For the On-prem Cisco Conferencing solution Cisco Meeting Server, the C2W connection between the WebBridge and CallBridge uses the concept of certificate pinning to prevent the Man In the Middle Attack.
But what is the Certificate Pinning and what is the relation with the MMP commands callbridge trust c2w and webbridge3 c2w trust?
In this article you will understand the concept.
Traditionally, SSL Handshake consists on the validation of the server's certificate, let's say collab.com. The validation is done using the CA's certificate located in the certificate store of the web browser.
The certificate store contains several CA Certificates, may be more than 100.
If at least one CA delivers by mistake or more likely to conduct an attack a valid certificate for example *.collab.com, attackers are able to launch a Man In The Middle Attack.
in order to prevent this attack, it is possible to use the SSL protocol in another way, by creating an association between the domain name of a site (www.collab.com) and the certificate or certification authority expected. Thus, only the a certificate (of collab.com) signed by one of the specific certification authorities will be accepted and if the certificate of collab.com signed by another CA is presented, it is not trusted.
Certificate pinning can be explained with a simple words: Is this connection secure with a valid certificate and is it signed by the CA I’m expecting?
For Cisco Meeting Server, the C2W connection between the WebBridge and CallBridge uses the concept of certificate pinning to prevent the Man In the Middle Attack.
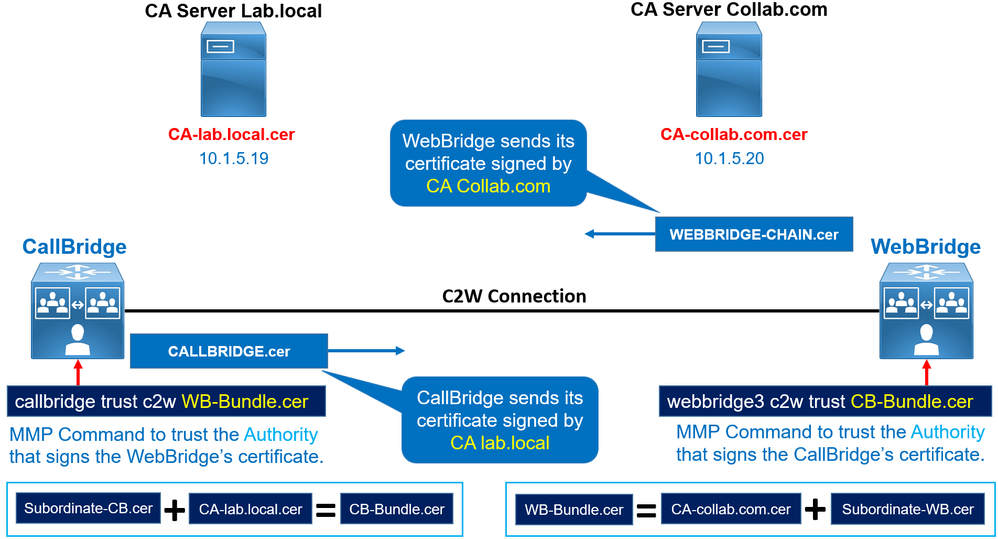
This is done by the webbridge3 c2W trust < Call Bridge Trust certificate Chain > and callbridge trust c2W < Web Bridge Trust certificate Chain > command.
The webbridge will trust certificates of callbridges that have been signed by one of those in its trust store, set by the < webbridge3 c2W trust < Call Bridge Trust certificate Chain > command.
The callbridge will trust webbridges that have certificates signed by one of those in its trust store, set by the < callbridge trust c2W < Web Bridge Trust certificate Chain > command.
In this scenario two differents CA are used to sign :
1. The WebBridge certificate chain WEBBRIDGE-CHAIN.cer is signed by CA-collab.com server using a bundle of root and subordinate certificates.
2. The CallBridge certificate CALLBRIDGE.cer is signed by the CA-lab.local server using a bundle of root and subordinate certificates.
Basically:
You tell the CallBridge service ----> trust only the WebBridge's certificate WEBBRIDGE-CHAIN.cer signed by the certificate WB-Bundle.cer. It's enforced with the callbridge trust c2w WB-Bundle.cer command.
You tell the WebBridge service ----> trust only the CallBridge's certificate CALLBRIDGE.cer signed by the certificate CB-Bundle.cer. It's enforced with the webbridge3 c2w trust CB-Bundle.cer command.