- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: “5411 Supplicant stopped responding to ISE". Use EAP-TLS for authentication method and the root...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 07:56 PM - edited 05-17-2020 11:55 PM
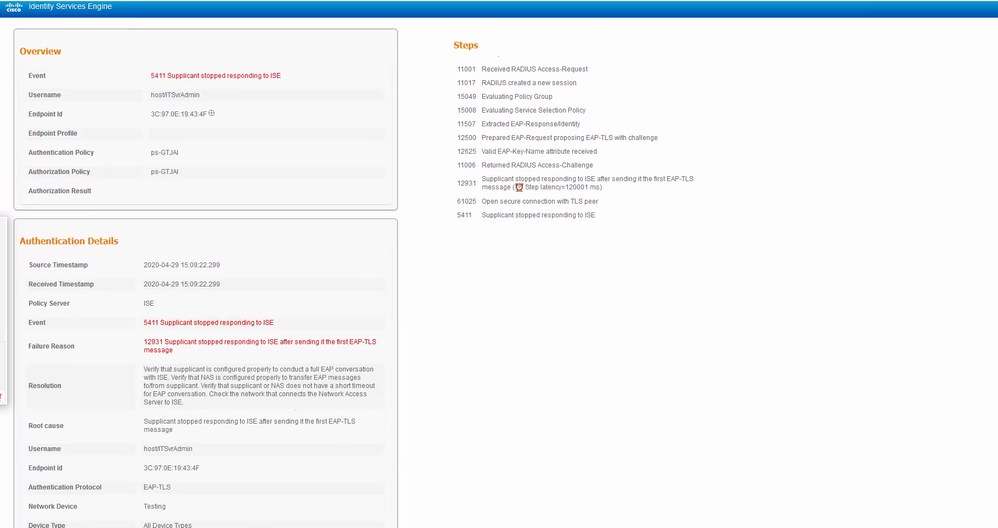
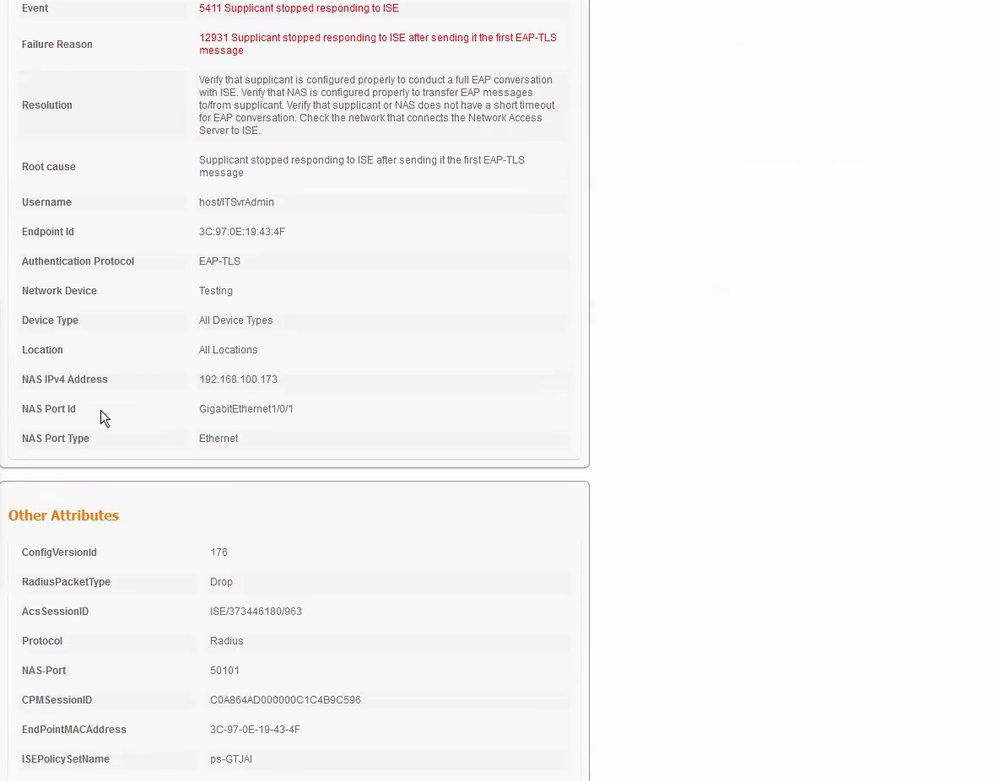
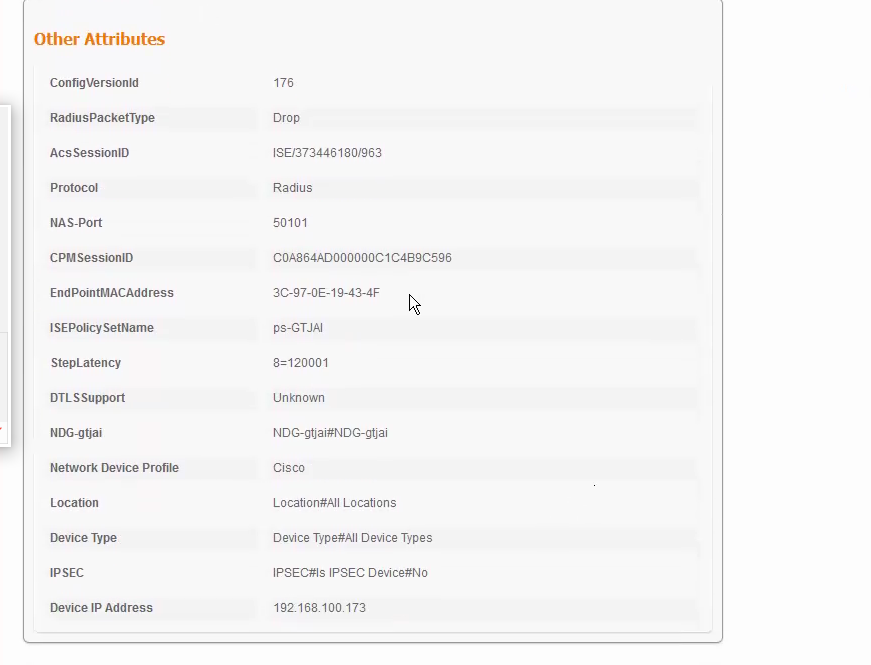
The background is the end devices PC would like to use EAP-TLS for authentication method and the root CA is window CA.
However the ISE live log show “5411 Supplicant stopped responding to ISE”.
Below as the ISE live log.
Switch config:
aaa group server radius gp-ISE
server name ISE
!
aaa group server tacacs+ group-ts-ISE
server name ts-ISE
!
aaa authentication login default group group-ts-ISE local
aaa authentication enable default group group-ts-ISE enable
aaa authentication dot1x default group gp-ISE
aaa authorization exec default group group-ts-ISE local
aaa authorization commands 0 default group group-ts-ISE local
aaa authorization commands 1 default group group-ts-ISE local
aaa authorization network default group gp-ISE
aaa accounting auth-proxy default start-stop group gp-ISE
aaa accounting dot1x default start-stop group gp-ISE
aaa accounting exec default start-stop group group-ts-ISE
aaa accounting commands 0 default stop-only group group-ts-ISE
aaa accounting commands 1 default stop-only group group-ts-ISE
aaa accounting commands 15 default start-stop group group-ts-ISE
!
aaa server radius dynamic-author
client 192.168.100.240 server-key 7 xxxxxxxxxxxxxxxxxxx
server-key 7 xxxxxxxxxxxxxxxxx
!
aaa session-id common
!
dot1x system-auth-control
dot1x critical eapol
errdisable recovery cause bpduguard
errdisable recovery cause loopback
errdisable recovery interval 180
license boot level ipservicesk9
diagnostic bootup level minimal
!
interface GigabitEthernet1/0/1
switchport access vlan 100
switchport mode access
ip arp inspection limit rate 100
authentication event fail action next-method
authentication open
authentication order dot1x
authentication priority dot1x
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
ip radius source-interface Vlan100
ip sla enable reaction-alerts
logging history size 50
logging history debugging
logging origin-id ip
logging facility local2
logging source-interface Vlan100
logging host 192.168.100.240
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
!
radius server ISE
address ipv4 192.168.100.240 auth-port 1645 acct-port 1646
key 7 xxxxxxxxxxxxxxxx
!
!
Any hits for this issues?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 08:45 PM
See a similar community post here
This is typically an issue with the client supplicant and/or certificate trust chain.
I've also seen this issue caused by fragmentation due to an MTU mismatch somewhere between the switch and PSN. If your switch MTU is set to jumbo, try setting it to 1500 and testing again. See the document EAP Fragmentation Implementations and Behavior for more info.
You might also want to do a packet capture on the client to see the full EAP conversation and open a TAC case if all else fails.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 08:52 PM
Basic checks
It appears that your supplicant is performing Machine Authentication - is it configured for certificate authentication (or user authentication), and does your machine have a machine certificate?
if the above is all good (i.e. you r supplicant is configured for Machine Auth and you have a machine cert) then:
In your ISE Wired 802.1X Policy Set Overall Condition, did you include "Allow Protocols EAP-TLS"?
If your Windows Clients are using TLS 1.0 or TLS 1.1, did you allow this under Admin > System > Settings Security Settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2021 12:12 PM - edited 03-10-2021 12:14 PM
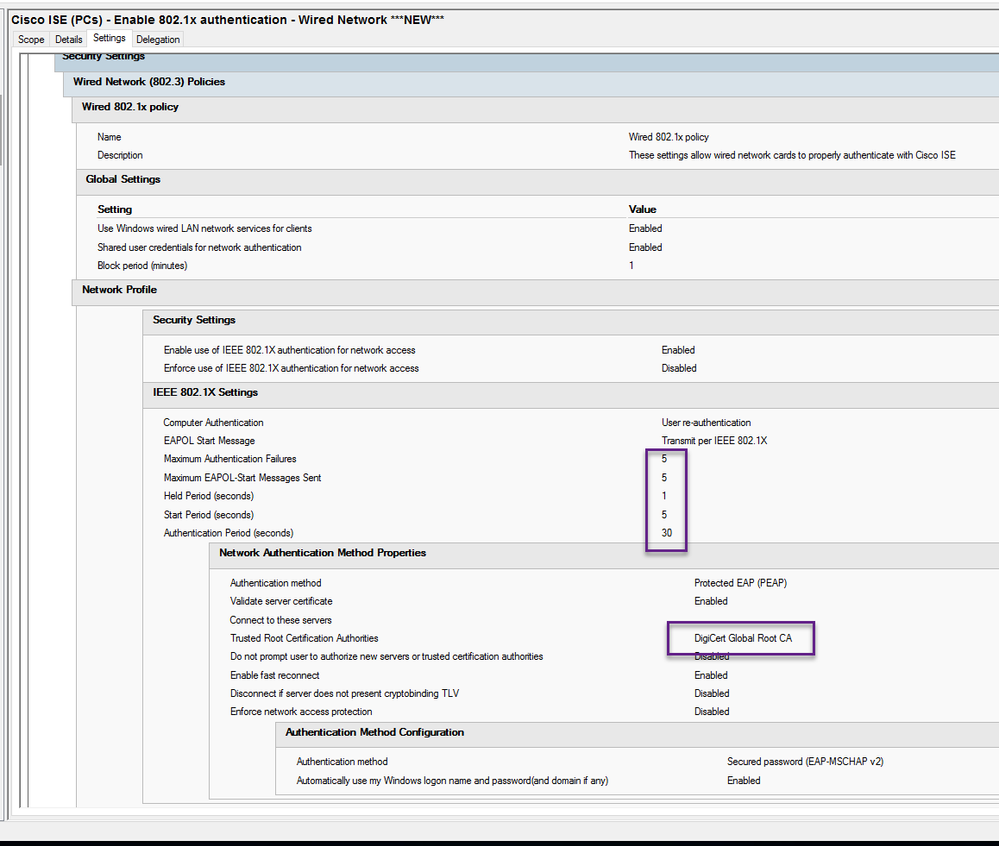
ISE teammates,
Ok, so after months of working on this issue with "Supplicant Stopped Responding..." errors, I've determined that by updating the Wired AutoConfig GPO we use to include these settings, we got the endpoints connected and authorized as expected. Out of the box Windows 10 tries once to connect to a Cisco switch via PEAP before giving up and waiting 20 minutes. Here's the GPO settings we're using. We opted for public CA certs because I was tired of fooling around with our internal CA.
Hope it helps someone,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 08:45 PM
See a similar community post here
This is typically an issue with the client supplicant and/or certificate trust chain.
I've also seen this issue caused by fragmentation due to an MTU mismatch somewhere between the switch and PSN. If your switch MTU is set to jumbo, try setting it to 1500 and testing again. See the document EAP Fragmentation Implementations and Behavior for more info.
You might also want to do a packet capture on the client to see the full EAP conversation and open a TAC case if all else fails.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 08:52 PM
Basic checks
It appears that your supplicant is performing Machine Authentication - is it configured for certificate authentication (or user authentication), and does your machine have a machine certificate?
if the above is all good (i.e. you r supplicant is configured for Machine Auth and you have a machine cert) then:
In your ISE Wired 802.1X Policy Set Overall Condition, did you include "Allow Protocols EAP-TLS"?
If your Windows Clients are using TLS 1.0 or TLS 1.1, did you allow this under Admin > System > Settings Security Settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2020 11:47 PM - edited 05-17-2020 11:59 PM
"Allow Protocols EAP-TLS" already enabled in Policy Set in ISE.
And the client cert. and root cert. already imported to client PC.
"certificate authentication (or user authentication)"already configure at network adapter of client PC.
Added partial config. of the switch relayed to authenticate configuration. is it possible it caused by switch configuration issues?
Switch config:
aaa group server radius gp-ISE
server name ISE
!
aaa group server tacacs+ group-ts-ISE
server name ts-ISE
!
aaa authentication login default group group-ts-ISE local
aaa authentication enable default group group-ts-ISE enable
aaa authentication dot1x default group gp-ISE
aaa authorization exec default group group-ts-ISE local
aaa authorization commands 0 default group group-ts-ISE local
aaa authorization commands 1 default group group-ts-ISE local
aaa authorization network default group gp-ISE
aaa accounting auth-proxy default start-stop group gp-ISE
aaa accounting dot1x default start-stop group gp-ISE
aaa accounting exec default start-stop group group-ts-ISE
aaa accounting commands 0 default stop-only group group-ts-ISE
aaa accounting commands 1 default stop-only group group-ts-ISE
aaa accounting commands 15 default start-stop group group-ts-ISE
!
aaa server radius dynamic-author
client 192.168.100.240 server-key 7 xxxxxxxxxxxxxxxxxxx
server-key 7 xxxxxxxxxxxxxxxxx
!
aaa session-id common
!
dot1x system-auth-control
dot1x critical eapol
errdisable recovery cause bpduguard
errdisable recovery cause loopback
errdisable recovery interval 180
license boot level ipservicesk9
diagnostic bootup level minimal
!
interface GigabitEthernet1/0/1
switchport access vlan 100
switchport mode access
ip arp inspection limit rate 100
authentication event fail action next-method
authentication open
authentication order dot1x
authentication priority dot1x
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
ip radius source-interface Vlan100
ip sla enable reaction-alerts
logging history size 50
logging history debugging
logging origin-id ip
logging facility local2
logging source-interface Vlan100
logging host 192.168.100.240
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
!
radius server ISE
address ipv4 192.168.100.240 auth-port 1645 acct-port 1646
key 7 xxxxxxxxxxxxxxxx
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2022 02:40 AM
Is it possible that if the clinet MAC address deleted from WLC and user faces this issue "5411 Supplication issue"? or because of DHCP leases overlapping ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 06:58 PM
Hi All,
Finally, it is working fine with the cert. signed by window Standalone CA, but it is not working for windows enterprise ca.
Any requirement or specific setting needed in ISE to compatible to windows enterprise ca.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2021 12:12 PM - edited 03-10-2021 12:14 PM
ISE teammates,
Ok, so after months of working on this issue with "Supplicant Stopped Responding..." errors, I've determined that by updating the Wired AutoConfig GPO we use to include these settings, we got the endpoints connected and authorized as expected. Out of the box Windows 10 tries once to connect to a Cisco switch via PEAP before giving up and waiting 20 minutes. Here's the GPO settings we're using. We opted for public CA certs because I was tired of fooling around with our internal CA.
Hope it helps someone,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2021 10:11 PM
It indeed helped me. Thank you for sharing. Appreciate it.
Regards,
Omid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2021 06:35 AM
against the wall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2024 04:19 PM - edited 12-11-2024 04:25 PM
Our Cisco 3850 switch was on 16.09.06. After months of fight to configure EAP-TLS, I upgraded the switch to 16.12.12 today. EAP-TLS just worked without a peep of a complaint. It was highly frustrating journey totally unnecessary and a company like Cisco which produce ISE, Switch, WLC should produce complete validated design and remove all wasted time from these monstrosity. For what it does, ISE infrastructure is too complicated. Well 802.1x Ecosystem and its various actors.. Most organizations just want their own device to connect and there are far easier way to accomplish than pile of mess I had to dig through. Validated Design, Validated configuration which should include all Version numbers in involved should be doable in 30 page doc. If not these don't deserve to exist. Now it is done it is a cinch but journey was too costly. I enjoy reading but I can count some 3000 pages to get here and that was ones I skim through and I have not touched others on the subject..
This article was written in 2020 when 16.09.06 is published. I am here from future 16.12.12 a 2024 release will likely fix your issue. My 5411 no longer appears in the log.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2024 04:38 PM
I share your sentiment on suffering simple/stupid bugs for a technology that has been around for a very long time. But you mentioned that there are "far easier way(s) to accomplish ..." - what do you propose as the alternative?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2024 04:48 PM
Simplified Canned Deployment.
what would you like to do today?
I would like a peap on vlan 10 using v10_user/password. Please authorize anyone with that credential and assign them vlan10.
What more would you like to today?
I would like a eap-tls with this CA Key and anyone presenting any Key issued from that CA let them connect.
My organization will likely use 20 some peaps and 1 Cert(Maybe 2-3 more if I end up doing BYOD type).
Hi, there is a device with 12:34:56:78:90:12 trying to connect what would you like to do? You can authorize, or put them in vLAN bucket or reject.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide