- Cisco Community
- Technology and Support
- Security
- Cloud Security
- I'm using WCCP and had to
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Windows Update not working with Ironport Web Appliance \ WSA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2015 06:53 AM - edited 03-08-2019 05:38 PM
Our engineers have issues trying to download Windows Server updates unless allowed out directly through the firewall. We use 2 S370 Ironport appliances and the logs don't show anything being blocked. When using the Ironport proxy the updates won't download. Has anyone seen this issue before? Thanks !
Cisco Ironport WSA S370
Cisco Ironport M670 management appliance
Windows Server 2003 & 2008
IE 11 browser
- Labels:
-
Web Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-25-2015 09:51 AM
Hello Paul,
There is an issue where Windows Updates fail when authentication is enabled, attempt to create identity that contains windows updates domains and exempt them from authentication. This guide may be helpful as it contains windows client updates, not sure if the share the same update domains with Windows Servers.
See the following for more information- http://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117994-qna-wsa-00.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2016 11:07 AM
I'm using WCCP and had to exclude the servers in my ASA ACL from going through the WSAs. If there's another way I don't know what it is but I really wasn't concerned about the servers getting filtered anyways because no one gets on them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2016 03:35 AM
Dear Paul,
Please create custom category for below URLs and authenticate bypass..
You can create this by creating a separate identity and separate access policy.
download.windowsupdate.com
.windowsupdate.microsoft.com
.update.microsoft.com
.download.windowsupdate.com
update.microsoft.com
.windowsupdate.com
download.microsoft.com
windowsupdate.microsoft.com
ntservicepack.microsoft.com
wustat.windows.com
c.microsoft.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2016 11:07 PM
Hello Paul,
Windows update is also using range request download method and this function is disabled globally by default in WSA due to security reason.
If you need the appliance to honour the rangerequest download method for just windows update, would recommend create a custom URL category for windows update from the other response information and also bypass authentication from WSA and you will need to set that custom URL category for windows update to "ALLOW" action in the policy instead of using "Monitor".
Hope this helps.
Regards
Handy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2016 02:06 AM
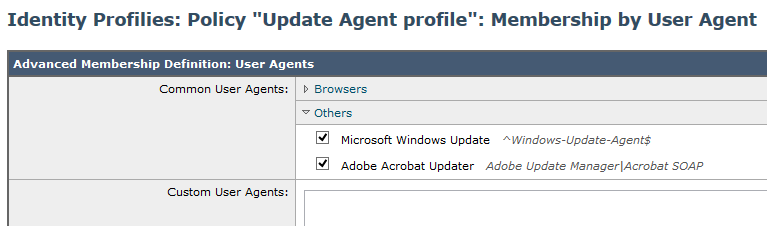
Windows and Acrobat updates can be specified in an Identity Profile so you don't need to create an URL category for that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2016 08:06 AM
If already using an Identity with a URL category for Windows update URL's, Would adding the "Common User Agent" - "Microsoft Windows Update" restrict all URL categories added to the Identity?
Looking at the Advanced section you can define by:
"Proxy Ports"
"URL Categories"
"User Agents"
I believe they are independent of each other but I was a little wary that if you are currently defining this by URL Category and then further add some "User Agent" strings/variables etc.... It may be required to match everything defined.
Can someone confirm that these 3 subsets in the "Advanced" section function independently?
I would hate to add the user agent for MS Updates if this then caused "Other" URL categories added to that specific Identity to stop working because they don't use the "Windows-Update-Agent" string....
I can see an advantage to selecting this option though as when our Server Admins started to setup Windows Server 2012 awhile back that the activation or update site for 2012 was slightly different than before and I had to add that URL to allow it out... but it would seem likely to be the same user-agent-string that Microsoft uses for updates... haven't verified this but it would make sense...
Anyone have more thoughts on this?...
Thanks,
KJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 07:24 AM
Windows 2012 Server’s Windows update agent uses "Microsoft BITS/7.7" as the user agent string:

Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide