Hi,
I am working with the following topology:
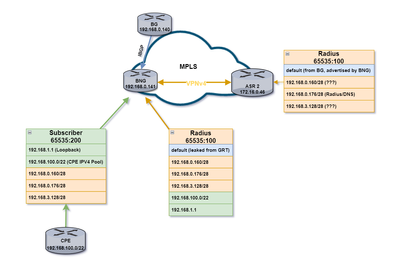
I have an ASR9k router (BNG in the topology) that has 2 VRF configured: Subscriber and Radius. The goal is to have the VRF subscriber able to reach a DNS server that is located behind ASR 02.
I receive all the networks and through leaking I am able to achieve this, the issue begins when I try to apply an import route policy to the Radius vrf to "clean up" the routing table and only import what is needed.
Without a policy, this is the routing table for the Radius VRF (routes in bold are the ones I am looking to filter):
B* 0.0.0.0/0 [200/0] via 192.168.0.140 (nexthop in vrf default), 00:00:04
L 172.16.128.103/32 is directly connected, 18:43:17, Loopback1
B 172.16.182.0/30 is directly connected, 00:00:04, Bundle-Ether5.99 (nexthop in vrf Subscriber)
B 192.168.0.160/28 [200/0] via 172.16.0.46 (nexthop in vrf default), 19:33:13
B 192.168.0.176/28 [200/0] via 172.16.0.46 (nexthop in vrf default), 19:33:13
B 192.168.1.1/32 is directly connected, 00:00:04, Loopback123 (nexthop in vrf Subscriber)
B 192.168.3.128/28 [200/0] via 172.16.0.46 (nexthop in vrf default), 19:33:13
B 192.168.100.0/22 is directly connected, 00:00:04, Null0 (nexthop in vrf Subscriber) |
This is the routing table on the Subscriber VRF:
B* 0.0.0.0/0 [20/0] via 172.16.182.2, 21:12:36
B 172.16.128.103/32 is directly connected, 00:04:22, Loopback1 (nexthop in vrf Radius)
C 172.16.182.0/30 is directly connected, 21:12:40, Bundle-Ether5.99
L 172.16.182.1/32 is directly connected, 21:12:40, Bundle-Ether5.99
B 192.168.0.160/28 [200/0] via 172.16.0.46 (nexthop in vrf default), 19:37:32
B 192.168.0.176/28 [200/0] via 172.16.0.46 (nexthop in vrf default), 19:37:32
L 192.168.1.1/32 is directly connected, 1d17h, Loopback123
B 192.168.3.128/28 [200/0] via 172.16.0.46 (nexthop in vrf default), 19:37:32
S 192.168.100.0/22 is directly connected, 01:34:07, Null0
A 192.168.100.5/32 is directly connected, 02:08:51, PW-Ether1.1000.pppoe483 |
I then created a route policy to filter out unwanted routes:
route-policy ImportRadius
if destination in (192.168.0.160/28, 192.168.0.176/28, 192.168.3.128/28, 192.168.100.0/22, 192.168.1.1/32) then
pass
else
drop
endif
end-policy |
And applied it under the VRF Radius configuration:
|
vrf Radius_DNS
rd 65535:100
address-family ipv4 unicast
import route-policy ImportRadius_DNS
import from default-vrf route-policy DEFAULT advertise-as-vpn <-imports default route from GRT
import route-target
65535:200
65535:100
!
export to default-vrf route-policy RDA allow-imported-vpn <- this leaks the radius networks to the GRT
export route-target
65535:100
|
While this succeeds in filtering out the unwanted routes from the VRF table, as soon as this policy is applied I do lose the ability to reach the networks in the Radius VRF from the subscriber VRF and I cannot figure out why. Could anyone advise?
Thank you