
!
interface GigabitEthernet0/5
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface Vlan1
ip address 10.123.10.250 255.255.255.0
!
interface Vlan10
ip address 172.16.10.250 255.255.255.0
ip helper-address 10.123.10.10
!
interface Vlan30
ip address 172.16.30.250 255.255.255.0
ip helper-address 10.123.10.10
!
ip forward-protocol nd
ip http server
ip http secure-server
!
!
!
!
!
!
radius server host
address ipv4 10.123.10.10 auth-port 1812 acct-port 1813
key 12345
!
!
line con 0
line vty 5 15
!
end
============================================================================
script switch supplicant:
Switch2#sh run
Building configuration...
Current configuration : 973 bytes
!
! Last configuration change at 06:17:51 UTC Fri Nov 3 2017
!
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
system mtu routing 1500
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface GigabitEthernet0/3
!
interface GigabitEthernet0/4
!
interface GigabitEthernet0/5
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface Vlan1
no ip address
!
ip forward-protocol nd
ip http server
ip http secure-server
!
!
!
!
!
line con 0
line vty 5 15
!
end
Switch#
i found the problem, when my authenticator connect to switch supplicant then the authentication notification does not appear to client. direct authentication failed.
from my configuration above, is there anything wrong or need to be added?
I beg for his help, thank you very much.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

