- Cisco Community
- Technology and Support
- Service Providers
- Metro
- Re: 3750 QOS limitation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
3750 QOS limitation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2010 08:11 AM
We are trying to do a simple setting and it doesn t seem to work. We are maybe forgetting some settings.
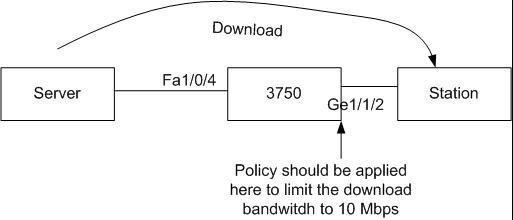
The 3750 is simply configure with one VLAN (ID4) . This lan is internal and the server for dowlaod testing is set in it
The port fa1/04 is in this vlan
The following policy-map has been defined
ROUTING#show policy-map
Policy Map V4
Class VLAN4
Police cir 10000000 bc 4500
conform-action transmit
exceed-action drop
violate-action drop
On the ES port gi1/1/2 we do have attached the policy map
ROUTING(config-if)#do show policy-map int gi1/1/2
GigabitEthernet1/1/2
Service-policy output: V4
Class-map: VLAN4 (match-all)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: vlan 4
Class-map: class-default (match-any)
17351684 packets, 1110537047 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: any
And a class map
ROUTING#show class-map VLAN4
Class Map match-all VLAN4 (id 5)
Match vlan 4
We have start a download from the server to the station but the policy is not applied, no traffic match the class-map, however the interface is in this vlan
We are unable to apply to the ES interface a class-map other the a MATCH VLAN, the MATCH IP or MATCH interface are not authorized and and error message is displayed when we try !
Our need:
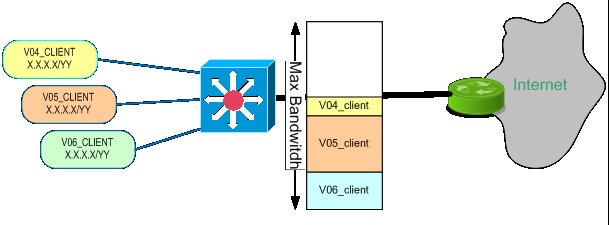
We are trying to setup the QOS on a Cisco 3750 for controlling the bandwidth usage of a set of customer. The 3750 is connected to an ISP through the egress port at 1 Gbps. The Fast Ethernet port provide access to a set of VLANs with and IP subnet.
We are seeking for a configuration example where we can classify the traffic for each customers (either by IP subnet range, VLAN or port) and assign to this classified traffic QOS rules that provide a committed information rate on the egress port.
ROUTING#sho vers
Cisco IOS Software, C3750ME Software (C3750ME-I5K91-M), Version 12.2(55)SE, RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2010 by Cisco Systems, Inc.
Compiled Sat 07-Aug-10 23:56 by prod_rel_team
Image text-base: 0x00003000, data-base: 0x02154800
ROM: Bootstrap program is C3750 boot loader
BOOTLDR: C3750ME Boot Loader (C3750ME-HBOOT-M) Version 12.1(14r)AX, RELEASE SOFTWARE (fc1)
ROUTING uptime is 3 days, 21 hours, 21 minutes
System returned to ROM by power-on
System image file is "flash:c3750me-i5k91-mz.122-55.SE/c3750me-i5k91-mz.122-55.SE.bin"
- Labels:
-
Metro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-23-2010 03:19 AM
Hi Ludovic,
QoS on ES port is different than Por Asic Qos as it is handled by the NP.
That leads that first of all we need to check how you configured your Gi1/1/2; I assume it is a L2 trunk (or access port...).
Can you send me the entire running config of your Metro switch?
Also, did you check if the same config works on the Non ES controlled Giga ports (Gi1/0/1 and Gi1/0/2)?
Regards,
Riccardo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-24-2010 01:33 AM
Hello,
Find here the 3750 configuration :
Best regards
Ludovic
Building configuration...
Current configuration : 10885 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
service password-encryption
!
hostname ROUTING
!
boot-start-marker
boot-end-marker
!
enable secret ####PRIVATE####
!
username swadmin privilege 15 password 7 ####PRIVATE####
username swadminsec privilege 15 password 7 ####PRIVATE####
!
!
no aaa new-model
clock timezone UTC 1
clock summer-time UTC recurring last Sun Mar 2:00 last Sun Oct 3:00
system mtu routing 1500
ip routing
!
!
no ip domain-lookup
vtp mode transparent
!
no mpls traffic-eng auto-bw timers frequency 0
!
!
!
spanning-tree mode rapid-pvst
spanning-tree loopguard default
spanning-tree extend system-id
spanning-tree vlan 1-4094 priority 4096
!
!
!
errdisable recovery cause link-flap
errdisable recovery interval 60
!
vlan internal allocation policy ascending
!
vlan 4
name V04_CLIENT
!
vlan 5
name V05_CLIENT
!
vlan 6
name V06_CLIENT
!
vlan 7
name V07_CLIENT
!
vlan 8
name V08_CLIENT
!
vlan 9
name V09_CLIENT
!
vlan 10
name V10_CLIENT
!
vlan 11
name V11_CLIENT
!
vlan 12
name V12_CLIENT
!
vlan 13
name V13_CLIENT
!
vlan 14
name V14_CLIENT
!
vlan 15
name V15_CLIENT
!
vlan 16
name V16_CLIENT
!
vlan 17
name V17_CLIENT
!
vlan 18
name V18_CLIENT
!
vlan 19
name V19_CLIENT
!
vlan 20
name V20_CLIENT
!
vlan 21
name V21_CLIENT
!
vlan 22
name V22_CLIENT
!
vlan 23
name V23_CLIENT
!
vlan 24
name V24_CLIENT
!
vlan 198
name V198_GIGALIS
!
vlan 199
name V199_HITS
!
vlan 200
name V200_HITS
!
!
!
!
interface FastEthernet1/0/1
description RESERVE_MGMT
switchport access vlan 200
switchport mode access
switchport nonegotiate
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/2
description ####PRIVATE####
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 199,200
switchport mode trunk
switchport nonegotiate
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast trunk
!
interface FastEthernet1/0/3
description ####PRIVATE####
switchport access vlan 199
switchport mode access
switchport nonegotiate
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/4
description ####PRIVATE####
switchport access vlan 4
switchport mode access
switchport nonegotiate
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/5
description ####PRIVATE####
switchport access vlan 5
switchport mode access
switchport nonegotiate
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/6
description ####PRIVATE####
switchport access vlan 6
switchport mode access
switchport nonegotiate
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/7
description ####PRIVATE####
switchport access vlan 7
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/8
description ####PRIVATE####
switchport access vlan 8
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/9
description ####PRIVATE####
switchport access vlan 9
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/10
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/11
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/12
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/13
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/14
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/15
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/16
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/17
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/18
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/19
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/20
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/21
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/22
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/23
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface FastEthernet1/0/24
speed 100
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface GigabitEthernet1/0/1
shutdown
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface GigabitEthernet1/0/2
shutdown
no cdp enable
no cdp tlv server-location
no cdp tlv app
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface GigabitEthernet1/1/1
shutdown
!
interface GigabitEthernet1/1/2
description ####PRIVATE####
switchport access vlan 198
speed auto 1000
spanning-tree portfast
spanning-tree bpdufilter enable
!
interface Vlan1
no ip address
no clns route-cache
!
interface Vlan4
description V04_CLIENT
ip address ####PRIVATE#### 255.255.255.248
no clns route-cache
!
interface Vlan5
description V05_CLIENT
no ip address
no clns route-cache
!
interface Vlan6
description V06_CLIENT
ip address ####PRIVATE####3 255.255.255.240
no clns route-cache
!
interface Vlan7
description V07_CLIENT
ip address ####PRIVATE#### 255.255.255.252 secondary
ip address ####PRIVATE#### 255.255.255.248
no clns route-cache
!
interface Vlan8
description V08_CLIENT
ip address ####PRIVATE#### 255.255.255.240
no clns route-cache
!
interface Vlan9
description V09_CLIENT
ip address ####PRIVATE#### 255.255.255.240
no clns route-cache
!
interface Vlan10
description V10_CLIENT
no ip address
no clns route-cache
!
interface Vlan11
description V11_CLIENT
no ip address
no clns route-cache
!
interface Vlan12
description V12_CLIENT
no ip address
no clns route-cache
!
interface Vlan13
description V13_CLIENT
no ip address
no clns route-cache
!
interface Vlan14
description V14_CLIENT
no ip address
no clns route-cache
!
interface Vlan15
description V15_CLIENT
no ip address
no clns route-cache
!
interface Vlan16
description V16_CLIENT
no ip address
no clns route-cache
!
interface Vlan17
description V17_CLIENT
no ip address
no clns route-cache
!
interface Vlan18
description V18_CLIENT
no ip address
no clns route-cache
!
interface Vlan19
description V19_CLIENT
no ip address
no clns route-cache
!
interface Vlan20
description V20_CLIENT
no ip address
no clns route-cache
!
interface Vlan21
description V21_CLIENT
no ip address
no clns route-cache
!
interface Vlan22
description V22_CLIENT
no ip address
no clns route-cache
!
interface Vlan23
description V23_CLIENT
no ip address
no clns route-cache
!
interface Vlan24
description V24_CLIENT
no ip address
no clns route-cache
!
interface Vlan198
description ####PRIVATE####
ip address ####PRIVATE#### 255.255.255.248
no clns route-cache
!
interface Vlan199
description ####PRIVATE####
ip address ####PRIVATE#### 255.255.255.248
no clns route-cache
!
interface Vlan200
description MANAGEMENT
ip address 10.200.1.1 255.255.255.0
ip access-group 100 in
no clns route-cache
!
ip default-gateway 10.200.1.254
ip classless
ip route 0.0.0.0 0.0.0.0 ####PRIVATE####
ip route 10.99.0.0 255.255.0.0 10.200.1.254
!
no ip http server
no ip http secure-server
!
!
ip sla enable reaction-alerts
access-list 60 permit 10.99.0.0 0.0.255.255
access-list 60 permit 10.200.1.0 0.0.0.255
access-list 70 permit 10.99.99.33
access-list 70 permit 10.200.1.10
access-list 100 permit ip 10.99.0.0 0.0.255.255 10.200.1.0 0.0.0.255
access-list 100 permit ip 10.200.1.0 0.0.0.255 10.200.1.0 0.0.0.255
access-list 100 deny ip any 10.200.1.0 0.0.0.255
no cdp advertise-v2
no cdp run
!
snmp-server community ####PRIVATE#### RO 70
snmp-server host 10.200.1.10 ####PRIVATE####
snmp-server host 10.99.99.33 ####PRIVATE####
banner exec ^CC
You're now connected to $(hostname).
Use of this system constitutes your consent to monitoring.
^C
banner motd ^CC
NOTICE TO USERS
=============================================================================
This is an official computer system and is the property of the ORGANIZATION.
It is for authorized users only. Unauthorized users are prohibited. Users
(authorized or unauthorized) have no explicit or implicit expectation of
privacy. Any or all uses of this system may be subject to one or more of the
following actions: interception, monitoring, recording, auditing, inspection
and disclosing to security personnel and law enforcement personnel, as well
as authorized officials of other agencies, both domestic and foreign. By
using this system, the user consents to these actions. Unauthorized or
improper use of this system may result in administrative disciplinary action
and civil and criminal penalties. By accessing this system you indicate your
awareness of and consent to these terms and conditions of use. Discontinue
access immediately if you do not agree to the conditions stated in this
notice.
=============================================================================
^C
!
line con 0
line vty 0 4
access-class 60 in
login local
line vty 5 15
access-class 60 in
login local
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-25-2010 02:22 AM
Ludovic,
2 remarks about your configuration
1. mls qos is not enabled. ( since you are applying qos on ES ports in this case you don't need mls qos but you should enable anyway when you use qos)
2. both ingress port fa1/0/4 and egress gi1/1/2 are access ports meaning that the actual frames have no .1q tag. That implies that match vlan cannot work as there is no vlan id to match (it matches the actual .1q tag if present).
For your configuration to work you need to configure gi1/1/2 as a trunk port carrying the actual tags. If you cannot do that as the station is directly attached to gi1/1/2 and does not understand tags you cannot match the vlan.
Anyway I don't think your station is directly connected to gi1/1/2 as IMHO it is not good idea "wasting" and ES port and use it as an access (moreover due to the speed mismatch you risk to see lots of drops on fa1/0/4 if the station sends burtsy traffic back to your server).
Finally have you checked the qos config guide of the me3750?
regards,
Riccardo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2010 03:14 AM
Thank a lots for your response.
I go to make some new tests, to see that.
I wish you an Happy new year !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2010 05:19 AM
Thanks a lot Riccardo, i really appreciate your input.
The configuration I sent is a testing configuration, we have another 3750
that is installed and working (without bandwidth management, that is the
point).
In the lab we do not connect the egress port to a provider, but in the real
configuration the port is of course connected to our ISP.
The link between the 3750 and the ISP is not VLAN enable and will not be.
The bandwidth management that we want to do is on the link between the 3750
and the ISP but based on the source vlan that is attached to the physical
fa1/0/4.
I thought that the drawing was self explanatory, sorry. In the future we
will have many customers, each of them having a different VLAN and IP
subnet. They will add their servers in their own VLAN but we want to be able
to control their bandwidth usage of the egress port gi1/1/2.
To check that bandwidth control is working we voluntary put a workstation
attached to the egress port and the server in its VLAN (port fa). In the
future the client will be located on internet and connect through the ISP
link (egress port) connection and the 3750 up to the servers of our customer
connected to the fa ports.
From your explanation, I should understand that the bandwidth limitation can
be applied only to a VLAN that is present as .1q tag between the 3750 and
the other remote device at the ISP location. We do not and can't do that
with our ISP.
Our need is very simple we want to limit the bandwidth use on the egress
port used by each of our customers. It doesn't matter how we select their
traffic, can be by port , by vlan or by ip subnet.
Up to now nor example nor simple config is available for doing that. I have
read the manual and many more without finding this simple example.
I really doubt about the feasibility with a 3750.
DO you think that there is a way to do that with a 3750, in other case we
will try to find another solution.
It is a shame because the device is a metro device and sold as a device with
bandwidth management features.
Kind regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2010 10:21 AM
Hi Ludovic,
I see your point.
You wrote:
"In the future we
will have many customers, each of them having a different VLAN and IP
subnet. They will add their servers in their own VLAN but we want to be able
to control their bandwidth usage of the egress port gi1/1/2."
That leads that in future implementation your Gi1/1/2 will either be a L2 trunk or a L3 port.
If you go for the L2 trunk you will have the .1q tag on the frames leaving the switch going to the ISP. In this case you might use the match vlan statement and apply the output policing to the ES port.
If (as I assume from your words when you say that no .1q tag will never be sent to the ISP) the ES port will be a L3 port you need to find a different way to police your traffic as the Hierarchical QoS model which is used on ES ports has some requirements and limitations (no match ACL and so on) which renders it not suitable for your needs.
You could do instead:
1. police the traffic in ingress on physical port fa1/0/4 (if multiple ports will belong to the same vlan you might aslo use an aggregate policer)
2. Don't use the ES port to connect to your ISP but use the non ES ports which do not have the same limitations of the ES ones.
regards,
Riccardo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2011 02:28 AM
Hi Riccardo
Thanks a lot for your last input, We get at least some results and can now control the maximum bandwidth use by our customers on the FA ports. Right now we can limit the outgoing traffic on the FA port with the srr-queue bandwidth limit interface command. As we have one port per customer we are able to define bandwidth limitation on the traffic coming from Internet and going to each customer’s vlan.
We would like to control the other way, So if you have working example of how to set the configuration for having a bandwidth limitation of the output traffic (Giga ports) it would be great. AS I mention before, I can use either the ES port or non ES Giga port. If I can do what I need with the non ES port that is fine.
The connection to the ISP is a simple single Ethernet link with no tag no trunking. In this connection to the ISP I have of course all the traffic of all my customers. My need is quite simple, I want to restrict the outgoing traffic bandwidth (policing) based either on source port (FA) ip subnet or vlan. I should be able to give for example to customer1 20 Mbps, to customer2 10 Mbps, to customer3 50 Mbps toward Internet of the Giga speed link with my ISP.
Is it possible with the 3750 ? You say that I should use non ES port, I imagine that I should first classify the traffic on the ingress port (fa) and police them on the egress port (giga). What commands should I use on the egress portto police the traffic and give a bandwidth limitation. The documentation is not clear with that need. I see that bandwidth can be limited on a queue, but I could have 20 customers and have only 4queues !
I you can give me a way of doing that I will not have to search for another type of device to solve my need. Which one in the Cisco product can solve it?
Thank you so much for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2011 09:42 AM
Hi Ludovic,
sorry but i still don't understand your future deployment.
If you will have multiple vlans that need to be policed the port towards the ISP must be either a trunk or a L3 port (do you routing towards your ISP). This part is still not clear.
If it will be a trunk you can use the same configuration you attached at the beginning of your thread, where you have a service policy on the ES port matching the vlan.
The qos guide has an exmplae for that "
Configuring a Hierarchical Two-Rate Traffic Policer"
Riccardo
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide