- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Knowledge Base
- Chalk Talk: An Insight to Cisco VPN Phone
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-02-2013 12:31 PM - edited 03-12-2019 10:06 AM
In today’s world, organizations are striving to stay connected with their employees. With businesses going 24X7, no organization can afford to have employees disconnected from the enterprise network and not able to access corporate voice or data resources. Understanding that modern day organizations need secure connectivity for their remote employees as well as telecommuters, Cisco has come out with the concept of VPN client on physical Cisco Unified IP Phone. Yes, you read it right, it’s an SSL client installed on a Cisco IP Phone that enables remote workforce and on-the-go employees to get access to corporate UC resources.
Cisco VPN Phone Overview
This new feature is called Cisco VPN Phone, and it leverages Cisco AnyConnect SSL client built into an IP phone’s firmware to connect to enterprise edge firewall (Cisco ASA). Cisco VPN Phone feature has numerous benefits,such as:
- No additional hardware is required by the end-user except for the IP Phone itself.
- Cisco Unified IP Phone with Cisco VPN client can get online from wherever Internet access is available.
- Cisco VPN Phone feature is supported with both Cisco ASA and Cisco IOS routers.
- Cisco VPN Phone can secure voice and video media along with IP Phone service traffic. This gives additional flexibility to go from a voice-only call to a video call. VPN tunnel applies only to voice, video, and IP phone services. The PC connected to PC port is responsible for authenticating and establishing its own tunnel with VPN client software (Split Tunneling)
- All settings are configured via CUCM administration, thereby providing ease of administration.
Figure 1 gives an overview of Cisco VPN Phone solution:
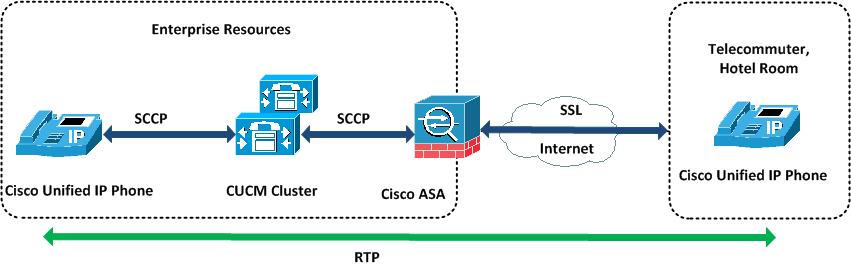
Figure 1: Cisco VPN Phone Overview
The Cisco Unified IP Phone creates an AnyConnect-based SSL tunnel to Cisco ASA, where all voice pertinent data is sent into the tunnel, whereas all regular data (non-voice traffic) is sent directly to the internet (split-tunnel) for the PC connected behind the IP Phone. When the SSL-tunneled data reaches Cisco ASA, matching the tunnel group, it decrypts the traffic and sends unencrypted traffic to CUCM (signaling as SCCP) and to the IP Phone within enterprise (media as RTP).
Cisco VPN Phone Configuration Prerequisites
There are certain pre-requisites that must be met before Cisco VPN Phone can be configured on a Cisco ASA and subsequently on a CUCM cluster. Cisco VPN Phone client is supported on 7942G, 7945G, 7962G, 7965G, 7975G, and 99xx and 89xx series IP phones.
For a list of phones supported with your CUCM version, you can check Feature: Virtual Private Network Client from CUCM Administration GUI > Cisco Unified Reporting > System Reports > Unified CM Phone Feature List > Generate a new report option.
The minimum requirements for support Cisco VPN Phone are as following:
- CUCM version 8.0.1 or above are supported.
- IP Phone SCCP firmware version 9.0(2) SR1S or later
- Cisco ASA IOS 8.0.4 or later
- Anyconnect VPN Pkg 2.4.1012 or later
- Two licenses, i.e. a premium AnyConnect license and AnyConnect for Cisco VPN Phone license is required for Cisco ASA. The part number for AnyConnect for Cisco VPN Phone is L-ASA-AC-PH-55XX (55XX is firewall model number such as 5505, 5510, 5580 and so on).
Detailed Steps to Configure Cisco VPN Phone
Step 1. Ensure that ASA Security Appliance Software version is 8.0(2) or greater
UCASA# show version
Cisco Adaptive Security Appliance Software Version 8.2(2)99 Device Manager Version 6.3(1)
Step 2. Confirm ASA is licensed for Cisco AnyConnect VPN Phone and AnyConnect Software 2.0 or greater is installed in flash.
UCASA#show disk0:
<output ommited>
140 2154944 Mar 18 2013 03:38:06 anyconnect- win-3.1.00495-k9.pkg
Step 3. Generate self signed certificate on cisco ASA.
UCASA (config)# crypto key generate rsa label vpnphone
UCASA (config)# crypto ca trustpoint asatrust
UCASA (config)# encrollment self
UCASA (config)# fqdn sslphone.cisco.com
UCASA (config)# subject-name CN=sslphone.cisco.com
UCASA (config)# keypair vpnphone
UCASA (config)# crypto ca enroll asatrust noconfirm
UCASA (config)# ssl trust-point asatrust outside
Step 4. Enable AnyConnect access on the interface that will terminate SSL VPN Connections.
UCASA (config)# webvpn
UCASA(config-webvpn)# enable outside
UCASA(config-webvpn)# svc enable
Step 5. Create a VPN Pool for assigning the VPN Phones unique IP addresses.
UCASA(config)# ip local pool SSLPool 192.168.250.1 - 192.168.250.254 mask 255.255.255.0
Step 6. Create a Group Policy, which specifies the configuration parameters that will be applied to the clients when they connect to Cisco ASA.
UCASA(config)# group-policy SSLVPNPhone internal
UCASA(config)# group-policy SSLVPNPhone attributes
UCASA(config-group-policy)# dns-server value 10.60.70.80
UCASA(config-group-policy)# vpn-tunnel-protocol svc
UCASA(config-group-policy)# default-domain value cisco.com
UCASA(config-group-policy)# address-pools value SSLPool
Step 7. Create a Connection Profile and Tunnel Group for the AnyConnect Client Connections, and assign an alias.
UCASA(config)# tunnel-group SSLPhone type remote-access
UCASA(config)# tunnel-group SSLPhone general-attributes
UCASA(config-tunnel-general)# default-group-policy SSLVPNPhone
UCASA(config-tunnel-general)# tunnel-group SSLPhone webvpn-attributes
UCASA(config-tunnel-webvpn)# group-alias SSLPhoneClient enable
UCASA(config-tunnel-webvpn)# group-url https://10.81.80.200/VPNPhone enable
Step 8. Enable alias/tunnel group selection for SSL VPN Connections.
UCASA(config-tunnel-webvpn)# webvpn
UCASA(config-webvpn)# tunnel-group-list enable
Step 9. Add user(s) to ASA local DB or use the TACACS+/RADIUS backend (if available).
UCASA(config)# username vpnclient password C1sc0123
UCASA(config)# username vpnclient attributes
UCASA(config-username)# service-type remote-access
Step 10. Export the ASA crypto certificate and save it as a .pem file on your laptop/PC.
UCASA(config)# crypto ca export vpnphone identity-certificate
The PEM encoded identity certificate follows:
-----BEGIN CERTIFICATE----- MIIB8zCCAVygAwIBAgIEAoMjTTANBgkqhkiG9w0BAQUFADA+MRowGAYDVQQDExFl
<output omitted>
-----END CERTIFICATE-----
Step 11. Upload the ASA Certificate on CUCM.
- Go to Cisco Unified OS Administration > Security/Certificate Management
- Select "Upload Certificate"
- Upload the ASA certificate to "Phone-VPN-Trust"
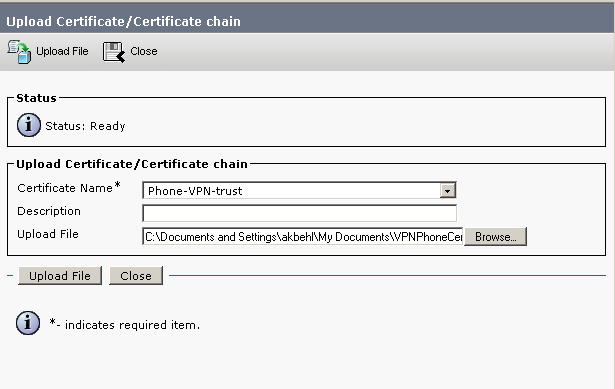
Figure 2: Cisco ASA to CUCM Certificate Upload
Step 12. Go to CUCM Administration > Advanced Features > VPN > VPN Gateway. Select the certificate that was uploaded earlier from ASA to CUCM, and ensure it’s listed under VPN gateway certificates.

Figure 3: CUCM VPN Gateway Configuration
Step 13. Go to CUCM Administration > Advanced Features > VPN > VPN Group. Under VPN Gateway Information, add the VPN Gateway created earlier.
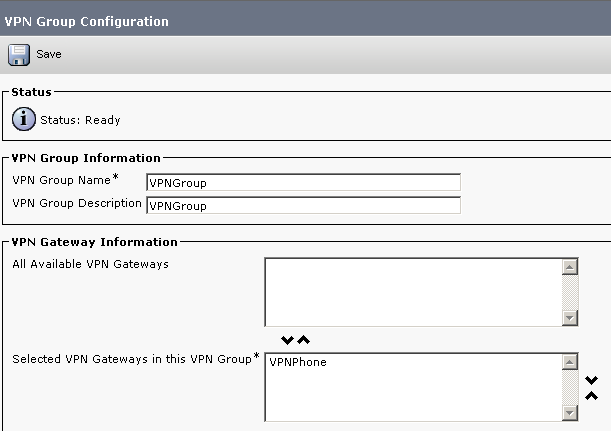
Figure 4: CUCM VPN Group Configuration
Step 14. Go to CUCM Administration > Advanced Features > VPN > VPN Profile. Ensure that the client authentication method is set to ‘user and password’ (similar to what was configured in Cisco ASA).
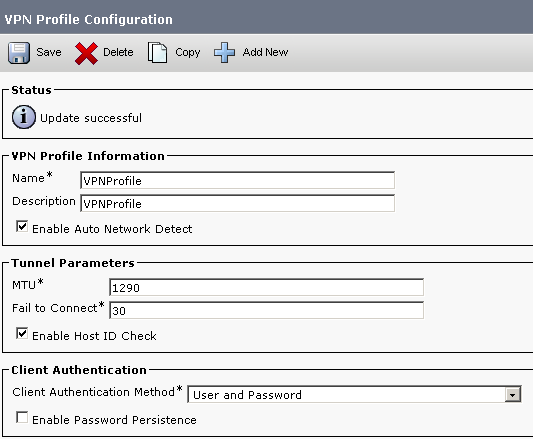
Figure 5: CUCM VPN Profile Configuration
Step 15. Go to CUCM Administration > Device > Device Settings > Common Phone Profile. Assign ‘Common Phone Profile’ to VPN phone.
Cisco VPN Phone configuration is now complete. After connecting the phone from within the enterprise environment, the IP Phone can be handed over to the user. The end user has multiple options to connect to VPN on Cisco Unified IP Phone:
- The user can select between VPN client (mode) enabled or disabled in the phone menu.
- With disabled mode on the VPN client; the phone makes no attempt to create a VPN connection and proceeds with the standard startup sequence.
- With enabled mode on the VPN client (and auto-network detection) the phone tries to detect the type of network and attempts to initiate a VPN connection only if the phone is outside of the enterprise network i.e. on a public network.
- With enabled mode on the VPN client and auto-network detection disabled the phone attempts to initiate a VPN connection. This allows the VPN connection to be established within the secure enterprise network.
The following figure gives an overview of user end configuration to initiate a VPN connection from IP Phone:
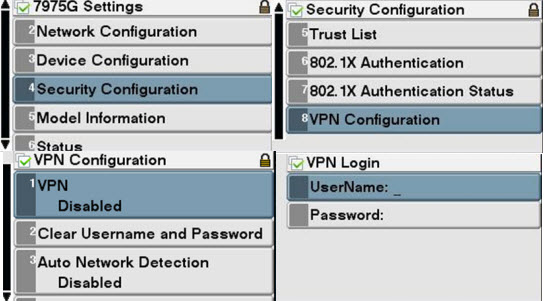
Figure 6: End USer VPN Phone -- VPN Connection Initiation
Summary
Cisco VPN Phone is a promising feature that is easy to deploy and maintain. It gives end users the flexibility to connect to the enterprise network and leverage voice resources from anywhere; wherever there is Internet connectivity. Moreover, it’s a solution that replaces older Phone Proxy and the need to have a VPN client side hardware, thereby reducing complexity of deploying a remote worker solution and helping lower costs.
Author's Biography

Akhil Behl is a Solutions Architect with Cisco Services, focusing on Cisco Collaboration and Security Architectures. He leads collaboration and security projects and service delivery worldwide for Cisco Services and the Collaborative Professional Services (CPS) portfolio. He's played major role in service conception and creation for various services within Cisco Advanced Services. He has Pre-Sales to Sales to Professional Services to Delivery to Post Sales experience with expertise in Consulting, Advisory, and Guidance services. He has extensive experience in Borderless, Collaboration and Data Center portfolio. Prior to his current role, he spent ten years working in various roles at Linksys as a Technical Support Lead, as an Escalation Engineer at Cisco Technical Assistance Center (TAC), and as a Network Consulting Engineer in Cisco Advanced Services.
Akhil has a bachelor of technology degree in electronics and telecommunications from IP University and a master’s degree in business administration from Symbiosis Institute. He is dual Cisco Certified Internetwork Expert CCIE # 19564 in Voice and Security. He also holds many other industry certifications, such as PMP, ITIL, VCP, ISM, CCNA, CCSP, CCVP, ISO/IEC 27002, TOGAF and CEH.
Over the course of his career, he has presented and contributed at various industry forums such as Enterprise Connect, Cloud Connect, Cloud Summit, Interop, Cisco Networkers, and SecCon. He has several research papers published in various national and international journals including IEEE.
He is an avid blogger and maintains a blog on Unified Communications Security - http://ucsecurity.wordpress.com
| Securing Cisco IP Telephony Networks Series: Networking Technology: IP CommunicationsPublished: Aug 31, 2012 Copyright 2012
Published by Cisco Press |
This article is featured in the December 2013 issue of the Cisco TS Newsletter. Are you subscribed?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can the phone firmware be updated over the VPN connection or does the phone need to be brought into the corporate network for firmware updates. Specifically 7942/62 devices. (updated) Assume that an Alternate TFTP is correctly set on the phone.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes, phone firmware upgrades can be performed on phones that are connected via VPN.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I don't think so. It is pretty tough to push even changes as you need to have alternative TFTP configured.
The VPN session is establishing after the phone boots up while the firmware upgrade is happening before that - this is specifically valid for 79xx phones. The new ones are keeping 2 images and they are downloading them while they are up so probably you can upgrade 8841 for example over SSL VPN.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


