- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Knowledge Base
- Chalk Talk: How to Manage Your Cisco Collaboration Environment Securely
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-05-2013 10:06 AM - edited 03-12-2019 10:05 AM
Now that your Cisco world class Collaboration Network is set up and functional, it is time to leverage the benefits of the Unified IP environment. With reduction in Total Cost of Ownership (TCO), leveraging converged network for transporting both voice and data and increased Return on Investment (ROI), what can possibly go wrong? Well, if you didn’t think in a holistic way while setting up the management aspect of your Collaboration network, a lot can go wrong. With things on the move, you should concentrate on making sure they keep going as planned. That is, ensure that you have a plan to securely manage the vital assets of your organization’s communications channels.
More often than not, the topic of “secure management” does not come up as early as it should in most network management discussions. Reasons can vary, such as – lack of support from higher management (monetary or manpower) or lack of insight or experience about what goes into secure management of a Collaboration network. With that said, a Secure Collaboration Network can be achievable only if network management is secured. All in all, if a true collaboration experience is to be achieved, it can be only by way of well-rounded security strategy, and secure network management is an indispensable part of any security strategy.
A Collaboration network’s secure management can be looked upon as a task to move away from unsecure management protocols to standards-driven secure management protocols. The following sections discuss the importance of switching from relatively unsecure or weak security posture management protocols to comparatively secure management protocols.
Something’s Just Not Right!
Until now many organizations still stick with clear text, and in turn, vulnerable protocols for managing their Collaboration networks. The burning question is – why use an insecure protocol at all? The answer is pretty straight forward –a default clear text protocol doesn’t require any special software at Network Management Station (NMS) nor any special configuration at the device being managed. While this may sound great at first, it’s not a leading practice or a recommendation for managing an organization’s Collaboration network.
Did Someone Say Telnet?
A few protocols deserve special mention here, which are still used whence their usage should be a thing of past. Telnet is one of those protocols that is used very frequently despite the fact that it is as good as leaving a device open to access with any authentication. Being clear text, telnet sessions can be sniffed and username and password can be used to gain access to the device being managed. In essence, it’s serving the access control to network devices on a silver platter to attackers/hackers.
Who’s Using FTP?
Similar to telnet, is File Transfer Protocol (FTP). Primarily used for transferring files e.g. IOS firmware, it’s a popular choice of management protocol for Cisco IOS routers and switches. While FTP can be secured by enforcing use of username and password (not leaving system exposed for anonymous access), the default unencrypted mode of FTP leaves it vulnerable to sniffing and Man-In-The-Middle (MITM) attacks. An insider or an external attacker can exploit and compromise the equipment being managed, by manipulating files as desired or by injecting code into files being transferred. More so, the attacker can still sniff the FTP stream for username and password (as it is unencrypted) and can start a new FTP session to the managed device.
To SNMP or Not to SNMP?
Simple Network management Protocol (SNMP) is one of the most popular and widely used network monitoring and notification protocol. SNMP can be deployed in various versions ranging from v1 to v2c to v3. If SNMP version is below version 2c, it is not the safest of options SNMP v1 has no data authentication or encryption capability, which leaves it wide open to attacks e.g. MITM attack. Both the device being managed and the NMS station can be compromised by a determined hacker/attacker. While SNMP v2c is not entirely secure; in that it doesn’t provide encryption abilities, it does offer authentication mechanism to keep nosy audiences out.
Now We are Getting Somewhere!
This section focuses on secure management protocols and their configuration for Cisco Collaboration network.
Why Didn’t I Use SSH to Begin With?
So, if Telnet is a high priority risk what are the alternatives? How about Secure Shell (SSH)? As a trustworthy protocol, SSH helps thwart all security risks associated with Telnet. SSH is secure by its very nature, being driven off RSA and can be configured very easily on Cisco gear, not to mention, it is now the default choice to access any appliance based server’s CLI.
For configuring SSHv2 (yes, we’ll talk about v2, which is more secure) for a Cisco IOS device such as a router or a switch, you’ll need to do the following:
Example 1: Enabling SSH on Cisco IOS Router
UCRouter(config)# ip domain-name mydomain.corp
UCRouter(config)# ip ssh version 2
UCRouter(config)# crypto key generate rsa usage-keys exportable modulus 1024
!
UCRouter(config)# aaa new-model
UCRouter(config)# aaa authentication login default local
UCRouter(config)# aaa authorization exec default local
!
UCRouter(config)# username nmsuser privilege 15 password 0 C1sc0123
!
UCRouter(config)# ip ssh time-out 120
UCRouter(config)# ip ssh authentication-retries 3
Who Needs FTP When I Have SCP and SFTP!
A viable and secure replacement for FTP exists as Secure Copy Protocol (SCP) and Secure File Transfer Protocol (SFTP). SCP handles the file transfer and relies on the SSH protocol to provide authentication and security for both user credentials and data. SCP basically tunnels Remote Copy (RCP) over SSH tunnel. You can enable SCP server on Cisco IOS switches and routers to transfer firmware or any other files, securely. The following example outlines IOS configuration to enable SCP transfer:
Note: Since SCP leverages SSH, we need the commands used in previous example for configuring SSH before configuring SCP.
Example 2: Enabling SCP Server on Cisco IOS Router
UCRouter(config)# ip scp server enable
At this time the Cisco IOS device is ready to accept an incoming session from an SCP client machine, which can be setup as shown in figure 1. For the following example WinSCP client is used, which is a free SCP client.
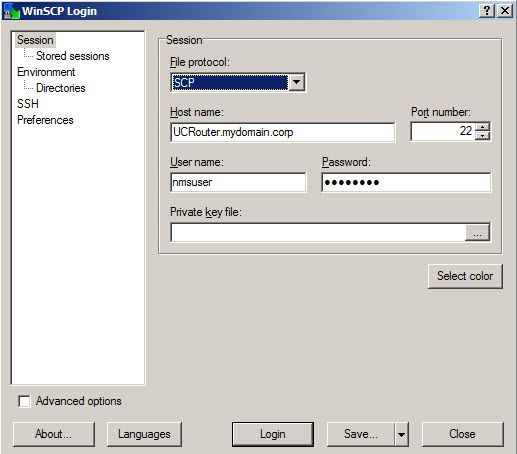
Figure 1: WinSCP client configuration
Similar to SCP, SFTP also leverages SSH to provide a secure service, allowing the application server to encrypt the data and the file transfer. Cisco UC applications, such as CUCM, CUC, CUPS, and so on, only support SFTP for secure image, update, locale, and phone firmware transfer. WinSCP can also act as an SFTP client. Just a flip of the “file protocol” option from SCP to SFTP and you have a working SFTP client.
With SNMPv3, You Just Can’t Go Wrong!
From SNMP perspective, SNMPv3 provides an application-level authentication and encryption capability that is not provided by either of other two flavors. While one could use SNMP v1 or v2c over IPSec tunnels, it is neither a scalable nor an supple solution. SNMPv3 does an excellent job to secure the data transferred between two or more entities and the NMS by enabling you to apply authentication (MD5, SHA) and encryption (DES, 3DES, AES). As of today, almost all Cisco IP Telephony applications and all the underlying infrastructure components such as routers, switches, and gateways etc. provide support for SNMPv3.
Following is a snippet of SNMPv3 configuration on Cisco IOS router:
Example 3: Cisco IOS router SNMPv3 Configuration
UCRouter(config)#SNMP-Server view NMSManager system included
UCRouter(config)#SNMP-Server group SNMPv3Group v3 priv Read NMSManager Write NMSManager
UCRouter(config)#SNMP-Server user SNMPv3User SNMPv3Group v3 auth MD5 C1sc0123 priv DES C1sc0123
The following figure shows the basic construct of Cisco Unified Communication Manager (CUCM) SNMPv3 user:

Figure 2: CUCM SNMPv3 user creation
Summary
A Cisco Collaboration network deserves to be managed as securely as it is expected to deliver. For managing the Cisco Collaboration network, infrastructure and applications ensure you do fair bit of planning before actually start managing the solution. A Collaboration solution can be built to serve users and provide resilient, supple, and robust services provided, it’s management is secure.
Author's Biography

Akhil Behl is a Solutions Architect with Cisco Services, focusing on Cisco Collaboration and Security Architectures. He leads collaboration and security projects and service delivery worldwide for Cisco Services and the Collaborative Professional Services (CPS) portfolio. He's played major role in service conception and creation for various services within Cisco Advanced Services. He has Pre-Sales to Sales to Professional Services to Delivery to Post Sales experience with expertise in Consulting, Advisory, and Guidance services. He has extensive experience in Borderless, Collaboration and Data Center portfolio. Prior to his current role, he spent ten years working in various roles at Linksys as a Technical Support Lead, as an Escalation Engineer at Cisco Technical Assistance Center (TAC), and as a Network Consulting Engineer in Cisco Advanced Services.
Akhil has a bachelor of technology degree in electronics and telecommunications from IP University and a master’s degree in business administration from Symbiosis Institute. He is dual Cisco Certified Internetwork Expert CCIE # 19564 in Voice and Security. He also holds many other industry certifications, such as PMP, ITIL, VCP, ISM, CCNA, CCSP, CCVP, ISO/IEC 27002, TOGAF and CEH.
Over the course of his career, he has presented and contributed at various industry forums such as Enterprise Connect, Cloud Connect, Cloud Summit, Interop, Cisco Networkers, and SecCon. He has several research papers published in various national and international journals including IEEE.
He is an avid blogger and maintains a blog on Unified Communications Security - http://ucsecurity.wordpress.com
| Securing Cisco IP Telephony Networks Series: Networking Technology: IP CommunicationsPublished: Aug 31, 2012 Copyright 2012
Published by Cisco Press |
This article is featured in the November 2013 issue of the Cisco TS Newsletter. Are you subscribed?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
