- Cisco Community
- Technology and Support
- Security
- Email Security
- Re: YUI vulnerability on ESA and SMA!!!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2021 01:02 PM - edited 12-11-2021 01:07 PM
this yui version is also running at 14.x version of WSA/ESA/SMA. Right now yui has released 3.6 version and cisco is running what??!!
there are multiple bugs mention this vulnerability but for very old versions like 9.x
is this valid?? Are there any fixes?!
Solved! Go to Solution.
- Labels:
-
Email Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 08:14 AM
Hello,
Thank you for providing the CVE and defects. While YUI may still be used on later builds, we modified some of the back-end files to no longer impact our product. It has been fixed starting in the Known Fixed Releases listed in the respective defect.
You can also confirm any 3rd party software in use by reviewing our Open Source release notes.
Thanks!
-Dennis M.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2021 06:26 PM
Hello,
It does not look like you have provided a CVE or any Cisco bugs. This would be important information for any vulnerability you're looking for details on.
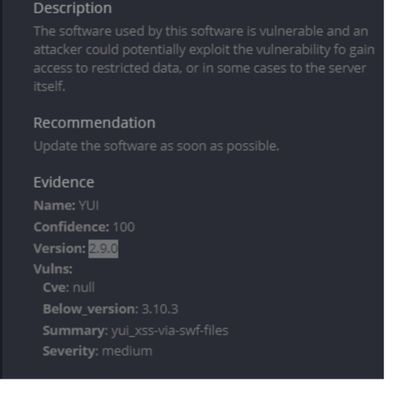
Also, where did you obtain the screenshot from? Is this a scanner you ran? If so, against what?
Thanks!
-Dennis M.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2021 11:04 PM
Hello,
Thanks for your reply!
I saw multiple bugs reported for older versiosn:
CVE-2013-6780
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCur89626?rfs=iqvred
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCur44409?rfs=iqvred
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCur89624?rfs=iqvred
Yes, the SS is from our scanner.
Kind Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 12:59 AM
Hi again,
I tried to replicate the behavior of the XSS but It didn't succeed, I suppose because it has been fixed (?).
http(s)://domain.com/yui/uploader/assets/uploader.swf?allowedDomain=\"})))}catch(e){alert('XSS');}//
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 08:14 AM
Hello,
Thank you for providing the CVE and defects. While YUI may still be used on later builds, we modified some of the back-end files to no longer impact our product. It has been fixed starting in the Known Fixed Releases listed in the respective defect.
You can also confirm any 3rd party software in use by reviewing our Open Source release notes.
Thanks!
-Dennis M.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide