- Cisco Community
- Technology and Support
- Service Providers
- MPLS
- NAT is not working for VRF partially
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2013 07:00 AM
Hello!
I have a diagram like this:
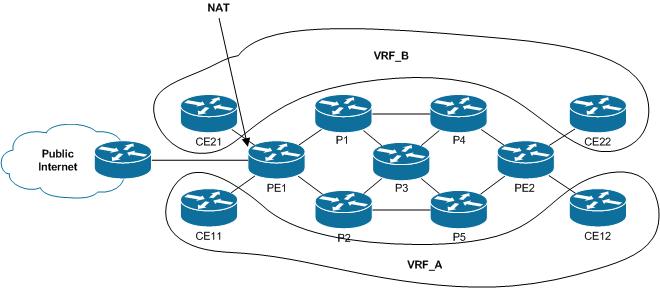
VRF_A and VRF_B have overlapping addressing plans from series 192.168.x.x.
As routing protocol in both of VRFs adopted RIP (I tried all, but effect much the same).
The closest to PE1 network is 172.16.0.0/24.
PE1:
ip vrf VRF_A
rd 65001:1
route-target export 65001:1
route-target import 65001:1
ip vrf VRF_B
rd 65001:2
route-target export 65001:2
route-target import 65001:2
ip nat inside source list 10 interface FastEthernet0/0 vrf VRF_A overload
ip nat inside source list 10 interface FastEthernet0/0 vrf VRF_B overload
ip route vrf VRF_A 0.0.0.0 0.0.0.0 FastEthernet0/0 172.16.0.1 global
ip route vrf VRF_B 0.0.0.0 0.0.0.0 FastEthernet0/0 172.16.0.1 global
interface FastEthernet0/0
ip address 172.16.0.24 255.255.255.0
ip nat outside
duplex full
interface FastEthernet1/0
ip vrf forwarding VRF_A
ip address 192.168.0.2 255.255.255.0
ip nat inside
duplex full
interface FastEthernet4/0
ip vrf forwarding VRF_B
ip address 192.168.0.2 255.255.255.0
ip nat inside
duplex full
When I try ti ping 172.16.0.1 from CE11, CE21 and from VRF_A and VRF_B on PE1 - all if fine! NAT is performed and ping is OK.
But when I tried to ping from others (PE2 and CE21 and CE22) NAT is not performed, I see 192.168.x.x at Internet Router and ping is failled.
I'm in stupor. What could it be??? And how to avoid this situation? Are there "exits"?
I forgot to mention that there is a full connectivity inside both of VRFs. Routing protocols and redistribution work fine.
Kind regard,
Ellad
Solved! Go to Solution.
- Labels:
-
MPLS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 04:01 AM
Hello,
Where do you see "mpls ip" on FastEthernet1/0 and FastEthernet4/0 (connect CE11 and CE21 to PE2). :-) When I see 192.168.x.x on Internet I am sure (more or less) that problem is with NAT. :-) I agree. I didn't configure "ip nat inside" on P-PE interfaces. It was done on PE-CE interfaces. These are absolutely different interfaces.
I did not say that you are missing mpls ip on interfaces on Fa1/0 and Fa4/0, it would by useless. You wrote that NAT is not working if you try ping from PE2, CE12, CE22. Also you wrote that you did not configure ip nat inside on P-PE interfaces. Do it!
PE1
interface toward P1
ip nat inside
interface toward P2
ip nat inside
Best Regards
Please rate all helpful posts and close solved questions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 01:39 AM
Hello Ellad,
I see 192.168.x.x at Internet Router and ping is failled.
So routing will be probably OK, ICMPs reach destination but with private source IP address so REPLY can not be delivered.
I think problem will be with NAT on PE1. Did you configure "ip nat inside" on PE1 interface toward P routers? Also can you post configuration of ACL 10?
Problem could be also with configuration ip nat inside and mpls ip on same interface, I had problems with this on some platforms.
Best Regards
Please rate all helpful posts and close solved questions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 02:34 AM
Hello!
Where do you see "mpls ip" on FastEthernet1/0 and FastEthernet4/0 (connect CE11 and CE21 to PE2). :-) When I see 192.168.x.x on Internet I am sure (more or less) that problem is with NAT. :-) I agree. I didn't configure "ip nat inside" on P-PE interfaces. It was done on PE-CE interfaces. These are absolutely different interfaces.
Sure, here is ACL10:
access-list 10 permit 192.168.0.0 0.0.255.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 02:46 AM
I even tried to add more specific rules in ACL10 like 192.168.1.0 0.0.0.255 and so on, but it didn't help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 04:01 AM
Hello,
Where do you see "mpls ip" on FastEthernet1/0 and FastEthernet4/0 (connect CE11 and CE21 to PE2). :-) When I see 192.168.x.x on Internet I am sure (more or less) that problem is with NAT. :-) I agree. I didn't configure "ip nat inside" on P-PE interfaces. It was done on PE-CE interfaces. These are absolutely different interfaces.
I did not say that you are missing mpls ip on interfaces on Fa1/0 and Fa4/0, it would by useless. You wrote that NAT is not working if you try ping from PE2, CE12, CE22. Also you wrote that you did not configure ip nat inside on P-PE interfaces. Do it!
PE1
interface toward P1
ip nat inside
interface toward P2
ip nat inside
Best Regards
Please rate all helpful posts and close solved questions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 04:13 AM
It's wrong:
PE1
interface toward P1
ip nat inside
interface toward P2
ip nat inside
Here is PE1:
1.0.5.1 is Loopback0 of P3. It's a route-reflector for all PEs. I study.Current configuration : 2829 bytes
!
version 12.3
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname PE1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
ip subnet-zero
!
!
!
ip vrf VRF_A
rd 65001:1
route-target export 65001:1
route-target import 65001:1
!
ip vrf VRF_B
rd 65001:2
route-target export 65001:2
route-target import 65001:2
!
ip cef
ip audit po max-events 100
mpls label protocol ldp
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback0
ip address 10.0.2.1 255.255.255.255
!
interface FastEthernet0/0
ip address 172.16.0.24 255.255.255.0
ip nat outside
duplex full
!
interface FastEthernet1/0
ip vrf forwarding VRF_A
ip address 192.168.0.2 255.255.255.0
ip nat inside
duplex full
!
interface FastEthernet2/0
ip address 10.0.23.1 255.255.255.0
duplex full
tag-switching mtu 1512
tag-switching ip
!
interface FastEthernet3/0
ip address 10.0.24.1 255.255.255.0
duplex full
tag-switching mtu 1512
tag-switching ip
!
interface FastEthernet4/0
ip vrf forwarding VRF_B
ip address 192.168.0.2 255.255.255.0
ip nat inside
duplex full
!
router ospf 1
log-adjacency-changes
network 10.0.0.0 0.255.255.255 area 0
!
router rip
version 2
no auto-summary
!
address-family ipv4 vrf VRF_B
redistribute bgp 65001 metric 1
network 192.168.0.0
no auto-summary
exit-address-family
!
router bgp 65001
no bgp default ipv4-unicast
bgp log-neighbor-changes
neighbor 10.0.5.1 remote-as 65001
neighbor 10.0.5.1 update-source Loopback0
!
address-family vpnv4
neighbor 10.0.5.1 activate
neighbor 10.0.5.1 next-hop-self
neighbor 10.0.5.1 send-community both
exit-address-family
!
address-family ipv4 vrf VRF_B
redistribute static
redistribute rip
no auto-summary
no synchronization
exit-address-family
!
address-family ipv4 vrf VRF_A
no auto-summary
no synchronization
exit-address-family
!
ip nat inside source list 10 interface FastEthernet0/0 vrf VRF_A overload
ip nat inside source list 10 interface FastEthernet0/0 vrf VRF_B overload
ip classless
ip route vrf VRF_A 0.0.0.0 0.0.0.0 FastEthernet0/0 172.16.0.1 global
ip route vrf VRF_B 0.0.0.0 0.0.0.0 FastEthernet0/0 172.16.0.1 global
no ip http server
no ip http secure-server
!
ip extcommunity-list 1 permit soo 65002:901
!
access-list 1 deny 10.1.8.1
access-list 1 deny 10.0.8.1
access-list 1 deny 10.1.2.1
access-list 1 deny 10.0.2.1
access-list 1 permit any
access-list 10 permit 192.168.0.0 0.0.255.255
access-list 10 permit 192.168.1.0 0.0.0.255
!
route-map rm-soo permit 10
set extcommunity soo 65002:901
!
route-map rm-soo-action deny 10
match extcommunity 1
!
route-map rm-soo-action permit 20
match ip address 1
!
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 144 0
logging synchronous
stopbits 1
line aux 0
stopbits 1
line vty 0 4
login
!
!
end
And all what you see above - Dynamipses. Internet router - real Ubuntu server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 04:18 AM
But...
I helps!!! :-) Why? Could you explain?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 05:22 AM
Traffic from PE2, CE12 and CE22 destinated to internet is received on one of these interfaces (interfaces toward P routers). On receiving interfaces you need to configure ip nat inside, outgoing interface need to be configured with ip nat outside and also traffic has to match ACL 10. Every condition was fulfiled except configuration of ip nat inside on receiving interface.
http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080094831.shtml
Best Regards
Please rate all helpful posts and close solved questions
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide