- Cisco Community
- Comunidad de Cisco
- Wireless Mobility
- Wireless
- Re: Not Join AP to WLC 9800
- Suscribirse a un feed RSS
- Marcar tema como nuevo
- Marcar tema como leído
- Flotar este Tema para el usuario actual
- Favorito
- Suscribir
- Silenciar
- Página de impresión sencilla
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 10-25-2023 05:16 PM
I have a 5520 with 3800 APs, I am going to migrate to a 9800 (version 17.9.3), I will use the same APs.
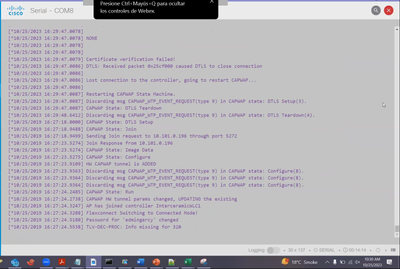
I configured my AP 3800 pointing to the WLC 9800, but the AP did not join.
It shows me a certificate error (I attach an error image).
This is the certificate information of the AP 3800
ap_Oficinas#
ap_Oficinas#show crypto
SHA1:
----------------------------- Device Certificate -----------------------------
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
2b:5f:d3:80:00:00:00:0b:7e:d1
Signature Algorithm: sha1WithRSAEncryption
Issuer: O=Cisco Systems, CN=Cisco Manufacturing CA
Validity
Not Before: Apr 19 02:52:22 2017 GMT
Not After : Apr 19 03:02:22 2027 GMT
Subject: C=US, ST=California, L=San Jose, O=Cisco Systems, CN=AP3G3-F80BCBFC8BBC/emailAddress=support@cisco.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Modulus (2048 bit):
00:eb:ac:57:81:7f:da:0a:d6:c9:15:ba:10:be:ff:
23:37:32:8a:ac:e4:a8:94:78:a2:35:9b:f6:6e:7f:
fc:6c:57:02:97:fd:7a:31:51:2a:d4:48:4e:16:dd:
4c:61:f2:24:1d:72:ab:7c:75:d2:f0:c9:77:3b:8a:
aa:ad:dc:61:dd:7e:10:28:aa:2c:34:24:b0:4b:02:
c3:08:e1:73:23:06:de:4a:ba:28:58:1f:1f:5a:44:
80:1a:66:34:58:85:57:9e:25:2e:93:b1:ff:8b:88:
16:3a:54:4e:e3:42:3c:80:c8:8c:e1:04:a1:00:6e:
9f:19:29:4e:90:86:4b:7c:20:d4:6f:e6:2a:fe:a8:
eb:84:7d:75:0a:73:d5:c4:f8:6d:84:ae:75:85:07:
d8:2f:8f:9a:65:5e:c0:66:8b:5c:54:c9:68:4b:f0:
06:e6:95:05:71:8e:4f:49:a0:25:cc:af:db:a7:ed:
1c:a6:c2:c2:d1:e7:a3:3b:c5:57:d5:ac:b6:25:da:
e3:fc:58:83:4f:83:3a:ec:7d:da:c0:f5:f4:4d:2c:
d9:d8:53:c6:b8:f4:2c:9c:4b:a7:40:40:4b:9f:98:
e2:e4:ec:a7:20:c2:a3:8e:2e:85:3d:2d:90:fa:59:
5b:8e:52:b5:cc:f4:ed:6f:e3:2e:dc:8d:23:5e:2c:
1c:91
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Subject Key Identifier:
61:3E:6A:B9:4C:87:2F:27:85:69:03:E2:A4:1F:1C:06:2A:E4:07:24
X509v3 Authority Key Identifier:
keyid:D0:C5:22:26:AB:4F:46:60:EC:AE:05:91:C7:DC:5A:D1:B0:47:F7:6C
X509v3 CRL Distribution Points:
URI:http://www.cisco.com/security/pki/crl/cmca.crl
Authority Information Access:
CA Issuers - URI:http://www.cisco.com/security/pki/certs/cmca.cer
1.3.6.1.4.1.311.20.2:
.0.I.P.S.E.C.I.n.t.e.r.m.e.d.i.a.t.e.O.f.f.l.i.n.e
Signature Algorithm: sha1WithRSAEncryption
82:05:c6:a4:a3:4e:d9:b1:d2:e1:5a:d8:6f:86:af:6e:3d:d2:
80:d7:7b:66:5f:2b:91:61:26:07:84:ba:bc:58:4c:ee:e6:21:
dc:db:e4:ad:e1:e9:6c:db:23:25:91:56:24:be:bf:9c:fd:95:
a6:ee:32:19:46:00:34:aa:e4:f7:22:99:b6:34:1f:eb:c8:7e:
c1:53:e3:c2:93:f3:13:d9:73:d7:be:a8:99:ca:e8:87:c9:5b:
9a:c2:27:c4:4a:b0:d7:d5:4e:04:9f:ea:a9:13:2d:5c:43:31:
e7:2d:43:78:3a:63:b9:49:5f:95:84:88:ae:a0:56:ff:b5:96:
4c:4b:ec:32:91:70:72:14:b9:53:cd:8e:67:c6:83:b1:9e:32:
b1:04:b7:08:e5:88:cd:24:39:b7:b1:5f:0e:34:08:37:02:00:
6c:2f:33:b6:f3:2a:ce:bc:f5:bf:05:23:f1:68:01:46:6d:c1:
d0:48:dd:8a:93:7a:72:99:57:66:b4:37:cc:83:4f:dc:12:e4:
84:22:f0:96:0b:30:a4:01:bc:fb:da:fd:cc:61:fd:13:36:4e:
38:2a:be:7e:97:6b:29:84:72:3e:c7:c1:d0:76:f8:df:10:4c:
19:a2:92:45:5b:f1:9d:7e:f8:75:f2:64:5e:79:d5:2b:4e:01:
a9:ab:4f:a6
------------------------------------------------------------------------------
SHA2:
----------------------------- Device Certificate -----------------------------
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
5e:f9:d4:ab:00:00:00:06:2b:8c
Signature Algorithm: sha256WithRSAEncryption
Issuer: O=Cisco, CN=Cisco Manufacturing CA SHA2
Validity
Not Before: Apr 19 02:53:10 2017 GMT
Not After : Apr 19 03:03:10 2027 GMT
Subject: C=US, ST=California, L=San Jose, O=Cisco Systems, CN=AP3G3-F80BCBFC8BBC/emailAddress=support@cisco.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Modulus (2048 bit):
00:cc:04:3d:51:78:c7:45:f0:50:fd:26:a9:10:fa:
e4:6c:1b:2e:81:fd:c4:0b:15:ac:72:13:6a:41:90:
d0:d4:90:b0:63:58:8b:79:0e:88:69:ab:a0:3f:98:
f1:88:7c:d1:a6:1c:d4:ca:86:ba:01:57:6c:10:ff:
c1:eb:4b:b9:20:f9:ae:4c:5e:81:ab:7d:9d:54:7d:
b7:29:4b:b4:41:36:d8:a8:a6:81:dd:41:52:f7:8d:
a8:f6:92:3f:81:a6:db:fe:30:22:7a:c1:f7:6a:87:
80:9a:4f:b8:f8:19:61:12:a3:0d:8b:b2:b3:de:f9:
44:cb:ea:3e:8b:6d:71:3e:40:18:e9:d4:c2:fb:9f:
2f:6e:1f:3e:28:3e:b4:73:e3:cd:33:7f:1e:63:fd:
66:bf:3b:24:0f:77:6f:d3:51:3c:64:a4:31:94:4b:
5c:83:c8:30:20:cc:e1:af:6a:71:ff:b2:4b:43:fa:
ed:5d:be:c1:98:cc:07:70:89:f5:f0:29:63:2b:69:
df:cd:52:d7:a3:00:94:52:38:1f:2c:f8:2e:64:dc:
25:79:c0:e4:cd:ff:c1:39:a5:70:34:92:dd:1a:48:
b8:eb:a0:dc:fa:2e:76:8a:18:3b:b3:4a:81:9f:5a:
d3:88:40:23:5b:f4:c0:de:09:bf:53:95:a2:ff:b0:
02:23
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Subject Key Identifier:
65:DC:D3:83:A1:7F:F7:6A:D5:D8:29:07:BD:94:72:CA:36:48:40:33
X509v3 Authority Key Identifier:
keyid:7A:D7:79:95:CA:BB:48:2B:B8:55:14:FD:A3:C0:0F:BC:A7:0F:96:19
X509v3 CRL Distribution Points:
URI:http://www.cisco.com/security/pki/crl/cmca2.crl
Authority Information Access:
CA Issuers - URI:http://www.cisco.com/security/pki/certs/cmca2.cer
1.3.6.1.4.1.311.20.2:
.0.I.P.S.E.C.I.n.t.e.r.m.e.d.i.a.t.e.O.f.f.l.i.n.e
Signature Algorithm: sha256WithRSAEncryption
d0:c7:d3:52:2f:41:12:6e:4f:43:2d:c9:c7:a6:bd:36:81:30:
ac:4f:c8:22:57:57:89:de:87:94:ae:2d:b8:49:4f:0f:45:77:
3e:a7:70:dc:a9:cf:34:a5:b6:6c:ca:57:2b:69:86:ff:f8:56:
f5:39:0a:79:90:80:00:c7:98:05:b1:f6:04:f0:bf:3f:f0:6b:
d8:59:1c:37:51:cc:9f:8d:5f:a6:5d:24:da:42:81:ab:41:f5:
40:24:ca:ea:29:bb:8b:62:59:aa:9b:ed:91:a4:53:38:e8:8b:
75:2e:3d:aa:d7:67:e6:2a:00:13:e0:e3:4f:8c:4a:62:a9:5e:
90:32:1d:f3:4a:a4:08:23:45:35:c5:c1:48:ea:65:b6:0e:30:
11:4a:46:1f:1b:4f:8b:8f:9d:30:55:e8:c7:b6:05:b0:1a:ac:
90:9a:21:e8:41:7b:9e:f4:97:83:f8:df:fc:d3:65:71:44:5a:
c7:3e:61:68:14:3e:1c:23:bf:55:38:e8:ed:fa:87:bb:6f:a4:
bd:94:03:97:03:5d:e9:b1:d0:ff:4d:4f:55:3c:1a:64:72:34:
c9:e5:bf:cd:f7:ec:7d:a7:16:76:fa:60:9b:c5:cd:30:1b:75:
00:dc:42:12:dc:d0:b2:77:c9:28:f0:63:51:ed:20:25:56:90:
16:79:9b:d0
------------------------------------------------------------------------------
Done
ap_Oficinas#
ap_Oficinas#
ap_Oficinas#
I can see that the certificates are still valid and the attached image does not show more details (for example invalid certificate or expired certificate).
So my plan of action is to upgrade my WLC 9800 to the recommended version or upgrade my AP to the most current version.
What could be happening.
¡Resuelto! Ir a solución.
- Etiquetas:
-
Wireless
Soluciones aceptadas
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 10-25-2023 07:40 PM
Hi again @nstr1
I see, I though you delete the previous WLC and was trying to join just to 9800.
Well you can do two things, the first one is upload manually the image on your AP that it will be use after joint to 9800 that image is 15.3(3)JPN2.
The second things its because I think you AP is hitting CSCvb93909 Field Notice: FN - 63942
configure terminal
crypto pki certificate map map1 1
issuer-name co cisco manufacturing ca
crypto pki certificate map map1 2
issuer-name co act2 sudi ca
crypto pki trustpool policy
match certificate map1 allow expired-certificate
exit
Create a Certificate Map and Add the Rules
configure terminal
crypto pki certificate map map1 1
issuer-name co Cisco Manufacturing CA
Use the Certificate Map Under the Trustpool Policy
configure terminal
crypto pki trustpool policy
match certificate map1 allow expired-certificate**Please rate the answer if this information was useful***
**Por favor si la información fue util marca esta respuesta como correcta**
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 10-25-2023 06:06 PM
Hi there.
Silly question, are you pretty sure the AP didn't join to the controller? because final lines It said It did it.
**Please rate the answer if this information was useful***
**Por favor si la información fue util marca esta respuesta como correcta**
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 10-25-2023 06:54 PM
Of course he joined but to WLC 5520.
I need to say that through the AP's CLI I point to the WLC 9800 for a moment, it does the discover and the 9800 responds then shows the certificate error and starts the disover once again and joins the 5520.
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 10-25-2023 07:40 PM
Hi again @nstr1
I see, I though you delete the previous WLC and was trying to join just to 9800.
Well you can do two things, the first one is upload manually the image on your AP that it will be use after joint to 9800 that image is 15.3(3)JPN2.
The second things its because I think you AP is hitting CSCvb93909 Field Notice: FN - 63942
configure terminal
crypto pki certificate map map1 1
issuer-name co cisco manufacturing ca
crypto pki certificate map map1 2
issuer-name co act2 sudi ca
crypto pki trustpool policy
match certificate map1 allow expired-certificate
exit
Create a Certificate Map and Add the Rules
configure terminal
crypto pki certificate map map1 1
issuer-name co Cisco Manufacturing CA
Use the Certificate Map Under the Trustpool Policy
configure terminal
crypto pki trustpool policy
match certificate map1 allow expired-certificate**Please rate the answer if this information was useful***
**Por favor si la información fue util marca esta respuesta como correcta**
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 10-26-2023 08:33 PM
I followed your recommendations and that helped me a lot. Now my Access points joined the wlc. thanks for the tip
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 10-26-2023 08:53 PM
Glad to hear
**Please rate the answer if this information was useful***
**Por favor si la información fue util marca esta respuesta como correcta**
Descubra y salve sus notas favoritas. Vuelva a encontrar las respuestas de los expertos, guías paso a paso, temas recientes y mucho más.
¿Es nuevo por aquí? Empiece con estos tips. Cómo usar la comunidad Guía para nuevos miembros
Navegue y encuentre contenido personalizado de la comunidad