- Cisco Community
- Technology and Support
- Security
- Email Security
- ESA with 3 interfaces
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2020 02:50 PM
Hi guys,
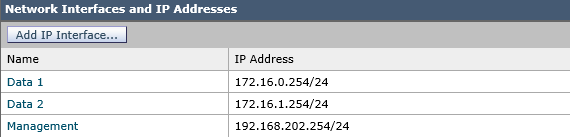
I setup a simpleLAB with ESAv and SMAv. I already configure the ESAv with the following configuration:
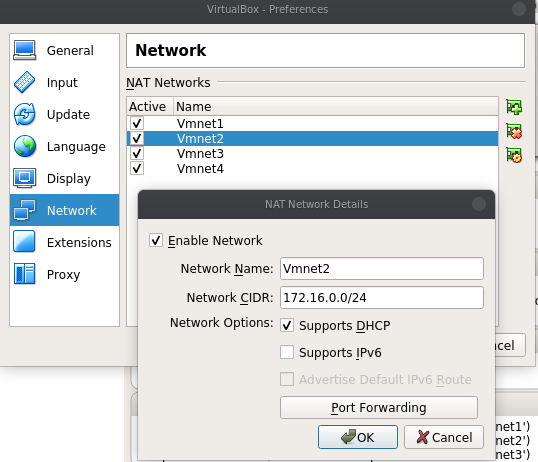
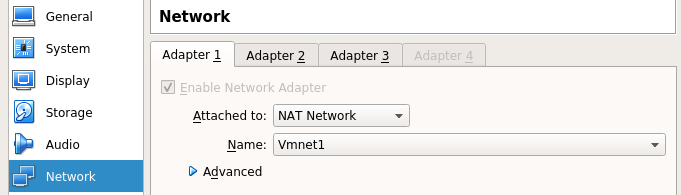
From VirtualBOX I setup 3 virtual Adapters on Vmnet1 (192.168.202.0/24), Vmnet2 (172.16.0.0/24) and Vmnet3 (172.16.1.0/24).
Ex Vmnet2 configuration:
Ex of Vmnet1 configuration on VM.
From ESA (Data1) I can ping all the other hosts on that network, from Data 2 the same also for Management.
The problem is that I cannot ping From Data 1 to Data2 and vice versa, I tryed also with telnet port 80, 443 and 25 but the traffic not pass the ESA from outside to inside, is this the normal behaviour?
I know that ESA is not a router, but something is escaping me here or not? I don't want to go further in the settings if I don't have the network working properly in VirtualBOX.
Thanks in advance
Solved! Go to Solution.
- Labels:
-
Email Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 06:56 AM
Multiple interfaces on an ESA are typically used so that one ip/listener is in the DMZ, one in your internal network, and one for management, each with its own set of security rules/acls, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 06:56 AM
Multiple interfaces on an ESA are typically used so that one ip/listener is in the DMZ, one in your internal network, and one for management, each with its own set of security rules/acls, etc.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide