- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Knowledge Base
- Configure SIP TLS using CA-Signed Certificates between Call Manager and CUBE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-22-2016 10:44 AM - edited 03-12-2019 10:23 AM
This document will cover a basic SIP TLS configuration between Call Manager and a CUBE router when at the end of the configuration RTP will travel using SIP port 5061 over TLS.
-What is TLS?
Transport Layer Security (TLS), is a widely used method of securing network traffic.
Topology: Router (Branch) ---TLS-----CUCM
CUCM= 10.10.10.200
Router= 192.168.10.1
Configuration on Router:
Note: Highlighted information can be customized by you.
1- Generate RSA key on the gateway as shown below:
Branch(config)#crypto key generate rsa modulus 4096 label Branch_CA
% The key modulus size is 4096 bits
% Generating 4096 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 137 seconds)
2- Configure a Trust-point on the gateway
Branch(config)#crypto pki trustpoint Branch_CA
Branch(ca-trustpoint)#revocation-check none
Branch(ca-trustpoint)#serial-number none
Branch(ca-trustpoint)#ip-address none
Branch(ca-trustpoint)#fqdn none
Branch(ca-trustpoint)#rsakeypair Branch_CA (Same name used in the trust-point)
Branch(ca-trustpoint)#subject-name cn=Branch,dc=gerx24,ou=TAC,o=CISCO,l=RICHARDSON,st=TEXAS,c=US
Branch(ca-trustpoint)#crypto pki trustpoint Branch_CA
Branch(ca-trustpoint)#enrollment terminal pem
3- Generate the CSR that will be sent to the signer.
Branch(config)#crypto pki enroll Branch_CA
% Start certificate enrollment ..
% The subject name in the certificate will include: cn=Branch,dc=gerx24,ou=TAC,o=CISCO,l=RICHARDSON,st=TEXAS,c=US
% The fully-qualified domain name will not be included in the certificate
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
-----BEGIN CERTIFICATE REQUEST-----
MIIE3zCCAscCAQAweTELMAkGA1UEBhMCVVMxDjAMBgNVBAgTBVRFWEFTMRMwEQYD
VQQHEwpSSUNIQVJEU09OMQ4wDAYDVQQKEwVDSVNDTzEMMAoGA1UECxMDVEFDMRYw
FAYKCZImiZPyLGQBGRYGZ2VyeDI0MQ8wDQYDVQQDEwZCcmFuY2gwggIiMA0GCSqG
SIb3DQEBAQUAA4ICDwAwggIKAoICAQCzysZo72WhwVsGvwcVjRgy8TkjYVlf486G
9BbDPliFGXak9v0Zc5Xb9OzFTuLYF+iK4AZGfnpONVJwE2zUZSA/i6jXs8IJACYo
Kjv3BgPuGhVbExL+RiuUn/t2GH376fbJU9LnRvnu3eoYmytoo6LmCzOgDbHPdsmu
88+tbJ5GM9h6WPGxoJCxKFvtbKW8UtoGWfEz7nd2x3iR3x1OYfMZiHJ1wYpn7ibE
Bo4OXzvBR+c1IKC7YPRDzu9pmczfbJYu0Gz964KFWtU4PnsFxghJf+rMV2HWsn3d
E2OEDYOTLlO8OHOotsK1T4QNKZtjPRceodFweJyeQZoQvn4SVnA6ztzsiFRAmaFb
ksOnKxc4GJiYGHPK97YYDowiFXk2W22rSQ+E5sdUqmGnr50ZmHSlFN7gnhilSEtM
cED/jn9LaX4XQIlTA4imkW8oJVXP3w1pb0wwpyUcAMQl5X9kH1Xkp+jVwGpsi61k
/Q396XrSKZBG7J9PxO3epSG6QAVCbm/8M+OLstN3Ck2VKY2hE+AVvn6ia5MHE/B1
EX40BHseqoz278dgvRSfh8wX5GQaCRgZOPwuW5bGQrsi3QYomQImannMmbX6AF1g
IDm3v/IA9qcntSNt+NvNt08L6BSithTMt2/jiQS6d+g6hhn9PxU6pOuDyYZf3UK7
2X2Tez+/7wIDAQABoCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNVHQ8BAf8EBAMCBaAw
DQYJKoZIhvcNAQEFBQADggIBAA64RRLRQGIV0g0YjwSjdr7gvO4bm1uyHDMYxx/1
IMocFFJ8l+wUA4QNOGPvhrVuVJpcNXTYVkdolsBI+EQLE9gdT2uToko1LOg06BGd
dq4Jvxl/oN3UcGVUlL8N7flDCApv2vTpdc/Id619XfWtQsU5oRKQ5fCKBBZ0zyiT
9LXET6WbPcHOlVomE2cdC2AGgVNnDW78Hdb3k5ppubiQAjf/fXF6uRPwQ7ITx83j
kcazFsOrSw+y2KibbsjG0/rlR6vm5hOmqqjkz+Ap/qzEZSZKpzuiTw1rxaHZbmNe
zcqlSqTcjcBQlNscW92+VpdxBrqWJamyiVXCbwbaULLgu1nTqXn2DGaBMMoj+FhY
gsM1tz79XMFTwsX5g/me5AlbAS8fASyUAI5bVOvZM/uC2I59xVH2fbQYodIVxzHU
YvCivbT8JKT5ioi/1EeLtnQhG0zWBcoTD343F9iqXJCfxdMTtr79UpIBqHzqTfhi
7TX9iJa+KsJzM+B/O1Wj7cej3hu5RYPD80uoDj0pBo0bkX45GBaR/b6XvU5v7+hP
WaF6zN4KYunXkzdPuZkIWbNE7xzy/qEL3MfAHNEgzZn+GASTRYg3P7xSmpMLsWxv
VRage/uiPJqHr4IGynce4r8B2S5QGltZdA6U8EsowUzpLm8d06gpC/cLcgp2BvZr
0kB8
-----END CERTIFICATE REQUEST-----
---End - This line not part of the certificate request---
Redisplay enrollment request? [yes/no]: no
-Verify your certificate using the certificate decoder below
https://certlogik.com/decoder/
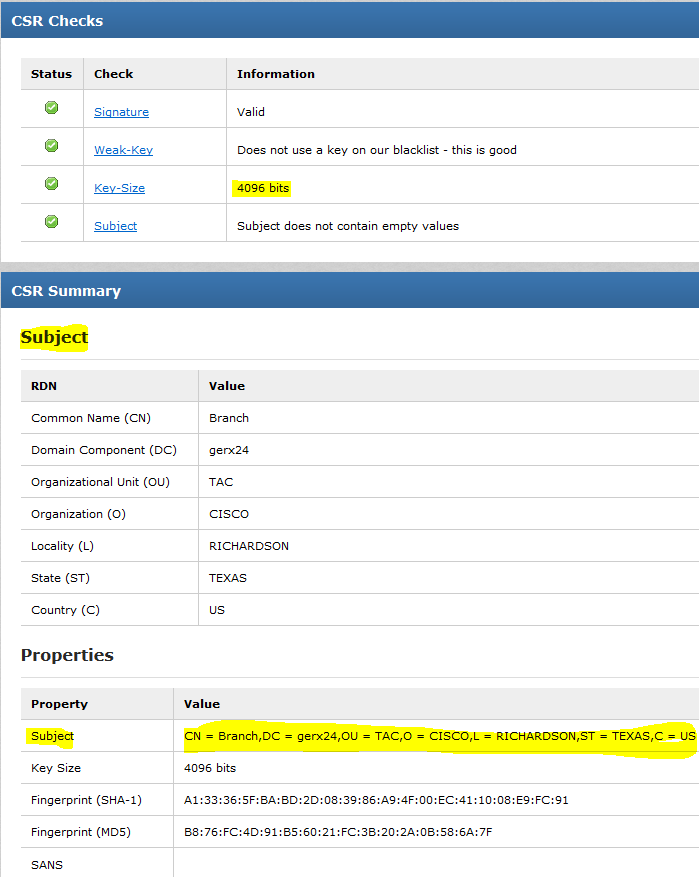
Notice that the "Subject" information matches with the router information also included in the Trust-point.
4- A this point you are ready to send this CSR to the CA-Signer.
5- The CA-Signer will send to you normally 3 certificates Root, Intermediate and Router certificate that need to be uploaded to the router and and Call Manager.
Installing Certificates
1- When you receive 3 certificates and you have not use any root certificate before signed by your CA-Signer you need to create a Trust-point dedicated for this certificate. No RSA is needed for this one.
Root certificate
Branch(config)#crypto pki trustpoint Branch_Root_CA
Branch(ca-trustpoint)#revocation-check none
Branch(ca-trustpoint)#enrollment terminal
Branch(ca-trustpoint)#crypto pki authenticate Branch_Root_CA
******* Paste the Root certificate in here *****
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDgTCCAmmgAwIBAgIQTHuIiTtqcqtDW2Z0XhW2yzANBgkqhkiG9w0BAQsFADBH
MRMwEQYKCZImiZPyLGQBGRYDbGFiMRUwEwYKCZImiZPyLGQBGRYFY2lzY28xGTAX
BgNVBAMTEEFELUNPTlRST0xMRVItQ0EwHhcNMTYwMjA1MDE0NDA4WhcNMjYwMjA1
MDE1NDA2WjBHMRMwEQYKCZImiZPyLGQBGRYDbGFiMRUwEwYKCZImiZPyLGQBGRYF
Y2lzY28xGTAXBgNVBAMTEEFELUNPTlRST0xMRVItQ0EwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQDPCU77fFdFiq+UeKYYyZU8JJKDcq3Z0r6pMgU2bKZ1
YaO+Pa90v0/CCslpzZU/8lPraX9bVGvD0hTD955MMyGMxyFNzljSWXH710TI+ykT
S+6feJd527lIE0oJGKK9T+FitXeZ+nauP+AJQ0j6DV5qMpnEL84u89wdSvhn6jag
wWlMujuoeKa2mRLWElXhpFgPL6jqr0+NcvDZScs4AS3OdXtrpBHU3jRUIiBTFawX
HxeonDSWxs4KVkKPBQCIRUtrAYfnctA63I65csUtS7KyZxXf8hfsbS7r6mzKbG63
QHdjGL+QDZkZo1IoK83kTcDLdRpe8213rl+EERGj/3xVAgMBAAGjaTBnMBMGCSsG
AQQBgjcUAgQGHgQAQwBBMA4GA1UdDwEB/wQEAwIBhjAPBgNVHRMBAf8EBTADAQH/
MB0GA1UdDgQWBBQ/HjH8zeBaq5QnVb1KzoA+oRaR/zAQBgkrBgEEAYI3FQEEAwIB
ADANBgkqhkiG9w0BAQsFAAOCAQEAf/I1rZn5HB1ncYcHHZkITOSFmYlxO42dmzRy
+58hZ+rbuwFbmW34cwgE1tjFeaa1Pm7sEK/7CdKcISR/owxjHBEHIuCqW3B9D7rt
APW4Vz8nQSthPJRx/xy+qebz/4wL7qPsAJzd2yNKdV8ribv3odSFlZco6aQUcOFn
5g1qzrTabF9oOPfvhZ3YLXWNSBLDVW2oK9RItwN3L1kDEZHk9Igg0hsiM69HoGiM
+z5noTHV5i3Z0ytj2o3JtOv0Q1pOsXph2IrRbCxi1R7Q+A1FFace4L3yEAJH7wkW
Lo4+2/+RoF1fr5KUu90HsGwIZR0iex3UQVRHIIABGyWAXOmWng==
-----END CERTIFICATE-----
Certificate has the following attributes:
Fingerprint MD5: 45374A62 C94B9CA6 621A86B5 7CA274EC
Fingerprint SHA1: FFB820FB 8F53ABDE 5B656469 6275823B 3B15402D
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully imported
-Notice that I used a Windows server to sign the certificate. Signer "AD-CONTROLLER-CA" verify it using the link https://certlogik.com/decoder/
2- At this point it is time to import the Intermediate and Router certificate using the original Trust-point used to generate the CSR.
Intermediate certificate
Branch(config)#crypto pki authentincate Branch_CA
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDgTCCAmmgAwIBAgIQTHuIiTtqcqtDW2Z0XhW2yzANBgkqhkiG9w0BAQsFADBH
MRMwEQYKCZImiZPyLGQBGRYDbGFiMRUwEwYKCZImiZPyLGQBGRYFY2lzY28xGTAX
BgNVBAMTEEFELUNPTlRST0xMRVItQ0EwHhcNMTYwMjA1MDE0NDA4WhcNMjYwMjA1
MDE1NDA2WjBHMRMwEQYKCZImiZPyLGQBGRYDbGFiMRUwEwYKCZImiZPyLGQBGRYF
Y2lzY28xGTAXBgNVBAMTEEFELUNPTlRST0xMRVItQ0EwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQDPCU77fFdFiq+UeKYYyZU8JJKDcq3Z0r6pMgU2bKZ1
YaO+Pa90v0/CCslpzZU/8lPraX9bVGvD0hTD955MMyGMxyFNzljSWXH710TI+ykT
S+6feJd527lIE0oJGKK9T+FitXeZ+nauP+AJQ0j6DV5qMpnEL84u89wdSvhn6jag
wWlMujuoeKa2mRLWElXhpFgPL6jqr0+NcvDZScs4AS3OdXtrpBHU3jRUIiBTFawX
HxeonDSWxs4KVkKPBQCIRUtrAYfnctA63I65csUtS7KyZxXf8hfsbS7r6mzKbG63
QHdjGL+QDZkZo1IoK83kTcDLdRpe8213rl+EERGj/3xVAgMBAAGjaTBnMBMGCSsG
AQQBgjcUAgQGHgQAQwBBMA4GA1UdDwEB/wQEAwIBhjAPBgNVHRMBAf8EBTADAQH/
MB0GA1UdDgQWBBQ/HjH8zeBaq5QnVb1KzoA+oRaR/zAQBgkrBgEEAYI3FQEEAwIB
ADANBgkqhkiG9w0BAQsFAAOCAQEAf/I1rZn5HB1ncYcHHZkITOSFmYlxO42dmzRy
+58hZ+rbuwFbmW34cwgE1tjFeaa1Pm7sEK/7CdKcISR/owxjHBEHIuCqW3B9D7rt
APW4Vz8nQSthPJRx/xy+qebz/4wL7qPsAJzd2yNKdV8ribv3odSFlZco6aQUcOFn
5g1qzrTabF9oOPfvhZ3YLXWNSBLDVW2oK9RItwN3L1kDEZHk9Igg0hsiM69HoGiM
+z5noTHV5i3Z0ytj2o3JtOv0Q1pOsXph2IrRbCxi1R7Q+A1FFace4L3yEAJH7wkW
Lo4+2/+RoF1fr5KUu90HsGwIZR0iex3UQVRHIIABGyWAXOmWng==
-----END CERTIFICATE-----
Certificate has the following attributes:
Fingerprint MD5: 45374A62 C94B9CA6 621A86B5 7CA274EC
Fingerprint SHA1: FFB820FB 8F53ABDE 5B656469 6275823B 3B15402D
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully imported
Router Certificate
Branch(config)#crypto pki import Branch_CA certificate
% The fully-qualified domain name will not be included in the certificate
Enter the base 64 encoded certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIGMjCCBRqgAwIBAgIKPhxKEAAAAAAAMjANBgkqhkiG9w0BAQsFADBHMRMwEQYK
CZImiZPyLGQBGRYDbGFiMRUwEwYKCZImiZPyLGQBGRYFY2lzY28xGTAXBgNVBAMT
EEFELUNPTlRST0xMRVItQ0EwHhcNMTYwNzI2MjI0NzA3WhcNMTcwNzI2MjI1NzA3
WjB5MQswCQYDVQQGEwJVUzEWMBQGCgmSJomT8ixkARkWBmdlcngyNDEOMAwGA1UE
CBMFVEVYQVMxEzARBgNVBAcTClJJQ0hBUkRTT04xDjAMBgNVBAoTBUNJU0NPMQww
CgYDVQQLEwNUQUMxDzANBgNVBAMTBkJyYW5jaDCCAiIwDQYJKoZIhvcNAQEBBQAD
ggIPADCCAgoCggIBAMiNazjW/aww/ebuahP42f8MkPKQiHymwe/uDu2c756sTzjy
7L0jXkEU8rIjxUiOzG324QvxMbAgZveVqrXfiMbKFa62E/ewI8V8qvQ05jm9NBXp
ZuwzowSJrg28zP9TDJ8Hoolg9u3nVGneGV4Cu+uUnY/xLaXhokMSkZBuUYYwC1Q+
kB+QMkHQ3w2GDyDWWlmC3zVqZBk6RiflRozYuJYOcYTUlylnMDJ21nfXitsk+59p
bFeH2/p4vGsQrz2+9suA0eT+5vG+o3+2l7T+qJeCIHOkYYJhI3VHWgqjThhckZgE
cB4d7GA0d/yCDWIVrDyK3exgvKiVMYQytpXKe46/5cKNkf+Ay4TdYcKQXg0toQFn
QYNlA8ld0j0IKJtyYT9g4vdx27DYAIdm/aOYanzktE/L75ZLkI8GiFT/938wGsuV
eeE7jvW85p3w+D2KlkNzNJcOQDyB2ph5/YKglXvmW01yiMDfTV8qJ00QBelZq4wL
o8zoFtdQxITHjLUhgReUcKKalszIrMe4YuBVBt+p0pr3a7gKf7rwg40aSUHOVRJ8
b8vZKEj4Mc7ZQnTlxmRHo0esjD6VXqZ8dUKe2Y0/eFtF9QA0MS93m0IDuB0ZnDap
7npKW2cYdJ+cqCJhBFA6lSLu1sPsmFfYvf70fXGfKpcGrf4IQAv1rm3qp8BzAgMB
AAGjggHsMIIB6DAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0OBBYEFLO3gMJUesMmMgXB
Us3zj7B1htcbMB8GA1UdIwQYMBaAFD8eMfzN4FqrlCdVvUrOgD6hFpH/MIHSBgNV
HR8EgcowgccwgcSggcGggb6GgbtsZGFwOi8vL0NOPUFELUNPTlRST0xMRVItQ0Es
Q049QUQtQ09OVFJPTExFUixDTj1DRFAsQ049UHVibGljJTIwS2V5JTIwU2Vydmlj
ZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1jaXNjbyxEQz1sYWI/
Y2VydGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNSTERp
c3RyaWJ1dGlvblBvaW50MIHABggrBgEFBQcBAQSBszCBsDCBrQYIKwYBBQUHMAKG
gaBsZGFwOi8vL0NOPUFELUNPTlRST0xMRVItQ0EsQ049QUlBLENOPVB1YmxpYyUy
MEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9
Y2lzY28sREM9bGFiP2NBQ2VydGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0
aWZpY2F0aW9uQXV0aG9yaXR5MA0GCSqGSIb3DQEBCwUAA4IBAQCPTtYDG2V9hg1f
n7xQU8UgImvIbwlBvniss6jmrqZhrkC9+rIcEuED6lapoPsC7+vwRW9NT+oPXGpY
Qcaj2w08osr3uLT05OuDRDD3kzR9G7eQbT0PgA7EJiR5sZI9gnvxrqRBLW+5Flfh
YYDeowWfWNjZVc9WKJArDY4eHfqs+EvXw8mpkFnFUVlUCb4g9CqMk3dSLLJ6o+D/
rnFtfNN8eXfbXVd7a+PMJv3If/wccmfnvGLb6uqXFDqqVU5/uWVW/NtQNU7REps/
F5DaKIGSdsDs6vein2xOAiNbz5NQbqRsusga5gS+SS2fpg92MnjWQi2nRbor/UKQ
nvAG/yEX
-----END CERTIFICATE-----
% Router Certificate successfully imported
Note: The Intermediate certificate procedure will be done only if you get an intermediate certificate otherwise you need to do only the authenticate with the "root certificate" and the import with the "router certificate" and you can use the same Trust-point so you do not need to create a single one for the Root certificate.
6- At this point the Router should have the "Root" and "Router" certificate signed by the same CA-Signer and we need to include under the Sip-ua the command that will allow the trust-point to be use to authenticate the root certificate
Branch(config)#sip
Branch(config)#sip-ua
Branch(config-sip-ua)#crypto signaling remote-addr 10.10.10.0 /24 trustpoint Branch_CA
Call Manager
7- Go to Call Manager and generate a Call Manager CSR.
7.1 -->Send the CSR to the signer (They will give us the ROOT and the Call Manager).
7.2 -->Upload the ROOT certificate as Call Manager-Trust and the Call Manager as "Call Manager".
7.3-->Restart Cisco Call Manager.
7.4-->Make sure CUCM is in mix mode and that the Subject name on the "Security Profile" configured on the trunk is the one from the router.
Enable mix mode on CUCM with the CLI command "utils ctl set cluster mix mode"
**** If you use the same "SIGNER" for both Router and Call Manager you need to upload just the Call Manager certificate to the Router *******
8- Create a new Trust-point on the router for Call Manager
Branch(config)#crypto pki trustpoint Branch_CUCM
Branch(ca-trustpoint)#revocation-check none
Branch(ca-trustpoint)#enrollment terminal
Branch(ca-trustpoint)#crypto pki authenticate Branch_CUCM
*Use the authenticate command to upload the Call Manager signed certificate*
9- On the dial-peer going to CUCM add the command "session transport tcp tls"
dial-peer voice 1 voip
description "Connection_to_SP"
destination-pattern 80..$
no modem passthrough
session protocol sipv2
session target ipv4:10.10.50.1
session transport tcp tls
voice-class sip options-keepalive
dtmf-relay rtp-nte
codec g711ulaw
no vad
10- Verify the SIP TLS communication enabling the "SIP Options" on the SIP Profile and adding to the dial-peer the command "voice-class sip options-keepalive"
Output should be as the following:
From Router:
Jul 26 23:33:05.036: //-1/xxxxxxxxxxxx/SIP/Msg/ccsipDisplayMsg:
Sent:
OPTIONS sip:10.10.10.200:5061 SIP/2.0
Via: SIP/2.0/TLS 192.168.10.1:5061;branch=z9hG4bK252194D
From: <sip:192.168.10.1>;tag=1EFB1858-1601
To: <sip:10.10.10.200>
Date: Tue, 26 Jul 2016 23:33:05 GMT
Call-ID: 22AD67EA-52C011E6-B680F81C-B2621099@192.168.10.1
User-Agent: Cisco-SIPGateway/IOS-12.x
Max-Forwards: 70
CSeq: 101 OPTIONS
Contact: <sip:192.168.10.1:5061;transport=tls>
Content-Length: 0
Received from rom Call Manager:
Jul 26 23:33:05.040: //9229/000000000000/SIP/Msg/ccsipDisplayMsg:
Received:
SIP/2.0 200 OK
Via: SIP/2.0/TLS 192.168.10.1:5061;branch=z9hG4bK252194D
From: <sip:192.168.10.1>;tag=1EFB1858-1601
To: <sip:10.10.10.200>;tag=508105887
Date: Wed, 27 Jul 2016 00:05:16 GMT
Call-ID: 22AD67EA-52C011E6-B680F81C-B2621099@192.168.10.1
CSeq: 101 OPTIONS
Allow: INVITE, OPTIONS, INFO, BYE, CANCEL, ACK, PRACK, UPDATE, REFER, SUBSCRIBE, NOTIFY
Content-Length: 0
Verify the open connections on the Router with the command:
Branch#show tcp brief all
TCB Local Address Foreign Address (state)
8AD8D670 192.168.10.1.24793 10.10.50.1.5061 ESTAB
8914E630 10.198.28.189.22 10.225.133.72.58079 ESTAB
89738680 192.168.10.1.5061 10.10.10.200.48417 ESTAB
89A82D0C 10.198.28.189.22 10.225.133.72.52039 ESTAB
88EC520C 192.168.10.1.5061 10.10.50.1.18791 ESTAB
CUCM= 10.10.10.200
Router= 192.168.10.1
Troubleshooting debugs:
debug crypto pki api
debug crypto pki callbacks
debug crypto pki messages
debug crypto pki transactions
debug ssl openssl errors
debug ssl openssl msg
debug ssl openssl states
debug ip tcp transactions
debug ccsip verbose
Related links
regards,
Gerson Fabian Morales Marin (gersomor)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for the helpful step-by-step configuration.
Could you please also explain how the step in number 8 should be if I use a different signer/CA for the CUCM ?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: