- Cisco Community
- Technology and Support
- Security
- Cloud Security
- Re: Block Whatsapp Upload Failed only on Web but it's work on Apps
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2023 09:08 PM
Hi All,
I'm trying to test Web Policy on Cisco Umbrella to block upload on Whatsapp, Wetransfer, and Dropbox. It turns out we can block upload only wetransfer and dropbox, there's something strange on Whatsapp.
If i test using Whatsapp apps on Windows it can block all upload files, but when i try using Whatsapp Web it doesn't block at all.
i don't understand why it happen. Can you guys help about this?
Solved! Go to Solution.
- Labels:
-
Umbrella
-
Web Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2023 05:18 AM
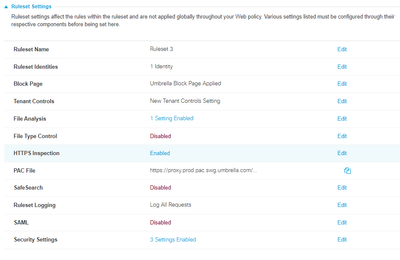
Looks like your configuration is correct and the policy is matching.
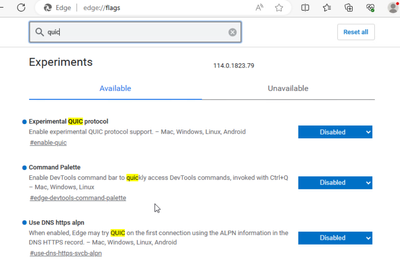
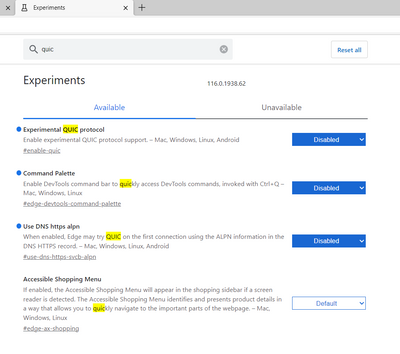
Do you have QUIC enabled? I would like to test the upload with QUIC disabled. To disable QUIC, browse "chrome://flags" and search "quic" and disable it from all:
Before testing, clear the cache and close all the tabs.
For the test, we need to use a different file, to make sure whatsapp doesn't have it in its cache already.
If after this, still doesn't work, please insist on the support case because engineering will have to push new updates from the backend.
As a workaround, you could try to block the following domains and test if this blocks the uploads:
cdn.whatsapp.net
mmg.whatsapp.net
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2023 04:47 AM
Hi,
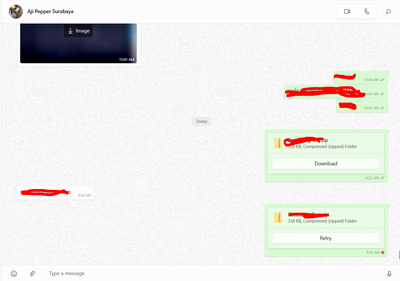
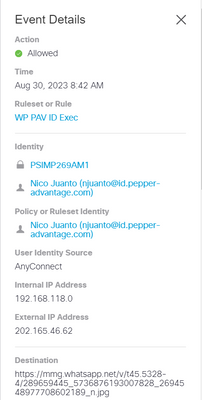
I understand that you are trying to block uploads on WhatsApp web, but it's been allowed instead.
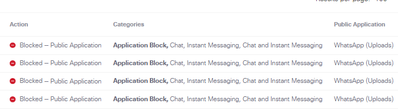
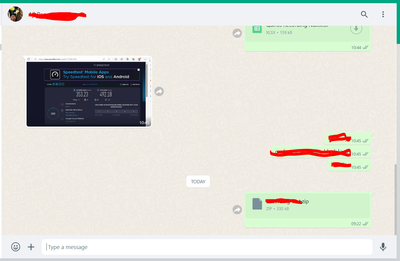
From your screenshots, I can see that is showing Allowed on the Activity Search report but on Whatsapp I can see the red icon, "Retry" and the time is different as well (10:44 vs 11:03AM). My question is, is that file being uploaded using Whatsapp web successfully?
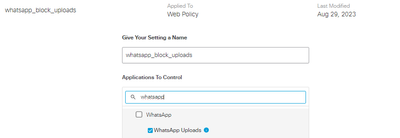
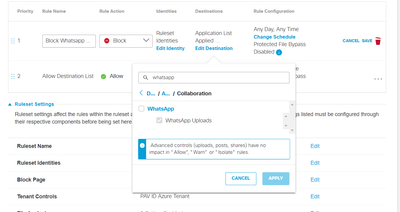
I have configured the following to block the uploads on WhatsApp and it works for me:
1. Policies/Policy Components/Application Settings/Add:
2. Policies/Web Policy/Add:
3.
4. Access to whatsapp web:
5. Upload a document to a conversation:
6. Check the Activity Search:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2023 07:29 PM
Hi @aaragonb ,
Thank you for your reply and yes i'm trying to block upload whatsapp on Apps and Web.
is that file being uploaded using Whatsapp web successfully?
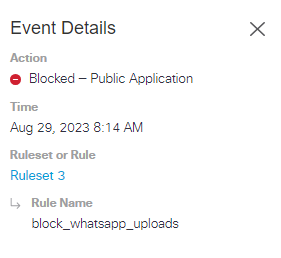
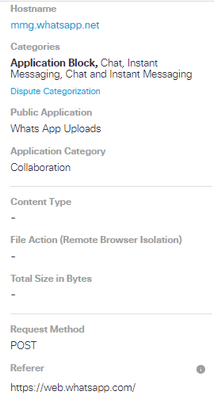
Yes it doen't block on Whataspp Web but it blocks on Whatsapp Apps.
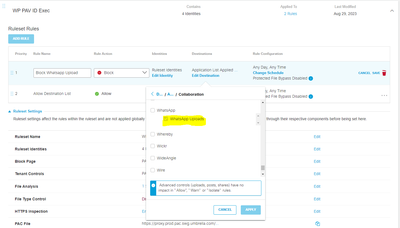
Belows are my setup on the web policy.
1. Block Upload on Rule
2. Make sure that my name on ruleset identities (njuanto@id.pepper-advantage.com)
3. Able to access Whatsapp Web and Whatsapp Apps
4. Test Upload on Web.
5. Test upload on Apps
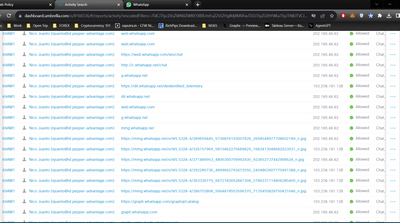
6. Activity Log Search
idk why on apps it is blocking but it doesn't show on log, instead of web.
i have raise a ticket as well to umbrella support but hasn't response. need to solve this ASAP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2023 05:18 AM
Looks like your configuration is correct and the policy is matching.
Do you have QUIC enabled? I would like to test the upload with QUIC disabled. To disable QUIC, browse "chrome://flags" and search "quic" and disable it from all:
Before testing, clear the cache and close all the tabs.
For the test, we need to use a different file, to make sure whatsapp doesn't have it in its cache already.
If after this, still doesn't work, please insist on the support case because engineering will have to push new updates from the backend.
As a workaround, you could try to block the following domains and test if this blocks the uploads:
cdn.whatsapp.net
mmg.whatsapp.net
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2023 01:51 AM
Hi @aaragonb ,
I just tested the QUIC disabled on Edge since i never using Edge and it's work all whatsapp upload can be blocked. Why do i need to disabled the QUIC, because it neither enabled nor disabled, it only show default.
since i have 150 endpoint, i cannot disabled the QUIC on Edge and Chrome manually. Do you have any idea to do it automatically from Cisco Umbrella? or Does this app control has some bug?
We also tested using one of our networks as ruleset identites and it's work without QUIC disable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2023 10:07 AM
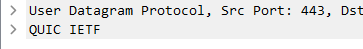
In a nutshell, QUIC operates over UDP, which is not intercepted by the Roaming Client, it won't be proxied by Umbrella, so Umbrella won't be able to enforce the policies to that traffic.
As a workaround, you could block QUIC on your firewall.
Please, keep in mind, that in devices with the AnyConnect/Secure Client with browsers with QUIC enabled/default, it might happen the traffic won't be intercepted by the roaming module, because this one proxies TCP 443/80 only.
You can read more about it here:
https://docs.umbrella.com/deployment-umbrella/docs/prerequisites-1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2023 06:57 PM
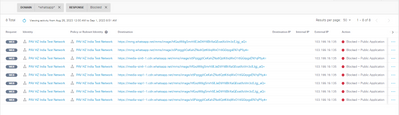
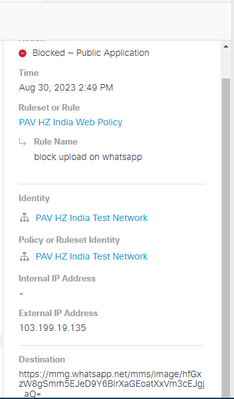
1 questions, if you said it won't be proxied by umbrella but why did it still blocked when using network as ruleset identities?
i didn't block QUIC on my firewall yet and i tested using browser with QUIC default on Chrome. please see the screenshow below as reference.
is that just a coincidence?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2023 01:40 AM - edited 09-01-2023 05:03 AM
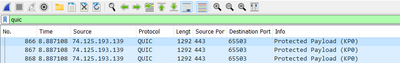
I would like to see a packet capture of that traffic to see if it was using QUIC to investigate further.
In general, we recommend blocking/disabling QUIC because it causes issues due to the nature of that protocol.
The traffic that is successfully handled by Umbrella and proxies in general is TCP 80/443.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2023 11:50 PM
ok cool @aaragonb , Does umbrella can see packet capture detail of the traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2023 09:46 AM
In the Umbrella dashboard, you can see the logged events in Reporting/Core Reports/Activity Search. You can export those to see more details about the events: https://docs.umbrella.com/umbrella-user-guide/docs/log-format-and-versioning
For instance, to see if the web traffic is using QUIC, we need to use Wireshark, because this traffic won't be logged by Umbrella.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide