- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: %AUTHMGR-5-SECURITY_VIOLATION, %AUTHMGR-5-MACREPLACE, %AUTHMGR-5-F
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 12:31 AM
Hello, We run an estate of mostly 9200L and some 3850 switches, with MAB, we also use Cisco ISE 3.1.
Our Switch logs are filling up with the following 3 errors,
%AUTHMGR-5-SECURITY_VIOLATION,
%AUTHMGR-5-MACREPLACE,
%AUTHMGR-5-FAIL
This is an example of one of the switches config, and logs:-
Mar 28 08:24:38: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/12, new MAC address (0800.0fc0.dece) is seen.AuditSessionID 0AF420D700006BB22D7A658E
Mar 28 08:24:38: %AUTHMGR-5-MACREPLACE: MAC address (0800.0fc0.dece) on Interface GigabitEthernet1/0/12 is replaced by MAC (0800.0fc0.dece) AuditSessionID 0AF420D700006BB22D7A658E
Mar 28 08:24:38: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/18, new MAC address (b00c.d158.a0b9) is seen.AuditSessionID 0AF420D700006BB32D7A65CA
Mar 28 08:24:38: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a0b9) on Interface GigabitEthernet2/0/18 is replaced by MAC (b00c.d158.a0b9) AuditSessionID 0AF420D700006BB32D7A65CA
Mar 28 08:24:38: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (0800.0fc0.dece) on Interface Gi1/0/12 AuditSessionID 0AF420D700006BB22D7A658E
Mar 28 08:24:38: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a0b9) on Interface Gi2/0/18 AuditSessionID 0AF420D700006BB32D7A65CA
Mar 28 08:24:38: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/41, new MAC address (b00c.d158.a4f3) is seen.AuditSessionID 0AF420D700006BB42D7A66CE
Mar 28 08:24:38: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a4f3) on Interface GigabitEthernet2/0/41 is replaced by MAC (b00c.d158.a4f3) AuditSessionID 0AF420D700006BB42D7A66CE
Mar 28 08:24:38: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a4f3) on Interface Gi2/0/41 AuditSessionID 0AF420D700006BB42D7A66CE
Mar 28 08:24:38: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/36, new MAC address (b00c.d158.a4c9) is seen.AuditSessionID 0AF420D700006BB52D7A682C
Mar 28 08:24:38: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a4c9) on Interface GigabitEthernet1/0/36 is replaced by MAC (b00c.d158.a4c9) AuditSessionID 0AF420D700006BB52D7A682C
Mar 28 08:24:38: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a4c9) on Interface Gi1/0/36 AuditSessionID 0AF420D700006BB52D7A682C
Mar 28 08:24:38: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/41, new MAC address (b00c.d158.a4f3) is seen.AuditSessionID 0AF420D700006BB62D7A6836
Mar 28 08:24:38: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a4f3) on Interface GigabitEthernet2/0/41 is replaced by MAC (b00c.d158.a4f3) AuditSessionID 0AF420D700006BB62D7A6836
interface GigabitEthernet2/0/41
switchport access vlan 139
switchport mode access
switchport voice vlan 505
no logging event link-status
no logging event power-inline-status
authentication event fail action next-method
authentication host-mode multi-domain
authentication open
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation replace
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
no snmp trap link-status
dot1x pae authenticator
dot1x timeout tx-period 10
auto qos trust dscp
spanning-tree portfast
service-policy input AutoQos-4.0-Trust-Dscp-Input-Policy
service-policy output AutoQos-4.0-Output-Policy
authentication mac move permit is enabled globally
The mac address 0800.0fc0.dece is a mitel phone, and it is authenticated in ISE
The messages are prolific and fill up the logs, so can make genuine troubleshooting difficult.
What is actually happening? Can the messages be stopped?
Thank you.
Den,
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 06:00 AM
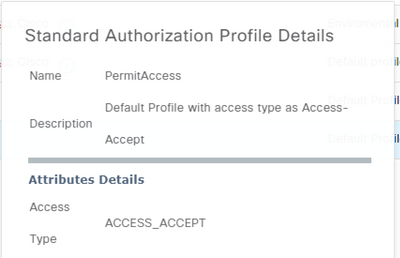
Thank you Octavian, this is really interesting, we do have a unique profile in ISE for Maintel Phones/VC units, but it hits the generic 'Permit Access' Authorisation profile.
Should the phones have their own Authorisation profile? I can see the Default Cisco IP phone authorisation profile, but we don't use it as we don't have any cisco phones onsite, I can see that it has a DACL, and Cisco AV pair info, is this what could be missing from my 'generic' IP phone profile?
"Access Type = ACCESS_ACCEPT
DACL = PERMIT_ALL_IPV4_TRAFFIC
cisco-av-pair = device-traffic-class=voice"
Can I just add, that we do not have any issues with IP phones working onsite with the current config.
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 06:11 AM - edited 03-28-2023 06:11 AM
Hi,
A 'normal' IP Phone uses the Voice VLAN.
The thing is that when you have 802.1x enabled, the switch will not let any MAC/session into the voice VLAN until it recevies from RADIUS the fact that it should belong to voice VLAN.
This translates to that "cisco-av-pair = device-traffic-class=voice" from ISE which is actually the check box voice vlan permissions when you look into the authorization profile from GUI.
You don't neccesarilly need that defualt cisco ip phone profile. You can create a simple profile, with no dACL, but remeber to check voice vlan permissions.
In your case, you don't have any issue because you have the authentication open command configured. If authentication/authorization fails, no one gets access denied.
BR,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 07:12 AM
Octavian, Digging a bit deeper, I can see what you mean, we do have an non cisco IP phone auth profile, it is there, but its not been used, this could be an oversight from when ISE3.1 was setup, and because the phones 'worked' it was never checked. From memory I do remember the setting from our old installation of ISE (hence why the 'non cisco phone' auth pro is there). It is an easy enough change, although, we have approx ALOT of phones on mab, so caution would be sensible :). I am curious to know if this would also bring the repeat counter down in ISE. It always seem astonishingly high at 5284758!!
Thanks you for your advice. I will let you know the outcome
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 04:03 AM
Apologies for the late reply, as it wasn't causing us too much pain, it wasn't high priority. However I have now changed the authorisation profile to "non cisco IP phone", which uses the following text:-
"Access Type = ACCESS_ACCEPT
DACL = PERMIT_ALL_IPV4_TRAFFIC
cisco-av-pair = device-traffic-class=voice"
I can confirm that the switch logs are no longer filling up, and we also noticed CPU utilisation dropping on all 4 Cisco ISE boxes.
The change did not cause any outage to the IP phones.
Thanks again for all your help and advice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 12:47 AM
Here are some possible reasons for these logs:
1. Devices on the network might be transmitting more than one MAC address from the same interface, causing the security violation and MAC replacement messages.
2. There might be a MAC address spoofing or an issue with devices trying to use the same MAC address.
3. Devices could be roaming across multiple switch ports. This is more common with phones and wireless access points connected to multiple switches.
To address these issues, you can try the following steps:
1. Verify if the devices are causing the security violations and see if there's any configuration or issue that leads to multiple MAC addresses being transmitted from a single interface. If so, fix the issue on the devices itself.
2. In case MAC address spoofing is identified, consider implementing enhanced security measures like IP Source Guard or Dynamic ARP Inspection to protect against such attacks.
3. If devices are roaming across multiple switch ports, consider implementing Sticky MAC or port security to allow known MAC addresses to move between ports without causing security violations.
However, if you determine that these logs don't pose an actual security threat and want to stop these messages from flooding the logs, you can adjust the logging levels on the switches using the following command:
```Cisco
logging level authmgr 4
```
This command sets the logging level for the authentication manager to "warnings" (level 4), which will exclude the messages related to security violations, MAC replacement, and failed authorizations.
Keep in mind that adjusting the logging level might hide genuine security threats or issues within your network. It is essential to perform proper analysis and troubleshooting before making changes to the logging level.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 04:34 AM
authentication mac-move permit <<- add this command and check again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 04:46 AM
Hi, yup, command is definitely there:-
switch 1 provision ws-c3850-48p
switch 2 provision ws-c3850-48p
authentication mac-move permit <<<
We are also using authentication host-mode multi-domain, as most Switch ports have a phone(mitel) and a PC attached
Devices don't move about, they sit on a desk, customers don't move kit.
This is happening on all switches, across multiple sites with the MAB config, so doubt it would be a spoofing event.
You can see how 'chatty' it is below:-
Mar 28 12:41:16: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (842a.fd52.02a4) on Interface Gi1/0/16 AuditSessionID 0AF420D7000167562E655A62
Mar 28 12:41:16: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a0b9) on Interface Gi2/0/18 AuditSessionID 0AF420D7000167572E655A6C
Mar 28 12:41:17: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/20, new MAC address (040e.3c94.380a) is seen.AuditSessionID 0AF420D7000167582E655CCE
Mar 28 12:41:17: %AUTHMGR-5-MACREPLACE: MAC address (040e.3c94.380a) on Interface GigabitEthernet2/0/20 is replaced by MAC (040e.3c94.380a) AuditSessionID 0AF420D7000167582E655CCE
Mar 28 12:41:17: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (040e.3c94.380a) on Interface Gi2/0/20 AuditSessionID 0AF420D7000167582E655CCE
Mar 28 12:41:17: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/16, new MAC address (842a.fd52.02a4) is seen.AuditSessionID 0AF420D7000167592E655ED6
Mar 28 12:41:17: %AUTHMGR-5-MACREPLACE: MAC address (842a.fd52.02a4) on Interface GigabitEthernet1/0/16 is replaced by MAC (842a.fd52.02a4) AuditSessionID 0AF420D7000167592E655ED6
Mar 28 12:41:17: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (842a.fd52.02a4) on Interface Gi1/0/16 AuditSessionID 0AF420D7000167592E655ED6
Mar 28 12:41:17: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/26, new MAC address (b00c.d158.a38d) is seen.AuditSessionID 0AF420D70001675A2E655EFE
Mar 28 12:41:17: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a38d) on Interface GigabitEthernet2/0/26 is replaced by MAC (b00c.d158.a38d) AuditSessionID 0AF420D70001675A2E655EFE
Mar 28 12:41:17: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a38d) on Interface Gi2/0/26 AuditSessionID 0AF420D70001675A2E655EFE
Mar 28 12:41:17: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/16, new MAC address (842a.fd52.02a4) is seen.AuditSessionID 0AF420D70001675B2E655F26
Mar 28 12:41:17: %AUTHMGR-5-MACREPLACE: MAC address (842a.fd52.02a4) on Interface GigabitEthernet1/0/16 is replaced by MAC (842a.fd52.02a4) AuditSessionID 0AF420D70001675B2E655F26
Mar 28 12:41:17: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (842a.fd52.02a4) on Interface Gi1/0/16 AuditSessionID 0AF420D70001675B2E655F26
Mar 28 12:41:18: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/26, new MAC address (b00c.d158.a38d) is seen.AuditSessionID 0AF420D70001675C2E6560DE
Mar 28 12:41:18: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a38d) on Interface GigabitEthernet2/0/26 is replaced by MAC (b00c.d158.a38d) AuditSessionID 0AF420D70001675C2E6560DE
Mar 28 12:41:18: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a38d) on Interface Gi2/0/26 AuditSessionID 0AF420D70001675C2E6560DE
Mar 28 12:41:18: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/36, new MAC address (0800.0fc0.c243) is seen.AuditSessionID 0AF420D70001675D2E6560DE
Mar 28 12:41:18: %AUTHMGR-5-MACREPLACE: MAC address (0800.0fc0.c243) on Interface GigabitEthernet1/0/36 is replaced by MAC (0800.0fc0.c243) AuditSessionID 0AF420D70001675D2E6560DE
Mar 28 12:41:18: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/16, new MAC address (842a.fd52.02a4) is seen.AuditSessionID 0AF420D70001675E2E6560E8
Mar 28 12:41:18: %AUTHMGR-5-MACREPLACE: MAC address (842a.fd52.02a4) on Interface GigabitEthernet1/0/16 is replaced by MAC (842a.fd52.02a4) AuditSessionID 0AF420D70001675E2E6560E8
Mar 28 12:41:18: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (0800.0fc0.c243) on Interface Gi1/0/36 AuditSessionID 0AF420D70001675D2E6560DE
Mar 28 12:41:18: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (842a.fd52.02a4) on Interface Gi1/0/16 AuditSessionID 0AF420D70001675E2E6560E8
Mar 28 12:41:19: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/45, new MAC address (b00c.d158.a27c) is seen.AuditSessionID 0AF420D70001675F2E6562F0
Mar 28 12:41:19: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a27c) on Interface GigabitEthernet2/0/45 is replaced by MAC (b00c.d158.a27c) AuditSessionID 0AF420D70001675F2E6562F0
Mar 28 12:41:19: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a27c) on Interface Gi2/0/45 AuditSessionID 0AF420D70001675F2E6562F0
Mar 28 12:41:19: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/16, new MAC address (842a.fd52.02a4) is seen.AuditSessionID 0AF420D7000167602E656598
Mar 28 12:41:19: %AUTHMGR-5-MACREPLACE: MAC address (842a.fd52.02a4) on Interface GigabitEthernet1/0/16 is replaced by MAC (842a.fd52.02a4) AuditSessionID 0AF420D7000167602E656598
Mar 28 12:41:19: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (842a.fd52.02a4) on Interface Gi1/0/16 AuditSessionID 0AF420D7000167602E656598
Mar 28 12:41:19: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/12, new MAC address (0800.0fc0.dece) is seen.AuditSessionID 0AF420D7000167622E65676E
Mar 28 12:41:19: %AUTHMGR-5-MACREPLACE: MAC address (0800.0fc0.dece) on Interface GigabitEthernet1/0/12 is replaced by MAC (0800.0fc0.dece) AuditSessionID 0AF420D7000167622E65676E
Mar 28 12:41:19: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (0800.0fc0.dece) on Interface Gi1/0/12 AuditSessionID 0AF420D7000167622E65676E
Mar 28 12:41:19: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/20, new MAC address (0800.0fc0.ddda) is seen.AuditSessionID 0AF420D7000167612E65676E
Mar 28 12:41:19: %AUTHMGR-5-MACREPLACE: MAC address (0800.0fc0.ddda) on Interface GigabitEthernet1/0/20 is replaced by MAC (0800.0fc0.ddda) AuditSessionID 0AF420D7000167612E65676E
Mar 28 12:41:19: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/20, new MAC address (040e.3c94.380a) is seen.AuditSessionID 0AF420D7000167632E65676E
Mar 28 12:41:19: %AUTHMGR-5-MACREPLACE: MAC address (040e.3c94.380a) on Interface GigabitEthernet2/0/20 is replaced by MAC (040e.3c94.380a) AuditSessionID 0AF420D7000167632E65676E
Mar 28 12:41:19: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/39, new MAC address (b00c.d158.a0b6) is seen.AuditSessionID 0AF420D7000167642E65676E
Mar 28 12:41:19: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a0b6) on Interface GigabitEthernet1/0/39 is replaced by MAC (b00c.d158.a0b6) AuditSessionID 0AF420D7000167642E65676E
Mar 28 12:41:19: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (0800.0fc0.ddda) on Interface Gi1/0/20 AuditSessionID 0AF420D7000167612E65676E
Mar 28 12:41:19: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (040e.3c94.380a) on Interface Gi2/0/20 AuditSessionID 0AF420D7000167632E65676E
Mar 28 12:41:19: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a0b6) on Interface Gi1/0/39 AuditSessionID 0AF420D7000167642E65676E
Mar 28 12:41:20: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/45, new MAC address (b00c.d158.a27c) is seen.AuditSessionID 0AF420D7000167652E6569B2
Mar 28 12:41:20: %AUTHMGR-5-MACREPLACE: MAC address (b00c.d158.a27c) on Interface GigabitEthernet2/0/45 is replaced by MAC (b00c.d158.a27c) AuditSessionID 0AF420D7000167652E6569B2
Mar 28 12:41:20: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (b00c.d158.a27c) on Interface Gi2/0/45 AuditSessionID 0AF420D7000167652E6569B2
Mar 28 12:41:21: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet1/0/16, new MAC address (842a.fd52.02a4) is seen.AuditSessionID 0AF420D7000167662E656B92
Mar 28 12:41:21: %AUTHMGR-5-MACREPLACE: MAC address (842a.fd52.02a4) on Interface GigabitEthernet1/0/16 is replaced by MAC (842a.fd52.02a4) AuditSessionID 0AF420D7000167662E656B92
Mar 28 12:41:21: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (842a.fd52.02a4) on Interface Gi1/0/16 AuditSessionID 0AF420D7000167662E656B92
Mar 28 12:41:21: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/31, new MAC address (f80d.ac1f.69d5) is seen.AuditSessionID 0AF420D7000167692E656BA6
Mar 28 12:41:21: %AUTHMGR-5-MACREPLACE: MAC address (f80d.ac1f.69d5) on Interface GigabitEthernet2/0/31 is replaced by MAC (f80d.ac1f.69d5) AuditSessionID 0AF420D7000167692E656BA6
Mar 28 12:41:21: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/20, new MAC address (040e.3c94.380a) is seen.AuditSessionID 0AF420D7000167672E656B92
Mar 28 12:41:21: %AUTHMGR-5-MACREPLACE: MAC address (040e.3c94.380a) on Interface GigabitEthernet2/0/20 is replaced by MAC (040e.3c94.380a) AuditSessionID 0AF420D7000167672E656B92
Mar 28 12:41:21: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/41, new MAC address (0800.0fc0.dd54) is seen.AuditSessionID 0AF420D7000167682E656B92
Mar 28 12:41:21: %AUTHMGR-5-MACREPLACE: MAC address (0800.0fc0.dd54) on Interface GigabitEthernet2/0/41 is replaced by MAC (0800.0fc0.dd54) AuditSessionID 0AF420D7000167682E656B92
Mar 28 12:41:21: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface GigabitEthernet2/0/3, new MAC address (0800.0fc0.e30e) is seen.AuditSessionID 0AF420D70001676A2E656C00
Mar 28 12:41:21: %AUTHMGR-5-MACREPLACE: MAC address (0800.0fc0.e30e) on Interface GigabitEthernet2/0/3 is replaced by MAC (0800.0fc0.e30e) AuditSessionID 0AF420D70001676A2E656C00
Mar 28 12:41:21: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (f80d.ac1f.69d5) on Interface Gi2/0/31 AuditSessionID 0AF420D7000167692E656BA6
Mar 28 12:41:21: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (040e.3c94.380a) on Interface Gi2/0/20 AuditSessionID 0AF420D7000167672E656B92
Mar 28 12:41:21: %AUTHMGR-5-FAIL: Authorization failed or unapplied for client (0800.0fc0.dd54) on Interface Gi2/0/41 AuditSessionID 0AF420D7000167682E656B92
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 05:30 AM
Hi,
I can see that your port is multi-domain and you already have mab + dot1x + access vlan + voice vlan + violation restrict, but somehow you're not authorizing the IP Phone session.
Is it possible that you don't give voice vlan permission to the mittel phone from ISE?
I'm asking you this because if the IP phone has a PC connected to it, and you don't return via authorization voice vlan permissions to your phone, then your port will ping/pong between phone and PC considering that only one MAC should be authorizated in the data VLAN and one in the voice VLAN (your config - multi-domain).
On a side note, it's normal for a switch to generate mac replace events when you're using IP phones and the reasoning is logic.
When you're first connecting your phone to the switch, the switch doesn't have any means to know from start that this is a phone.
That's why the phone's MAC will initiallybelong to the data VLAN. After ISE authenticates the phone, the same MAC will be part of the voice VLAN, but it will not be automatically deleted from the data VLAN. When PC joins in, his MAC will replace the phone MAC from data VLAN only. The same phone MAC will be safe and sound (authorized) in the voice VLAN.
Regarding those logs, if needed, you can supress them.
This is an example for the monitor session:
(config)#logging discriminator FILTER facility drops AUTHMGR|MAB|DOT1X
(config)#logging monitor discriminator FILTER
You can apply the same filter to buffer logging or any destination of your choice.
BR,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 06:00 AM
Thank you Octavian, this is really interesting, we do have a unique profile in ISE for Maintel Phones/VC units, but it hits the generic 'Permit Access' Authorisation profile.
Should the phones have their own Authorisation profile? I can see the Default Cisco IP phone authorisation profile, but we don't use it as we don't have any cisco phones onsite, I can see that it has a DACL, and Cisco AV pair info, is this what could be missing from my 'generic' IP phone profile?
"Access Type = ACCESS_ACCEPT
DACL = PERMIT_ALL_IPV4_TRAFFIC
cisco-av-pair = device-traffic-class=voice"
Can I just add, that we do not have any issues with IP phones working onsite with the current config.
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 06:11 AM - edited 03-28-2023 06:11 AM
Hi,
A 'normal' IP Phone uses the Voice VLAN.
The thing is that when you have 802.1x enabled, the switch will not let any MAC/session into the voice VLAN until it recevies from RADIUS the fact that it should belong to voice VLAN.
This translates to that "cisco-av-pair = device-traffic-class=voice" from ISE which is actually the check box voice vlan permissions when you look into the authorization profile from GUI.
You don't neccesarilly need that defualt cisco ip phone profile. You can create a simple profile, with no dACL, but remeber to check voice vlan permissions.
In your case, you don't have any issue because you have the authentication open command configured. If authentication/authorization fails, no one gets access denied.
BR,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2023 07:12 AM
Octavian, Digging a bit deeper, I can see what you mean, we do have an non cisco IP phone auth profile, it is there, but its not been used, this could be an oversight from when ISE3.1 was setup, and because the phones 'worked' it was never checked. From memory I do remember the setting from our old installation of ISE (hence why the 'non cisco phone' auth pro is there). It is an easy enough change, although, we have approx ALOT of phones on mab, so caution would be sensible :). I am curious to know if this would also bring the repeat counter down in ISE. It always seem astonishingly high at 5284758!!
Thanks you for your advice. I will let you know the outcome
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-03-2023 03:16 PM
Hi DigiDen,
In this case, the switchport learn multiple MAC addresses and as per your configuration at the switchport is as below.
"authentication host-mode multi-domain"
This issue was generated due to multi-domain. To understand this please see the below facts.
multi-host: Multiple mac addresses can be in DATA domain. Only first mac is authenticated.
multi-domain: Only 1 mac address can be in DATA domain and only 1 mac address can be in VOICE domain
multi-auth: Multiple mac addresses can be in DATA domain (all authenticated individually) and only 1 MAC address can be in Voice domain.
To resolve the issue, you should use "multi-auth" instead of "multi-domain".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 04:03 AM
Apologies for the late reply, as it wasn't causing us too much pain, it wasn't high priority. However I have now changed the authorisation profile to "non cisco IP phone", which uses the following text:-
"Access Type = ACCESS_ACCEPT
DACL = PERMIT_ALL_IPV4_TRAFFIC
cisco-av-pair = device-traffic-class=voice"
I can confirm that the switch logs are no longer filling up, and we also noticed CPU utilisation dropping on all 4 Cisco ISE boxes.
The change did not cause any outage to the IP phones.
Thanks again for all your help and advice.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide