- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Re: Cisco Secure Endpoint - Exclusions - Epic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Secure Endpoint - Exclusions - Epic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022 06:35 PM
I am currently running a project where we are updating Cisco Secure Endpoint on all over our servers from 7.3.15 to 7.5.5. Since we first deployed what was originally known as Cisco AMP we have experienced 100% CPU issues with a fair amount of our Epic servers. The exclusions we received from Epic have not completely resolve our issues. When enabling debugging and capturing log files I'm not able to find anything that is specific to Epic to indicate what needs to be whitelisted. The servers in question have the most issues when there is an update being installed and these servers have IIS setup for the Epic. If anyone has any insight on what I exclusions we should be using I would greatly appreciate it.
- Labels:
-
AMP for Endpoints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 05:20 AM
Carl,
Without duplicating your setup or logs it is difficult to say what to exclude. If you'd like someone to look at the logs for you I suggest opening a TAC case and attaching debug logs. If you'd prefer to do the investigation yourself, I'd recommend using this tool from CiscoSecurity.
Thanks,
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 05:44 AM
I haven't used this tool before as generally I used a powershell script I downloaded called "amphandlecount.ps1" which generates several files that breaks things down into a CSV by giving time, process, and path being looked at by AMP. I tried using this tool but not getting very far as I'm running command as administrator and giving a permission denied message.
However, really I'm just looking to gage someone that has had to troubleshoot setting up AMP exclusions with Epic seeing as how big of a program Epic is in the healthcare world. I can't imagine I'm the first one to deal with this issue. Epic has provided general exclusions for AV programs which we have implemented but still continue to see 100% CPU issue with our servers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 09:17 PM
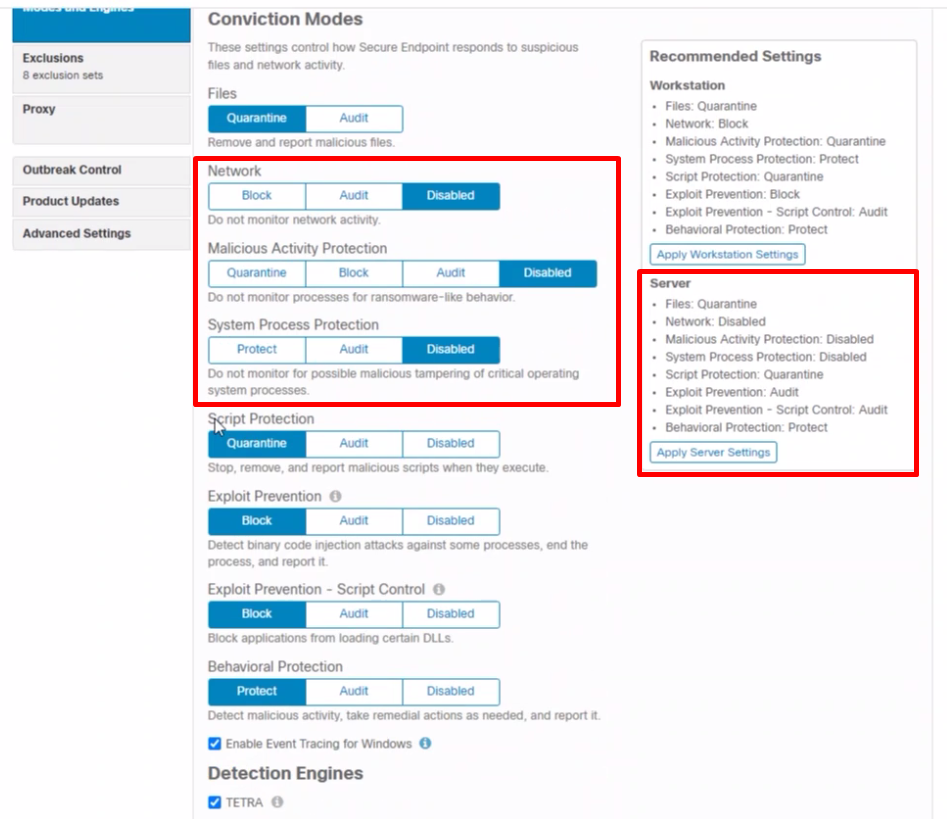
I will have to agreed with Matt on opening TAC case since you are not able to run the GitHub script, however you also mentioned that these machines are servers and you see the most issues during updates. Well the other thing that might be causing the issue besides exclusions in your case is certain engines that we usually recommend to exclude/disable for servers unless you verify that they are not causing any harm.
I would like to point out in our Secure Endpoint Deployment Strategy Guide: PAGE #21 - Server
https://docs.amp.cisco.com/en/SecureEndpoint/Secure%20Endpoint%20Deployment%20Strategy.pdf
Also MAP could potentially hammer performance in certain scenarios, that’s why we are giving two examples for the customers to start with and work through. One for workstations and one for servers.
You can test these settings as well and I would start with Network first. In very rare occasions we seen that network driver could impact performance as well. To completely disable the Network including the Driver you will have to install the secure endpoint with skip DFC flag for NETWORK engine to be fully disabled using command line switches
Command Line Switches for Cisco Secure Endpoint Installer
Please be aware that setting policy to AUDIT is essentially the same as running the policy in PROTECT the only difference in AUDIT is that the AMP will not take any action such as removing threat or blocking, how ever the engine itself is still fully functional and it’s working, meaning scanning and placing handles on files and process is still in place and it will still cause high CPU.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide