- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Non vPC Peer Link Mandatory
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Non vPC Peer Link Mandatory
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2018 09:27 AM
Hey All,
Quick question hopefully.
I have Nexus 9K vPC deployment with a number of VLANs that are used to provide connectivity to two Cisco ASA firewalls in a HA pair. The ASA firewalls are single attached to each peer switch and do not use port-channels. To allow the firewalls to communicate for HA, I am currently allowing these VLANs over the peer-link.
I have read that VLANs such the ones used above should be placed on a separate non-vPC peer link. Is that correct? If so, is this a recommendation or mandatory for support purposes? For simplicity, I would ideally keep them on the peer-link and not lose a couple of 10GbE ports for another inter-switch connection but I'm not sure if I will run into issues if I do.
Thank you
- Labels:
-
Nexus Series Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2018 11:16 AM
Hello CiscoGeek,
I hope you are doing great,
Analizing what you just stated above, you have a subset of VLANs to intercommunicate the Failover link between the ASAs that´s why you are connecting the ASAs to the N9Ks, similar to the below image, ignore the vPC for data traffic in the drawing. It is not optimal to have those VLANs in the vPC peer-link since you are connecting them as "orphan ports" to the N9k vPC pair but it could work anyways and I´ve seen it working, though as you stated it is not recommended, in the below drawing you can see a trunk allowing VLAN 5-6 that´s the recommended when having an scenario like the one you explained and excluding the VLANs from the vPC peer-link.
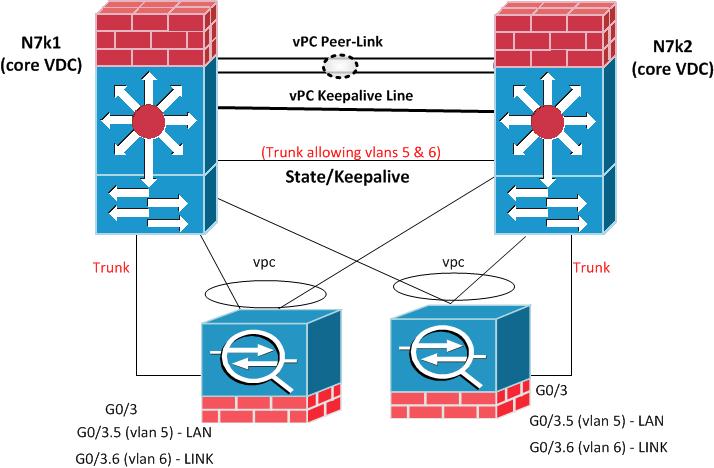
Now having it this way can introduce also an issue if you have "peer-switch" in the vPC domain configuration because with peer-switch enabled, each Nexus 7000 switch or in your case each n9k generates BPDUs with the root bridge set to the virtual bridge ID and the designated bridge set to the physical bridge ID. Since the priorities are the same, all non-vPC connections always forward on the link connected to the Nexus 7000 switch with the lower bridge ID (N7K-1 in this example) and block on the links connected to the Nexus 7000 switch with the higher bridge ID (N7K-2 in this example) in your case would be the N9k2. So to avoid this issue you can set the spanning tree priority higher on the second switch for the non-VPN VLANs:
spanning-tree vlan 5 priority 16384
Also if the extra link or if you keep if functioning in the vPC peer-link you have to use the command:
vpc orphan-port suspend
To avoid splin brain situations.
Let me know if this clarifies the scenario for you.
The best practice here is to have a vPC and you can find below the best practices:
Please mark the question as answered, if it helped you.
Thanks,
David Castro,
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
