- Cisco Community
- Technology and Support
- Security
- Network Access Control
- 802.1x and Dynamic VLAN deployment for Cisco ISE and Meraki Access Points
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 03:10 AM - edited 06-21-2021 03:11 AM
Hi all,
We’ve deployed Cisco ISE in our DC and we planned to control 802.1x wireless access from branch sites. We’ve already configured VPN tunnel between DC and Branches. We would like to configure Dynamic VLAN assignment to the client PCs on branch sites, i.e., we’ve only one SSID and users from different user groups will be assigned to different VLAN when connected to Wi-Fi.
As we are using Meraki Wireless APs on branch sites, it is possible to use dynamic VLAN assignment feature with Cisco ISE?
As for now, we already configure dynamic VLAN feature in our environment, but some endpoints did not get IP assigned although it passed authentication and authorization.
Thank You!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2021 10:51 PM
Looking for “Per User VLAN Tagging”
https://documentation.meraki.com/MR/Client_Addressing_and_Bridging/VLAN_Tagging
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 04:30 AM
I do not believe this solution works, since you have only 1 SSID, that is associated with VLAN aleady.
But with ISE profiling, based on the user Group you can setup the Security profile, what user / end device can access the resources.
As for now, we already configure dynamic VLAN feature in our environment, but some endpoints did not get IP assigned although it passed authentication and authorization.
is this wired or wireless ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2021 06:28 AM
Dynamic VLAN feature is supported with Cisco WLC right? But with Cisco Meraki , it cannot be work ?
But right now only some endpoints can't get IP address while most endpoints are working Ok. And there is no VLAN tagging enable for SSID at this moment.
We planned to enable 802.1x only for Wireless network.
If this is not a proper solution , we'll deploy with different SSID then.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2021 10:38 PM
Have you tried Group Policy with Filter ID or Airespace ACL?
Depends on your AuthZ conditions, you probably can assign different Group Policies to different AuthZ Profiles, each has different Group Policy associated with different VLAN ID.
Here are the docs for your reference. https://documentation.meraki.com/MR/Group_Policies_and_Block_Lists/Using_RADIUS_Attributes_to_Apply_Group_Policies
Basically you create the several Group Policies with different VLANs on Meraki Dashboard, then creat corresponding AuthZ Profiles on ISE which call the names of the Group Policies.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2021 10:51 PM
Looking for “Per User VLAN Tagging”
https://documentation.meraki.com/MR/Client_Addressing_and_Bridging/VLAN_Tagging
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2021 05:04 PM
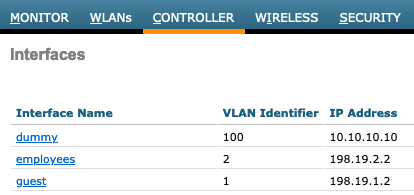
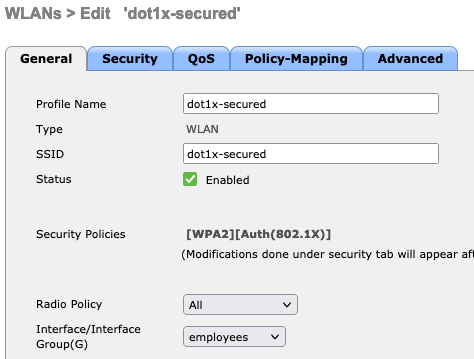
Typically your WLAN SSID is associated with a specific VLAN, regardless of the wireless product.
Cisco AireOS WLC with a specific Interface Group mapping to a VLAN:
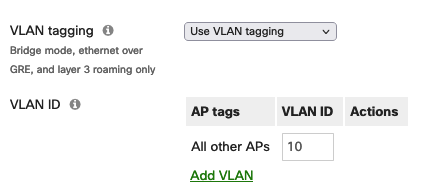
And in Meraki APs for a given SSID:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide