- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Authorization profile - denied access despite successful auth
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 12:28 PM
Hello all, hoping I can get some help with a new setup here. I've been asked by administration to set up ISE with EAP chaining, in a fairly simple setup, to restrict wireless network access to domain only devices. I'm not generally a network admin so it's been a bit of a slog to get to understand ISE, but after a lot of documentation and videos, I think I have a fair understanding of it...the problem being I still can't get it to work (and neither can our network admin or the support he tried bringing in...)
I'm on ISE 2.7 (old, I know, but it's what I'm have a license for, and theoretically should work), administration doesn't want to buy Anyconnect but everyone is on up to date copies of Windows 10/11 enterprise, so TEAP should be usable.
After going through all the documentation I could find, I've set up access according to the documentation at https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/216510-eap-chaining-with-teap.pdf
And set up the wireless according to https://community.cisco.com/t5/security-knowledge-base/teap-for-windows-10-using-group-policy-and-ise-teap/ta-p/4134289
I am unable to connect to the network at all though. I'll attach the full radius log from a connection attempt since they're rather huge, but the end result of the attempt appears to be, for the machine auth part -
| 24325 | Resolving identity - BMEDLOANL15 | |
| 24313 | Search for matching accounts at join point - corp.umfmed.org | |
| 24319 | Single matching account found in forest - corp.umfmed.org | |
| 24323 | Identity resolution detected single matching account | |
| 24700 | Identity resolution by certificate succeeded - All_AD_Join_Points | |
| 22037 | Authentication Passed | |
| 12506 | EAP-TLS authentication succeeded | |
| 15036 | Evaluating Authorization Policy | |
| 24209 | Looking up Endpoint in Internal Endpoints IDStore - BMEDLOANL15 | |
| 24211 | Found Endpoint in Internal Endpoints IDStore | |
| 15048 | Queried PIP - Network Access.EapChainingResult (2 times) | |
| 15016 | Selected Authorization Profile - DenyAccess | |
| 15039 | Rejected per authorization profile | |
| 11503 | Prepared EAP-Success | |
| 11003 | Returned RADIUS Access-Reject |
The user auth then fails because no machine access was successful. If the endpoint is being found and successfully authenticated, I can not figure out why it's choosing deny access? The policy set is extremely simple, just as in the documentation above. What am I missing here? Any help at all would be appreciated.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2023 10:15 AM
After 1 month of unsuccessful community troubleshooting, it's time to call TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 12:48 PM
Hello Adam, I would recommend to double check your supplicant configuration, in the radius live log you are sharing it can be seen how ISE is receiving PEAP(MSCHAPv2) instead of the TEAP, apart from that in the livelog I can see ISE is just receiving the user authentication as part of the username, in a successful EAP CHAINING authentication you should be seeing the user and a comma separating it from the hostname, this will be included as a single username. I can see in the livelog you shared ISE is not receiving even an attempt to use TEAP from the endpoint, so that is why I would recommend you to check that first. Also, validate that you don't have a GPO pushing a different supplicant configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 01:18 PM
Thank you for the quick response. I double checked and there is no GPO pushing a configuration; I removed and re-added the configuration as shown in the video; this time I see in the radius log that it shows EAP-TLS instead of MSCHAP2 (still not TEAP specifically, not sure if it should or not) but the rest of the result is still the same, and it still still not showing a single authentication with user and hostname in one.
The one thing I see different from that video is that I don't have the option of EAP-TEAP, only Microsoft Tunnel EAP (TEAP)... I assume this is the same, and just a difference in how it's displayed in Windows 11 but I could be wrong there.
Is there any good documentation for setting up wireless with the windows 10/11 supplicant? Most of what I've found is either third party or only shows how to use AnyConnect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 10:46 PM
@adam imbruglio : It would help us validating your windows 10/11 supplicant configurations, if you may post the screenshots. If you can't share them, please engage Cisco TAC, instead.
5434 Endpoint conducted several failed authentications of the same scenarioare in your auth detailed reports. By default, ISE is enabled to suppress repeated failed clients -- clients with repeated authentication failures will be suppressed from the audit logs, and the requests from these clients will be automatically rejected for the specified time period.
The picture below shows how to bypass the suppression temporarily for an hour.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2023 02:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2023 05:42 PM
It's also important to understand how the supplicant works with EAP-TLS and TEAP. I would suggest having a look at the flows I describe in the 802.1x and TEAP sections of the following document.
Cisco ISE with Microsoft Active Directory, Azure AD, and Intune
The first step would be confirming you have a valid Computer certificate and User certificate enrolled (using the MMC snap-in). If you log out of the computer, you should see a successful Computer authentication session with the EAPChainingResult = User failed and computer succeeded. After that, you would need to log back in with the user account and check the authentication and EAPChainingResult.
If you have multiple certificates in the Computer and User store, that could also cause issues. In that case, you would want to use the Advanced section in the supplicant configuration to specify the Root and/or Intermediate CA that signed the certificate you intend to use for 802.1x.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 08:26 AM
@adam imbruglio The EapChainingResult attribute has four allowed values
- No chaining
- User and machine both succeeded
- User failed and machine succeeded
- User succeeded and machine failed
The policy set you showed in your initial post has rules for two of them so you would get DenyAccess if the endpoint has one of the other two values.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 09:21 AM
Yes, that's how the documentation at https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/216510-eap-chaining-with-teap.pdf shows it. Is that incorrect?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2023 01:44 PM
@adam imbruglio Please ensure the endpoint is NOT still getting
Event 5434 Endpoint conducted several failed authentications of the same scenarioAs the auth details reports might be misleading, if that is still the case.
From your existing reports, ISE did not seem to attempt EAP Chaining at all. Please make sure that is enabled in ISE as shown 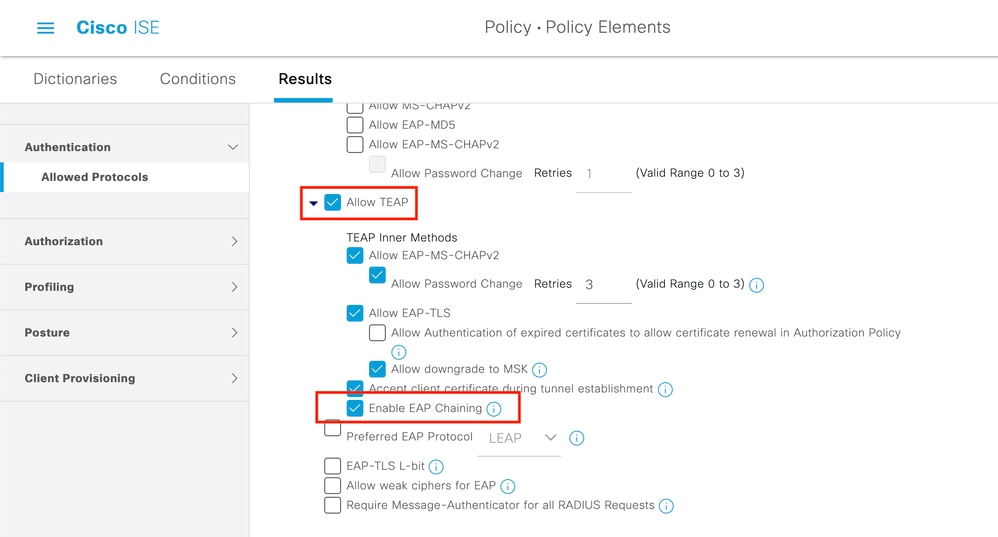 in the Step 1 of the ISE Tech Notes EAP Chaining with TEAP, which is contributed by a Cisco TAC engineer.
in the Step 1 of the ISE Tech Notes EAP Chaining with TEAP, which is contributed by a Cisco TAC engineer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2023 08:00 AM
Still running into the same roadblock. Yes, TEAP and EAP chaining are enabled. Windows still does not appear to be attempting eap chaining; I still get the same separate authentication attempts in the radius logs, with no "username comma machine name" in the logs.
I've updated ISE to 3.1 just in case that changed anything, but it hasn't made any difference, except that now I do not seem to be able to bypass suppression filtering; no sessions even appear in the live logs after trying and failing to connect repeatedly.
I did post my Windows supplicant settings above; can anyone confirm that that's correct? The documentation I've found for wireless setup all says to choose EAP-TEAP as a network authentication method, but that is not an option; the only options given are Smart card or other certificate (EAP-TLS), Protected EAP (PEAP), EAP-TTLS, or Tunnel EAP (TEAP).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2023 10:15 AM
After 1 month of unsuccessful community troubleshooting, it's time to call TAC.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



