- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Mobility control & data encryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 10:25 AM - edited 07-05-2021 11:16 AM
Hi everybody!
Found this paper:
It says that:
"In release 8.7 end-to-end Tunnel encrypted between Anchor and Foreign Controllers"
by issuing commands:
config mobility group member add
config mobility encryption enable
(i'm not mentioning adding mobility peers)
But in Configuration Guide it's more complicated:
config mobility group member add peer-mac-addr peer-ip-addr group-name encrypt { enable | disable}
config mobility group member data-dtls peer-mac-addr { enable | disable}
1) Which commands are true?
2) Will both control (port 16666) and data (port 16667) flows will be encrypted after enabling this feature?
3) When deploying Foreign-Anchor scenario with this encryption, is it enough to open ports 16666 & 16667 on the firewalls for mobility messaging and user traffic to be tunneled between foreign and anchor? Or is it required to open 5246/5247 for CAPWAP traffic for Anchor also? (not mentioning everything else, like https, snmp etc.)
Thanks in advance!
Artem
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 03:20 PM
In release 8.7 end-to-end Tunnel encrypted between Anchor and Foreign Controllers"
by issuing commands:
config mobility group member add
config mobility encryption enable
(i'm not mentioning adding mobility peers)
But in Configuration Guide it's more complicated:
config mobility group member add peer-mac-addr peer-ip-addr group-name encrypt { enable | disable}
config mobility group member data-dtls peer-mac-addr { enable | disable}
1) Which commands are true?
"config mobility group member add" is not the full command syntax. What you see in config guide is full syntax of that command. In other deployment guide, it just give the stating section of that command.
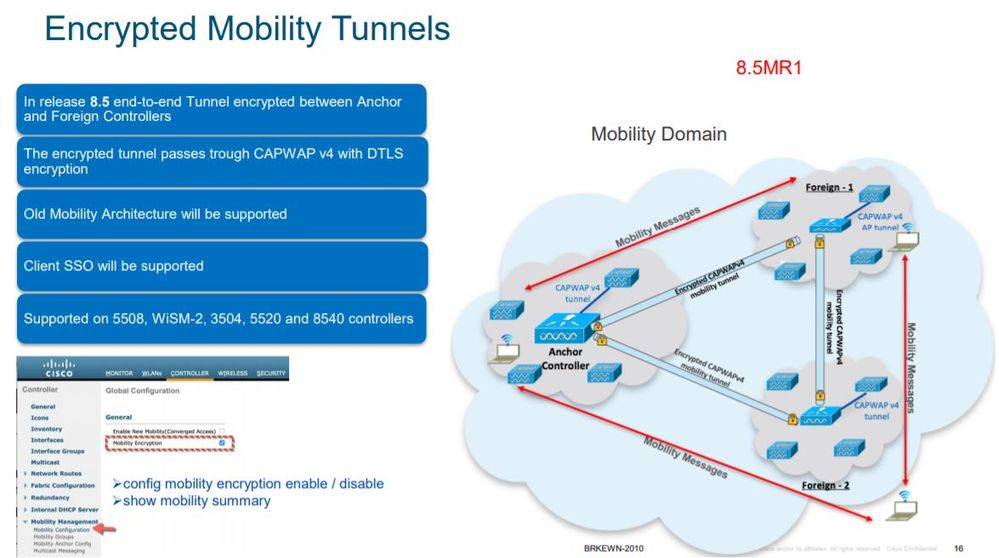
Mobility peer encryption introduced in 8.5MR1 release. So in that version you have to enable it globally (note that WLC will reboot once you enable it ) . See this Ciscolive presentation (below image from it - slide 16)
(WLC-1) >config mobility ?
dscp Configures the Mobility inter controller DSCP value.
encryption Configures tunnel(control/data) encryption in mobility flat architecture.
group Configures the Mobility group parameters.
multicast-mode Configures the Multicast Mode for mobility messages
new-architecture Configure the controller to switch between old and new mobility architecture.
statistics Resets the mobility statistics
(WLC-1) >config mobility encryption enable
Enabling encryption would change the data and control channel of mobility tunnel from unencrypted to encrypted !!!
Configuration changes will be saved and System will be rebooted. !!!
Are you sure you want to continue? (y/n)
y
Mobility tunnel encryption is enabled for flat architecture.
The system has unsaved changes.
Configuration saved!
System will now restart!
Later versions, you do not have option to enable it like that. You can enable it per mobility member. Here is a controller running on 8.10 configuration options.
(WLC-3) >config mobility ?
dscp Configures the Mobility inter controller DSCP value.
group Configures the Mobility group parameters.
multicast-mode Configures the Multicast Mode for mobility messages
statistics Resets the mobility statistics.
(WLC-3) >config mobility group member ?
add Add/Change a Mobility group member to the list.
data-dtls Optional data-dtls configuration for mobility peer. Default is enabled
delete Delete a Mobility group member from the list.
hash Configure hash key for authorization. Applicable only if member is a Virtual Controller in the same domain.
(WLC-3) >config mobility group member add 28:94:0f:ae:42:e0 10.5.x.x mildura encrypt ?
disable Disables secure communication to peer
enable Enables secure communication to peer
(WLC-3) >config mobility group member add 28:94:0f:ae:42:e0 10.5.x.x mildura encrypt enable
2. Yes, both control & data will be encrypted. You can disable "data-dtls" if you want
(WLC-3) >config mobility group member data-dtls 28:94:0f:ae:42:e0 ?
enable Optional data-dtls enable or disable for member
disable Optional data-dtls enable or disable for member
(WLC-3) >config mobility group member data-dtls 28:94:0f:ae:42:e0 enable
data-dtls already configured
3. Still mobility messages use UDP 16666 & 16667 in outer headers, however inner traffic (control & data) is encrypted.
HTH
Rasika
*** Pls rate all useful responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 11:09 AM
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 11:43 AM
Thanks, Scott!
It's customer's requirement. We need to either confirm or refuse that both flows encrypted when speaking with their security department. It will not affect the design though, just want to be sure when speaking with them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 02:04 PM
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 03:20 PM
In release 8.7 end-to-end Tunnel encrypted between Anchor and Foreign Controllers"
by issuing commands:
config mobility group member add
config mobility encryption enable
(i'm not mentioning adding mobility peers)
But in Configuration Guide it's more complicated:
config mobility group member add peer-mac-addr peer-ip-addr group-name encrypt { enable | disable}
config mobility group member data-dtls peer-mac-addr { enable | disable}
1) Which commands are true?
"config mobility group member add" is not the full command syntax. What you see in config guide is full syntax of that command. In other deployment guide, it just give the stating section of that command.
Mobility peer encryption introduced in 8.5MR1 release. So in that version you have to enable it globally (note that WLC will reboot once you enable it ) . See this Ciscolive presentation (below image from it - slide 16)
(WLC-1) >config mobility ?
dscp Configures the Mobility inter controller DSCP value.
encryption Configures tunnel(control/data) encryption in mobility flat architecture.
group Configures the Mobility group parameters.
multicast-mode Configures the Multicast Mode for mobility messages
new-architecture Configure the controller to switch between old and new mobility architecture.
statistics Resets the mobility statistics
(WLC-1) >config mobility encryption enable
Enabling encryption would change the data and control channel of mobility tunnel from unencrypted to encrypted !!!
Configuration changes will be saved and System will be rebooted. !!!
Are you sure you want to continue? (y/n)
y
Mobility tunnel encryption is enabled for flat architecture.
The system has unsaved changes.
Configuration saved!
System will now restart!
Later versions, you do not have option to enable it like that. You can enable it per mobility member. Here is a controller running on 8.10 configuration options.
(WLC-3) >config mobility ?
dscp Configures the Mobility inter controller DSCP value.
group Configures the Mobility group parameters.
multicast-mode Configures the Multicast Mode for mobility messages
statistics Resets the mobility statistics.
(WLC-3) >config mobility group member ?
add Add/Change a Mobility group member to the list.
data-dtls Optional data-dtls configuration for mobility peer. Default is enabled
delete Delete a Mobility group member from the list.
hash Configure hash key for authorization. Applicable only if member is a Virtual Controller in the same domain.
(WLC-3) >config mobility group member add 28:94:0f:ae:42:e0 10.5.x.x mildura encrypt ?
disable Disables secure communication to peer
enable Enables secure communication to peer
(WLC-3) >config mobility group member add 28:94:0f:ae:42:e0 10.5.x.x mildura encrypt enable
2. Yes, both control & data will be encrypted. You can disable "data-dtls" if you want
(WLC-3) >config mobility group member data-dtls 28:94:0f:ae:42:e0 ?
enable Optional data-dtls enable or disable for member
disable Optional data-dtls enable or disable for member
(WLC-3) >config mobility group member data-dtls 28:94:0f:ae:42:e0 enable
data-dtls already configured
3. Still mobility messages use UDP 16666 & 16667 in outer headers, however inner traffic (control & data) is encrypted.
HTH
Rasika
*** Pls rate all useful responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2019 12:03 AM
It's exactly what I needed to know.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide