- Cisco Community
- Technology and Support
- Security
- Email Security
- Re: Cisco ESA Message scanning vs Virus infected message
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 11:28 PM
Dear all.
could anyone tell me what is the difference between Message scanning and Virus infected message?
When i send EICAR test virus inside notepad ESA catch it and deliver it by dropping only virus infected attachment.Instead new txt file was added. I tested again. this time i sent EICAR test virus code only in message. email delivered to user with warning message and txt file about virus.
Solved! Go to Solution.
- Labels:
-
Email Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 03:55 PM
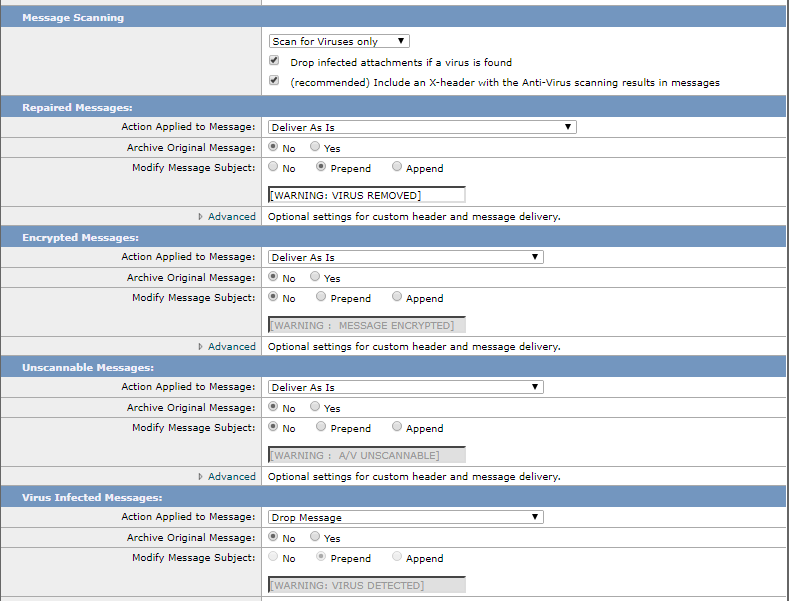
With your settings with scan for viruses only and drop infected attachment if virus is found check box.
This opens the "Repaired Messages" action you see here where we will remove the attachment and place another .txt file showing the attachment which was removed and deliver the base mail content to the end user.
If you un-tick drop infected attachment, any attachments with any viral signatures will result in the immediate "Drop" action you also have at the bottom of the screenshot.
Virus Repair typically can occur where the Sophos engine is able to detach the viral content off an attachment and safely strip that part before sending in the email and rest of the attachment, where the repair does not work - it'll run the VIRUS REMOVED and strip the attachment and replace with a text.
Regards,
Mathew
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 03:55 PM
With your settings with scan for viruses only and drop infected attachment if virus is found check box.
This opens the "Repaired Messages" action you see here where we will remove the attachment and place another .txt file showing the attachment which was removed and deliver the base mail content to the end user.
If you un-tick drop infected attachment, any attachments with any viral signatures will result in the immediate "Drop" action you also have at the bottom of the screenshot.
Virus Repair typically can occur where the Sophos engine is able to detach the viral content off an attachment and safely strip that part before sending in the email and rest of the attachment, where the repair does not work - it'll run the VIRUS REMOVED and strip the attachment and replace with a text.
Regards,
Mathew
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 11:58 PM
Greate explanation thanks so much.
yesterday we got virus was sent as pdf. esa saw that attachment name as /xbf/xef/....../xbf.pdf. is it possible to create regular expression for such a filename? have you ever seen such filename?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 02:18 PM
That looks like a UTF-8 encoded filename which is why it came up like it.
I would imagine it's in a different language.
I believe you can get the entire string and convert it using tools online.
Regards,
Mathew
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 10:23 PM
Actually it was virus infected file that was sent 3 days ago. and sophos didnt catch. i wrote about that.
i just wanted to block filename if sophos didnt catch it. do you think this is best approach for our situation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 10:42 PM
Hi Ccns90,
I'd pull a copy of the email from the recipient mailbox and open A TAC case with the message attached to it to ensure that the file is marked as malicious in future. You can also run the file SHA through https://talosintelligence.com/talos_file_reputation to confirm its current status before logging the TAC case.
As a stop gap measure I'd also suggest creating a dictionary for Filenames. Create a Content Filter to Quarantine emails with attachments that match the terms in the dictionary. Enable this for your relevant incoming mail policies.
Content Filter Condition:
Attachment File Info contains term in content dictionary
With the content filter in-place you can add file names quickly in response to a zero-day or targeted exploit situation.
Action:
Quarantine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 01:08 AM
Hi. i created dictionary for malicious filenames. and added \xef\xbf\ inside it (without .pdf extention). then created content filter accordingly. I tested buy sending new created pdf as \xef\xbf.pdf on linux. but this time amp got it as malicious file. i didnt understand if amp catch \xef\xbd named file when i send, why it was not able to real malicious file. when i looked at event the file name as same as i just created
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 02:50 AM
Hi Ccns90,
It's possible the AMP definitions have updated between the first file and the second, however AMP normally works using the SHA and not the filename to allow for malicious files having the same content and different names. Did you copy the original file or create a new pdf with the same name?
Cheers,
Shane.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 04:11 AM
The interesting part is that logs shows the file name as \xef\xbf\..(so on).pdf but when message arrives to users file name shown as FOREXAMPLE.pdf. i created content filter for \xef\xbf\...(so on).pdf instead of FOREXAMPLE.pdf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 04:21 AM
Hi Ccns90,
I'd log a TAC case, give them copies of the message tracking, a copy of the file and the content filter rules.
Regards,
Shane.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 02:15 PM
Typically if the logs show a UTF8 encoded email and you see it in the inbox, the MUA typically decodes/re-encodes to a readable format.
On the ESA though - i believe you should be able to catch it using FOREXAMPLE.pdf rather than the UTF8 encoded name.
But as Shane shared, I strongly recommend to have the ticket opened so we can review it and see why it didn't catch properly.
Thanks for bringing this up.
Regards,
Mathew
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2019 03:05 AM
Thanks a lot. i block it with subject and content. Subject and message never changes.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide