- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Nexus 3524-X and radius (NPS) not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Nexus 3524-X and radius (NPS) not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2020 07:06 AM
Hi there,
I'm trying to get it four Nexus 3524-X to login authenticate with windows 2019 NPS via radius protocol, but so far no luck.
I see in the NPS logs there 2 of the switches are sending radius requests, but somehow NPS doesn't like them, i have compared the requests to the requests that older Nexus 3548 make, and the only difference i can see is that the older ones are sending an extra hostname according to the NPS log. The older Nexus 3548s are authenticating fine, using image 9.6.0.2.A1.1d
2 of the other switches, i don't even see them in the NPS logs.
But the common denominator is that all 4 switches say "AAA servers are not reachable"
In the event viewer, in the system events, i can see that the 2 switches that are visible in the NPS logs, are sending something every 5 seconds, that the NPS doesn't like, and it says "error". no details unfortunately.
All four switches came with 9.2.2 image, and i have tested the current suggested image 7.0(3) I7 (7)
config i have been using:-
radius-server retransmit 3
radius-server deadtime 5
radius-server host ip key 7 *** auth-port 1645 acct-port 1645 authentication accounting
radius-server host ip key 7 *** auth-port 1645 acct-port 1645 authentication accounting
aaa group server radius radius-login
aaa authentication login default group radius-login
aaa authentication login console local
aaa authentication login error-enable
Has anyone seen this before? What else can i try to find out the cause of the problem?
- Labels:
-
Nexus Series Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2020 07:43 AM
Hello Ara,
I hope you are doing great,
From the configuration you have posted it seems good, you could also add the below command:
switch(config)# ip radius source-interface mgmt 0
This way the request will source to that interface or the VLAN where the AAA servers are, now for some switches there are basic reachability since you saw logs on the event viewer. Please make to also configure all the switches are RADIUS Clients in the NPS switch and select the Vendor Name "Cisco" so that the Radius can understand the Radius format from the nexus switches. Below the steps:
To add siwtch as RADIUS client:
- Logon to server with NPS using account with admin credentials.
- Go to Start / Administrative Tools and then click Network Policy Server.
- Expand RADIUS Client and Servers.
- Right-click on RADIUS Clients and click New from context menu.
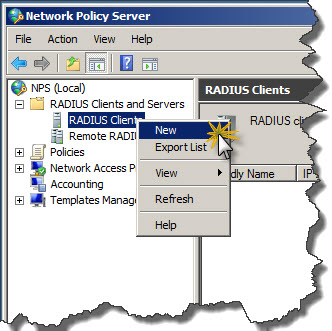
- In New RADIUS Client window Settings tab enter:
- Friendly name of the switch – name to recognize router, usually same as hostname.
- Address (IP and DNS) – IP address of the router or hostname – if hostname used proper hostname needs to be registered in DNS prior to RADIUS configuration.
- Shared secret – passphrase which was configured on router which will allow to identify router when requesting AAA from RADIUS.
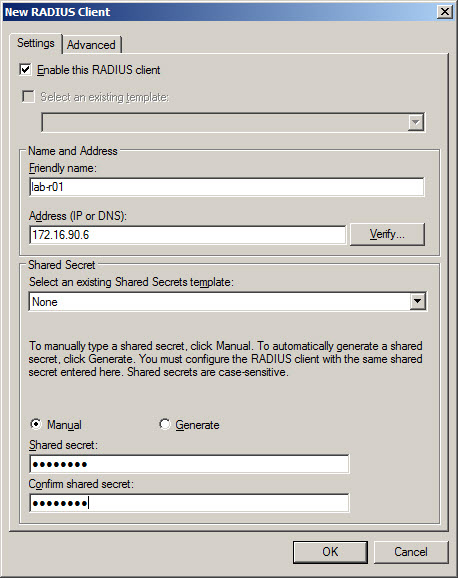
- In New RADIUS Client window Advanced tab enter:
- Vendor name – Cisco – as in this example Cisco switch will communicate with RADIUS.
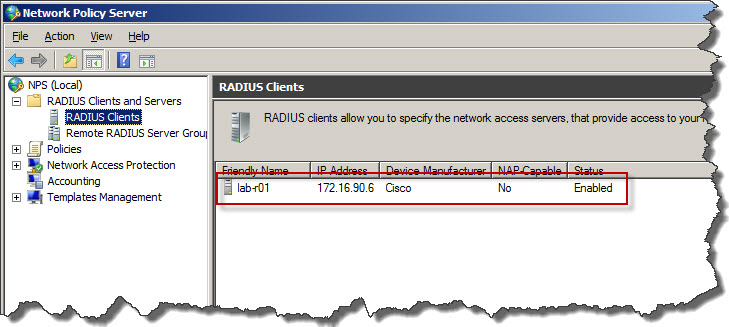
- Once confirmed with OK we will see that switch has been added to RADIUS configuration as client.
Probably you could have all of these set up already, please provide a wireshark capture so this way we could see if there could be something else, make sure that if there is any some sort of IPS/NGIPS device to add a trust exception or firewall to allow traffic.
I hoped I helped you, please rate all helpful posts, and keep us posted,
David Castro,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 05:35 AM
In my case, it seems the solution was to write the following
radius-server host ip key 0 cleartextpassword authentication accounting
instead of
radius-server host ip key 7 "encryptedpassword" authentication accounting
The password was getting garbled in latter command.
Cheers
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
