- Cisco Community
- Technology and Support
- Networking
- Cisco Catalyst Center
- Re: Cisco DNA Discover - Netconf fail in Switch and WLC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco DNA Discover - Netconf fail in Switch and WLC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2023 06:14 AM
Hi,
Can anyone help me understand and list the requirements needed to successfully discover a device via Netconf?
I validate that the devices have the command:
netconf-yang
1 - I read something that the device can not have AAA, TACACS, Radius configuration, is it true?
2 - I read something that the device must only have below configs regarding AAA, is it true?
3 - I know that to provisioning the WLC 9800 in Cisco DNA I need to have NETCONF, but to provision a device do I need to have NETCONF?
Please can anyone clarify my question above and let me know the right procedure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2023 09:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2023 01:38 PM
Thank you.
I followed the instruction, but I still get an error message in Netconf.
I did a tcpdump capture in DNA and I noticed that the Switch is always sending a "Reset" to the connection.
Any advice?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2023 02:31 PM
which device model and version are you trying to disconvery?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2023 02:29 AM
Hi,
Thank you for your reply.
I have these devices, and all of them failed in NETCONF:
cisco C9800-80-K9
Cisco IOS-XE
ROM: 16.12(5r)
Sw version 17.03.07.
C9300-48P
ROM: IOS-XE ROMMON
SW version 16.9.3
C9500-16X
ROM: IOS-XE ROMMON
SW Version: 16.12.3a
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2023 03:12 AM
Disable netconf and enable again.
Test with ssh < ip address> 830
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2023 04:15 AM
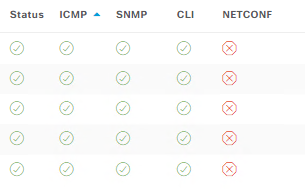
When I try to access a Switch with DNAC default settings:
I don´t know if the text in the image is visible. The output is:
Unable to negotiate with x.x.x.x port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
I already tried to add this algorithm to DNAC:
$ nano /etc/ssh/ssh_config
KexAlgorithms diffie-hellman-group-exchange-sha1
After adding this line in ssh_config file:
The error message is because I have FIPS enable, but I don't have FIPS enable. I have checked it
When I tried to do it for the WLC 9800 with DNAC default settings:
If you could give me any advice about it, I would be very grateful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2023 04:57 AM
What? Do you have FIPS enable on DNAC?
Man, if you do, you need to reimage the server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2023 05:05 AM
No, I don't have FIPS enabled.
This is why I don´t understand this message.
Look:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
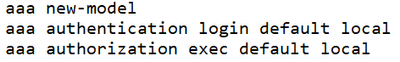
06-26-2023 05:16 AM
OK.
Try this. Enable SSH on the devices again.
crypto key generate rsa
user 2048 key lengh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2023 05:29 AM
-- Switch:
-- WLC:
SSH Enabled - version 1.99
Authentication methods:publickey,keyboard-interactive,password
Authentication Publickey Algorithms:x509v3-ssh-rsa,ssh-rsa,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,x509v3-ecdsa-sha2-nistp256,x509v3-ecdsa-sha2-nistp384,x509v3-ecdsa-sha2-nistp521,rsa-sha2-256,rsa-sha2-512
Hostkey Algorithms:x509v3-ssh-rsa,rsa-sha2-512,rsa-sha2-256,ssh-rsa
Encryption Algorithms:aes128-gcm,aes256-gcm,aes128-ctr,aes192-ctr,aes256-ctr
MAC Algorithms:hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
KEX Algorithms:ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group14-sha1
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 2048 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded): TP-self-signed-3942078477
ssh-rsa...................
Sorry, some of the images lost all quality, when I upload them
Same issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2023 01:50 PM
@Flavio Miranda is this NETCONF error related to it?
Cisco DNA Discover - Netconf fail in Switch and WLC - Cisco Community
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2023 01:53 AM
It could be. Are using tacacs?
As per your introduction I though you were aware of that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2023 04:04 AM
In the Switches I only have Radius, and WLC I have both, but only Radius is assigned to VTY lines.
My doubt is because when I try the same setup in my lab environment it works well.
The only difference is that in my lab environment, I am able to perform ssh < ip address> -p 830, and the production enviroment I am not able as I mentioned above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2023 04:13 AM
You should be able to ssh from DNAC to device on port 830.
what´s prevents it? Firewall?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide