- Cisco Community
- Technology and Support
- Service Providers
- MPLS
- IOS XR Rewrite Not Working | Migration from XE Issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2023 01:44 PM
Hi Community,
I am seeing some issues when attempting to migrate some l2vpn circuits from IOS XE to IOS XR.
The layout is as follows:
(INT VLAN 1) ---- [IOS CPE 3650 CX] ---- (int gi0/1/1, service instance 1 ethernet encapsulation dot1q untagged) [IOS XE PE, ASR 900] ----> l2 mpls virtual circuit <---- [IOS XR P, ASR 9006] ---- (INT BUNDLE 2.5 dotq 5 rewrite ingress tag pop 1 symmetric) [IOS XR EDGE, ASR 9006] --- (INT BUNDLE 10.5 dot1q 5 )
My l2vpn / mpls pseudowire is established (showing up on both the 9006 and 900 transport routers) but the layer 2 is not establishing. I see the following error messages on my CPE when it establishes:
Feb 17 20:21:32.245: %SPANTREE-2-RECV_PVID_ERR: Received BPDU with inconsistent peer vlan id 5 on GigabitEthernet1/0/8 VLAN1.
Feb 17 20:21:32.245: %SPANTREE-2-BLOCK_PVID_PEER: Blocking GigabitEthernet1/0/8 on VLAN0005. Inconsistent peer vlan.
Feb 17 20:21:32.245: %SPANTREE-2-BLOCK_PVID_LOCAL: Blocking GigabitEthernet1/0/8 on VLAN0001. Inconsistent local vlan.
Feb 17 20:21:32.248: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to down
It as if the rewrite to untagged is not taking effect properly on the transport IOS XR router and it is still sending the VLAN 5 to the CPE router.
If I use this same setup, but instead use an IOS XE router for the P router, I do not have the errors, and I can establish layer 2 back to the edge router.
Solved! Go to Solution.
- Labels:
-
MPLS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 05:03 AM
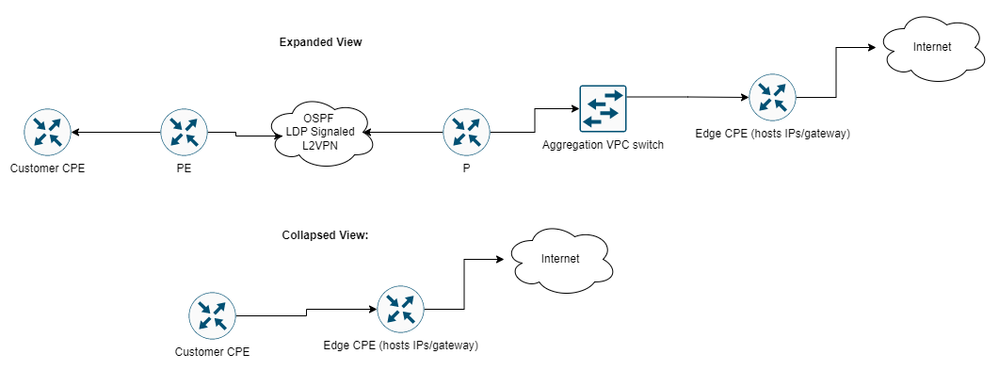
I see - the attempt to tunnel between endpoint, to endpoint STP.
I think the issue may be partly due to the placement of the switch that helps to aggregate our links facing the edge CPE. See this diagram that shows the traffic. I did not include that switch in the initial writeup, but it is actually between the P and the edge CPE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2023 11:33 AM
Hi @diefierr
Here is another update. I tried moving this to a VFI/bridge-domain setup instead of a p2p xconnect. So it was in a bridge-group with just one member.
The port didn't go down and the member didn't flap, but the MAC was not learned still.
I did see this MAC addressed learned in the bridge-group on the PE router, which appears to be the Nexus VPC that is in front of the edge router.
0026.f008.0000
https://www.cisco.com/c/en/us/support/docs/switches/nexus-7000-series-switches/211494-Use-of-Source-MAC-Address-Field-in-Spann.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2023 10:28 AM
|
rewrite ingress tag translate 1-to-1 dot1q <othersideTag> symmetric |
try this solution, you can only change the tag
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2023 10:54 AM
Thanks for the help! This is still sending the VLAN 119 even when rewritten to VLAN 1 on the P router.
And, the ASR 900 won't perform this option, and complains it is not a logically valid operation on the EFP. It seems that it is a limitation with the RP for it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 07:22 AM
Hi,
as @diefierr has already mentioned, according the log messages you have an issue with the STP protocol. IOS and IOS XR behave differently when transporting STP BPDUs over pseudowires.
Please check the following document for more information
To prevent your issue you have to block STP BPDUs either on CE devices, or on the ASR9K router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 07:32 AM
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 09:04 AM - edited 03-09-2023 09:05 AM
You have two options
- block the BPDUs on the Nexus VPC switch using BPDU filter
or
- block BPDUs on the P router using ethernet-services ACL
I would prefer the second option. In both cases the filtering applies on all BPDUs, you can not filter out single VLAN BPDUs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 09:19 AM
Thanks @filopeter @diefierr @MHM Cisco World for your help. I will give these options a try and come back the post with my results.
I appreciate your time!
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide