- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ACS 5.2 - Identity Group as Authorization Condition is not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-23-2010
06:01 AM
- last edited on
03-25-2019
05:27 PM
by
ciscomoderator
![]()
Hello,
I trying use "Identity Groups" as "Compound Condition" in My "Access Policy" Authorization rule: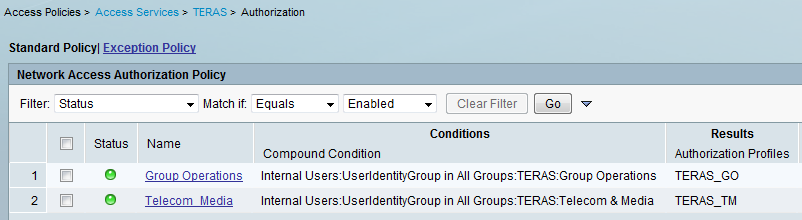 .
.
Result is simple Radius Class attribute which should be passed to SSL VPN gateway (picture is modified to be smaller):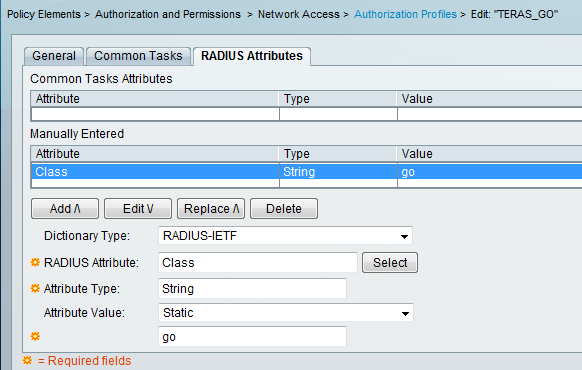
Every user in my Radius database has assigned any Identity Group which should identify him like member of some Business Unit (we are used it in this way with ACS 4.x - user database and Groups was migrated to ACS 5.2 from it).
Unfortunately these authorization rules are not working as expected. If I will for testing purposes bypass one rule with Operator "not in" instead of "in" this rule is used and matching Authorization Profile from Result is used.
So, it looks like Compound condition can't match itself with Identity Group correctly - Is it any known / unknown BUG or I am missed something in my configuration? I am a newbie to the ACS 5.2 so is possible that I am forgot something.
Thanks for any help with this strange issue.
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2010 05:58 AM
Please confirm that the access service identity policy is using the internal data for authentication
In order to see the full details/steps for the request go to:
-Launch Monitoring & Report Viewer
- Select Authentications - RADIUS - Today
- When you see the record for your failing request press the icon under the heading details and you will see all the processing for the request
The Authentication Details is the most relevant section
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-24-2010 12:08 AM
Hi
You don't need to use any "Compound conditions". You need to use "Identity Group" condition. The next example show you how to enable the "Identitiy Group" condition.
After that, edit your rules, uncheck "Compound" condition, check "Identity group" and choose the value desired.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2010 12:22 AM
Hello, Thank you for tip, this is little bit simplest way how to do it, but unfortunately situation is still the same - rule is still not working. It looks like another bug
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2010 06:14 AM
I am tried another thing. I am created new Dictionary entry (System Administration --> Configuration --> Dictionaries --> Identity --> Internal Users), type Enum with two items (ID=1, Value=Groups Operations; ID=2, Value=Telecom & Media), and in user profile choose "Group Operations" from new menu.
I am changed Authorization rules to match this new condition only, but still it is not working. Something is terribly wrong and I don't have any idea what I can try next
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2010 07:18 AM
Could you please post your new config with "Identity Groups". Also you can go to "Monitoring and Report" to see the logs and see what's ACS doing exactly when matching your rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2010 12:57 AM
All pictures are modified to save space.
My testing user account:

Identity Groups:

Identity Attribute:

Authorization Policy - Test 1 - match Itentity Group:

Authorization Policy - Test 2 - match Identity Atribute:

Log mesage:

Unfortunately I can't find logs where is logged rules matching process - do you have any guide?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2010 05:58 AM
Please confirm that the access service identity policy is using the internal data for authentication
In order to see the full details/steps for the request go to:
-Launch Monitoring & Report Viewer
- Select Authentications - RADIUS - Today
- When you see the record for your failing request press the icon under the heading details and you will see all the processing for the request
The Authentication Details is the most relevant section
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2010 07:58 AM
It was accurate shot. I am using RSA Authentication Manager for authentication and it look that ACS expecting attributes from RSA instead of ACS. So I am created new Identity rule where is used RSA for authentication and additional attributes are taken from Internal Users storage. Now it is working well. Thank you very much.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide