- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Anyconnect NAM disconnect network during auth
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 05:23 AM
Hi,
we use EAP-TLS for machine and user auth. When certificates are installed, everything is fine. I am testing the scenario when the e.g. User certificate is not present. Anyconnect shows the warning that there is no certificate (dot1x fails) but network connection is still active on the device (auth open is configured with permit any ACL on the interface). The connection timeout session starts the countdown and after this period anyconnect tries to auth again. The problem is that during this reauth the network is cut. What to set in order to prevent this network disconnect?
thank you
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
-
Wired
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2021 05:27 AM - edited 03-01-2021 05:29 AM
Totally understand. NAM can be tricky because as soon as it is installed it overrides the built-in Windows network management, which is actually why Cisco recommends to hide the Windows network icon to aide in eliminating user confusion. IMO you have several options for proper client staging & onboarding. You could setup a parking lot of some sort that devices without NAM are authorized to via mab (keeping ports closed auth which means less overhead & time for you). The kicker with that would be having MACs in a local ISE endpoint group, which could be a good thing for client tracking purposes. Then within that parking lot give clients access to your PKI, & whatever necessary resources are needed to properly stage itself for proper 8021x onboarding. Then per user or ISE authz profile have devices reauth every so often so that they eventually once setup properly will use 8021x and onboard to their full respective networks. Lastly, It really depends on your requirements. Good luck & HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 06:26 AM - edited 02-28-2021 06:26 AM
Do you have a fallback mechanism enabled and in place to kick in once 8021x fails like perhaps mab? I am not sure what your config looks like, but the two commands below will determine 8021x timeout & failover. Essentially at link up, the NAD sends an eap-request frame. The NAD will wait for a period of time before sending another eap-request which is determined by timeout tx-period & the number of times it resends the eap-request is defined by max-reauth-req. The commands are as follows:
#dot1x timeout tx-period
#dot1x max-reauth-req
The timeout formula for 8021x to fail is this:
Timeout = (max-reauth-req +1) * tx-period
NAM does have a configuration setup that allows data traffic via port authentication exception policy.
From Cisco docs:
Port Authentication Exception Policy Pane
This pane appears only for wired networks.
The Port Authentication Exception Policy pane enables you to tailor the IEEE 802.1X supplicant’s behavior during the authentication process. If port exceptions are not enabled, the supplicant continues its existing behavior and opens the port only upon successfully completing the full configuration (or as described earlier in this section, after the maxStarts number of authentications are initiated without a response from the authenticator). Choose from one of the following options:
-
Allow data traffic before authentication—Allows data traffic prior to an authentication attempt.
-
Allow data traffic after authentication even if:
-
EAP fails—When selected, the supplicant attempts authentication. If authentication fails, the supplicant allows data traffic despite the authentication failure.
-
EAP succeeds but key management fails—When selected, the supplicant attempts to negotiate keys with the key server but allows data traffic if the key negotiation fails for any reason. This setting is valid only when key management is configured. If key management is set to none, the check box is dimmed out.
-
Good luck & HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 07:22 AM
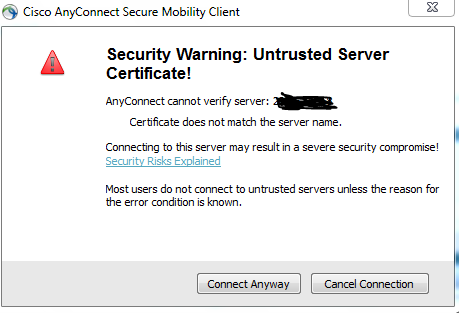
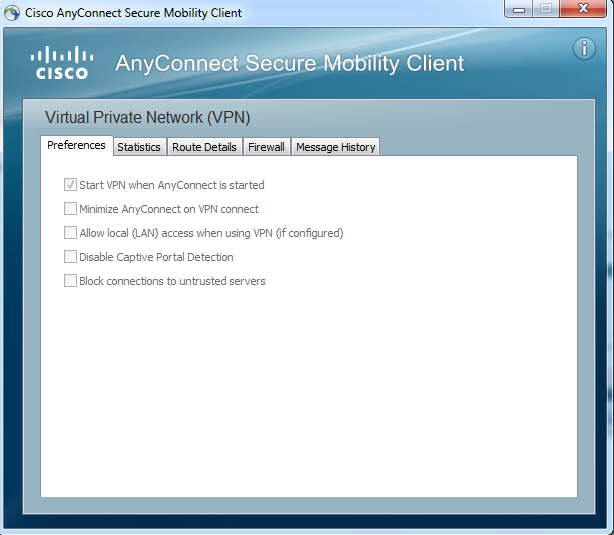
Thank you for communicating with the Cisco community, validate that the error communication is not activated and in the anyconnect configuration that you have allowed the servers below, it sends you a screen of how it should be
this is done on the client side.
Remember to rate this answer as this motivates you to continue contributing in the community
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 09:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 10:52 AM
So the NAM 'Connection Timeout' configures the number of seconds that the NAM module will wait for a network connection to establish before it attempts to connect to another network so that is not the problem in this scenario. Note that by default, before successful authentication the identity of a client/user is unknown so all traffic is blocked when using 8021x. Only EAPOL traffic is allowed to negotiate onboarding. Hence why you see the drops during fallover authentication transitions after you remove <authentication open>. There are however different 8021x modes. If you wish to allow certain traffic pre-auth & even after failed auth you may want to research low impact mode. Take a look into testing the NAM port exceptions as well that I mentioned earlier.
Lastly, here are some good links that dive in deeper:
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 01:03 PM
Hi Mike,
the reason why I try to find out why the outage happens is because of the roll-out phase on all interfaces. Anyconnect+certificates will be already installed on PCs so when I configure the interface everything should be fine. I am trying to simulate the cases when xml, certificates or NAM wont be present on the device and what it means to end users from their point (network outage, etc). My plan is to configure interfaces in 2 steps - 1st: authentication open, control direction both and ACL - permit ip any any. When auth is successful then I will configure the port with closed mode - it is 2nd step. But if there is a problem I wont configure the 2nd step and client should not be affected. But right now the client is affected.
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2021 05:27 AM - edited 03-01-2021 05:29 AM
Totally understand. NAM can be tricky because as soon as it is installed it overrides the built-in Windows network management, which is actually why Cisco recommends to hide the Windows network icon to aide in eliminating user confusion. IMO you have several options for proper client staging & onboarding. You could setup a parking lot of some sort that devices without NAM are authorized to via mab (keeping ports closed auth which means less overhead & time for you). The kicker with that would be having MACs in a local ISE endpoint group, which could be a good thing for client tracking purposes. Then within that parking lot give clients access to your PKI, & whatever necessary resources are needed to properly stage itself for proper 8021x onboarding. Then per user or ISE authz profile have devices reauth every so often so that they eventually once setup properly will use 8021x and onboard to their full respective networks. Lastly, It really depends on your requirements. Good luck & HTH!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide