- Cisco Community
- Technology and Support
- Services
- Cisco Cloud Service Router (CSR) for Public Cloud Discussions
- Re: ASA Radius Exec Authorization Not Working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA Radius Exec Authorization Not Working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2019 12:12 PM
Hello,
I have an ASA 5515 running 9.8(3)21. I'm using a Win2019 NPAS server for RADIUS. The setup is working fine for authentication for VPN, HTTPS, and SSH. My NPAS is configured on the ASA as:
aaa-server SB_MGMT_NPAS protocol radius
aaa-server SB_MGMT_NPAS (inside) host x.x.x.x
key 8 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
no mschapv2-capable
These are the AAA commands that make that work:
aaa authentication enable console SB_MGMT_NPAS LOCAL
aaa authentication http console SB_MGMT_NPAS LOCAL
aaa authentication ssh console SB_MGMT_NPAS LOCAL
aaa authorization command LOCAL
aaa authentication login-history
The problem I'm having is that I can't find a "aaa authorization" command syntax that will allow me to control the privilege level of SSH users. I have two levels of users setup in NPAS RADIUS based on group membership. Admin users are set for level 15 and auditors for level 3. Using debug on the ASA I can clearly see that RADIUS is communicating the privilege attribute during the authentication process:
Got AV-Pair with value shell:priv-lvl=15
Got AV-Pair with value shell:priv-lvl=3
However, when I apply "aaa authorization exec authentication-server auto-enable" or I enable authorization for exec shell access in ASDM it will not allow be to enable at all. What is the command syntax to make the ASA pay attention to the privilege level attribute? Thank you.
- Labels:
-
CSR for Public Cloud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2020 01:49 PM
I am having the same issue... did you find a resolution? If I disable the auto-enable, I can enable fine, but if I auto-enable, I get the "You do NOT have Admin Rights to the console" message.
Thanks,
Glenn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2020 08:37 PM
Hey guys I found a solution to this problem, I was having the exact same issue myself.
I came across this blog post here
https://blog.junico.uk/2020/02/27/assigning-privilege-levels-on-cisco-asa-with-radius/
Basically how this works with out getting too lost in the weeds (see the link above for additional details) the process to get privilege lvl 15 on an ASA is as follows:
Assuming you've have already correctly configured your radius server on you ASA this will only focus on the windows side of things and specifically in my environment where I got this working is on a windows 2016 server.
Open NPS on your windows 2016 server. Expand the Policies section and right click network policies and click new. Give your policy a suitable name and click next. Assign the user group to this policy (in my case network admins) and click next again. Select access granted and click next again. Check the box for Unencrypted authentication (PAP, SPAP), click next and click no on viewing the help topic. Click next again on the client constraints. Everything up until now should be familiar stuff in regards to NPS being used for Cisco authentication. Now you should be at the configure settings portion of the wizard, and this is where things drastically differ from you standard configuration as opposed to a router or switch authenticating.
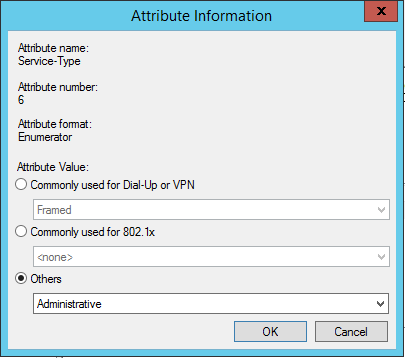
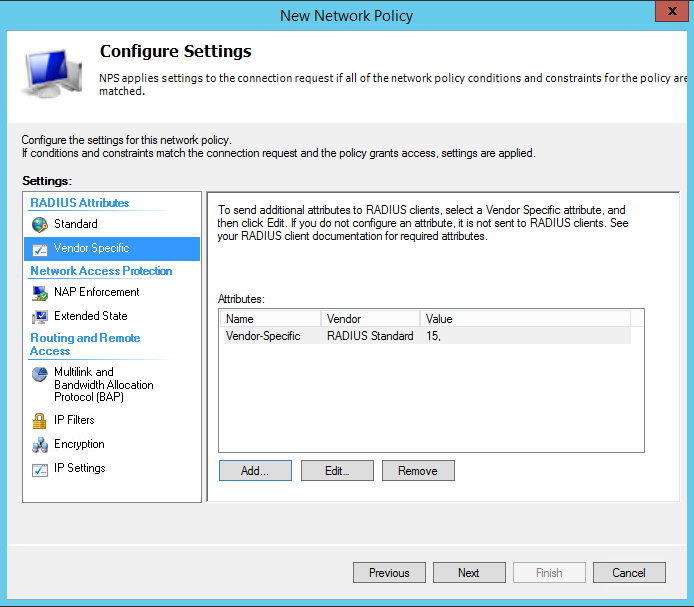
First remove the framed protocol, then edit the service type so that the value is administrative.
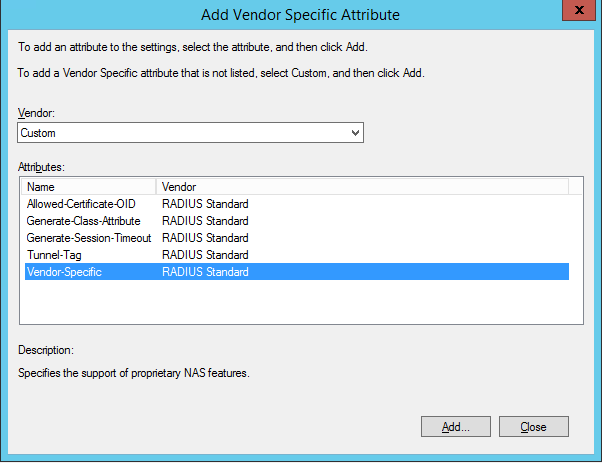
Move to vendor specific, click add, and instead of selecting Cisco, choose custom and select vendor specific the click add (see screen shot below)
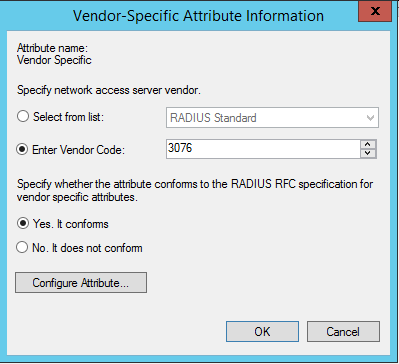
In the vendor-specific attribute window that opens click the radial button for "enter vendor code" and put the value of 3076. Below that select the radial button of "yes it conforms" and then click configure attribute.
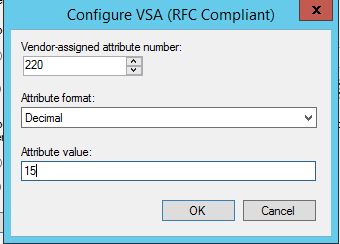
In the Configure VSA (RFC Compliant) window that open enter a value of 220 in the vendor-assigned attribute number. For the attribute format select decimal, and finally, in the attribute value enter the privilege level you desire (in my case lvl 15)
Click Ok, Ok, Ok, and close. Now you should be back at the configure setting portion of the wizard.
Just click next and Finish.
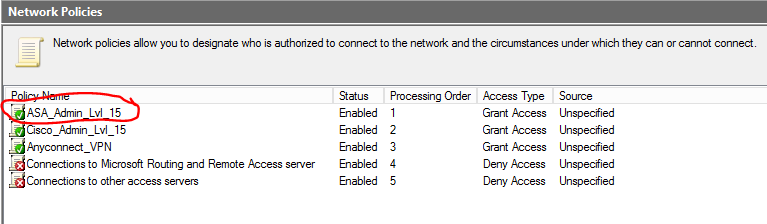
LAST thing to note is you want to move this new policy to the top of you network policies otherwise it doesn't seem to function with the ASA if you have other policies above it.
Hopefully this post helps someone and they don't have to go as deep down the rabbit hole as I did to find this information to get ASA authentication with proper authorization working.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide