- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Re: VXLAN BGP EVPN: Is there any problem on connect Border Leafs to the external network using OSPF
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2020 07:24 AM
Hello,
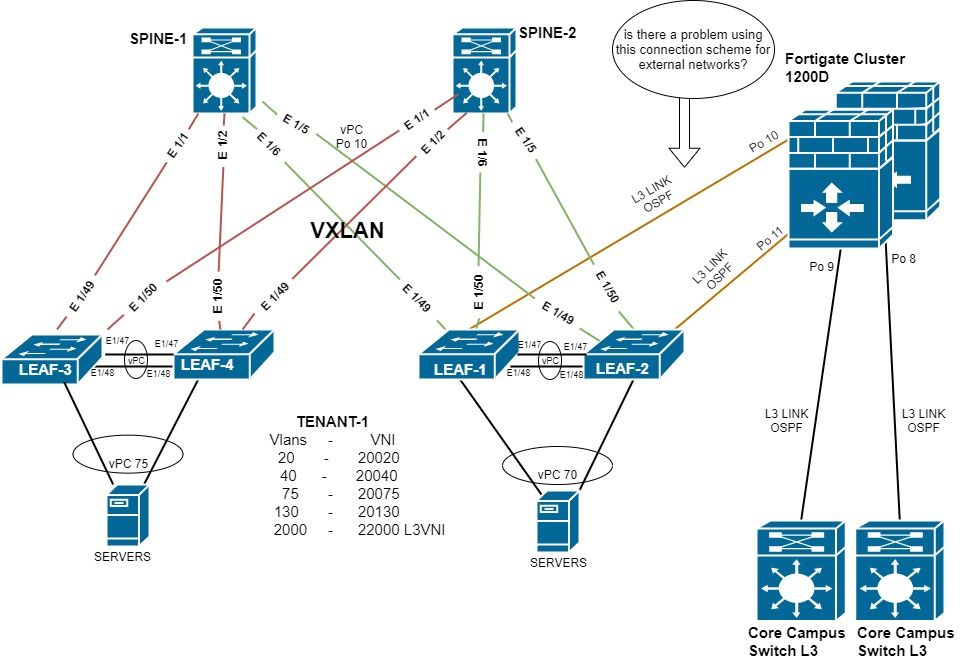
We are implementing VXLAN BGP EVPN in our Datacenter. Our VXLAN Fabric consists of two Nexus 9364c Switches (Spines) and four Nexus C93108TC Switches (Leafs). The Leaf switches are forming two pairs of vPC VTEP Switches (Leaf1 with Leaf2) and (Leaf3 with Leaf4).
1-) Would there be a problem on connect the Border Leafs to the external network with OSPF instead eBGP?
2-) What should we take into account to implement this type of connection to the external network? (One OSPF link to the external network on each Leaf Border)
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2020 09:42 AM
Hi Carlos,
Assuming that both units within the Fortigate cluster are able to send an identical LACPDU, then Po10 and Po11 could be combined into a single vPC. Since vPCs are Layer 2 constructs, this means your OSPF adjacencies to the Fortigate firewalls would be an SVI in each respective tenant VRF.
I did not find any documentation explicitly stating that this is supported, but the NextGen DCI with VXLAN EVPN Multi-Site Using vPC Border Gateways White Paper (which places Border Gateways into a Border Leaf role) indicates that this is supported.
With this being said, I would recommend using Layer 3/routed links between each border leaf and the Fortigate cluster if possible. I would expect you to see just as good performance in failover scenarios with Layer 3/routed links as you would with routing over vPC. Furthermore, Layer 3/routed links would involve less technology (since vPC is no longer a consideration), which means there is one less point of failure to be concerned about.
I hope this helps - thank you!
-Christopher
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2020 01:15 PM
Hi Carlos!
This topology is certainly supported. I highly recommend reviewing the "Configuring External VRF Connectivity and Route Leaking" chapter of the Cisco Nexus 9000 Series NX-OS VXLAN Configuration Guide for details on how to configure this, as well as caveats for this type of topology. Specifically, the "Configuring VXLAN BGP EVPN with OSPF for VRF-lite" section contains a configuration example that is very similar to your topology.
Depending on the size of your network, you may also be interested in advertising a default route into the tenant VRF of the VXLAN fabric as opposed to redistributing your entire OSPF routing table into BGP. This is particularly useful if these border leafs are the only exit points for north-south traffic in your fabric. You can review a configuration example for this option with the "VXLAN BGP EVPN - Default-Route, Route Filtering on External Connectivity" section of the aforementioned document.
I hope this helps - thank you!
-Christopher
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2020 08:13 AM
Hello Christopher!
Thanks for your response.I have one more question. Would it be okay if we configure the two links to the external network (fortigate) using multichassis port-channel (vPC)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2020 09:42 AM
Hi Carlos,
Assuming that both units within the Fortigate cluster are able to send an identical LACPDU, then Po10 and Po11 could be combined into a single vPC. Since vPCs are Layer 2 constructs, this means your OSPF adjacencies to the Fortigate firewalls would be an SVI in each respective tenant VRF.
I did not find any documentation explicitly stating that this is supported, but the NextGen DCI with VXLAN EVPN Multi-Site Using vPC Border Gateways White Paper (which places Border Gateways into a Border Leaf role) indicates that this is supported.
With this being said, I would recommend using Layer 3/routed links between each border leaf and the Fortigate cluster if possible. I would expect you to see just as good performance in failover scenarios with Layer 3/routed links as you would with routing over vPC. Furthermore, Layer 3/routed links would involve less technology (since vPC is no longer a consideration), which means there is one less point of failure to be concerned about.
I hope this helps - thank you!
-Christopher
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2020 10:21 AM
Christopher,
Thank you very much. Your views have helped us a lot. We want to know your opinion about the design we want to implement.
We plan to configure the Firewall as an ABR. The external network will use OSPF Area 0 and the links to the Border Leaf will use OSPF Area 10. We will configure area 10 in the Firewall as stub-no-summary so that it only shares a default route to the Border Leafs instead of the entire OSPF table. The Leaf Borders will redistribute the default route learned by OSPF to the other Leafs via BGP, that way if a link fails the Border Leaf would stop advertising the default route and the packages will go through the Border Leaf that has the active link.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide