- Cisco Community
- Technology and Support
- Security
- Network Access Control
- C9200 - MAB set up and not able to ping or access to a shared folder
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2023 09:39 AM
Hello,
I just installed a C9200 stack and configured the MAB with a RADIUS server. I added the mac address of my 40 users in the RADIUS, then I activated the MAB the necessary ports.
When I did this 2 days ago everything was fine a priori, but today a user pointed out to me that he couldn't access a shared remote folder on a windows server in the same LAN and that the PING towards this server are KO also
I checked the log in the RADIUS, everything is OK, the mac address is authorized
On the switch the port is OK
#show mac address-table | include ca63
18 d08e.790f.ca63 STATIC Gi1/0/10
#arp -a
192.168.100.246 d0-8e-79-0f-ca-63 dynamique
#show int status | include Gi1/0/18
Gi1/0/10 connected 18 a-full a-1000 10/100/1000BaseTX
And the server can communicate with the outside (connection on firewall OK)
I tried to debug with no success so I removed the MAB configuration from the port, unplugged/plugged the RJ45 cable and immediately access to the shared folder was OK and ping OK too.
Here's the configuration of my MAB and PORT
aaa new-model
!
!
aaa group server radius rad_access
server name yyyyyyyyyy
!
aaa authentication dot1x default group radius
aaa authorization network default group radius local
!
!
!
!
!
!
aaa session-id common
vtp mode off
!
dot1x system-auth-control
!
interface GigabitEthernet1/0/10
switchport access vlan 18
switchport mode access
authentication port-control auto
mab
spanning-tree portfast
!
radius server yyyyyyyyyy
address ipv4 192.168.100.248 auth-port 1812 acct-port 1813
key xxxxxxxxxxxxxxxxx
!
The server has been restarted 2 times before I come to debug without success
Can someone help me to debug this situation please?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 09:25 AM
Change:
aaa authentication dot1x default group radius
aaa authorization network default group radius local
To:
aaa authentication dot1x default group rad_access
aaa authorization network default group rad_access
Then try again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2023 10:24 AM
Nothing seems to be blocking on the switchport. Are you pushing any VLAN for DACL from the RADIUS server which could be blocking traffic to the shared folder. Share the output of "show authentication session interface gig 1/0/10 detail" at the time of issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 03:46 AM - edited 03-23-2023 03:54 AM
#show authentication session interface gig 1/0/10 detail
Interface: GigabitEthernet1/0/10
IIF-ID: 0x162AE369
MAC Address: d08e.790f.ca63
IPv6 Address: Unknown
IPv4 Address: Unknown
User-Name: d08e790fca63
Status: Authorized
Domain: DATA
Oper host mode: single-host
Oper control dir: both
Session timeout: N/A
Common Session ID: 0142C80A0000092F0DE04867
Acct Session ID: Unknown
Handle: 0xaf000081
Current Policy: POLICY_Gi1/0/10
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecured
Server Policies:
Method status list:
Method State
mab Authc Success
---------------
LOG from an other machine that ping this server:
With no MAB and no authentication port-control auto - Ping OK
With MAB and authentication port-control auto I've the following PING log.
Réponse de 192.168.100.246 : octets=32 temps=1 ms TTL=128
Réponse de 192.168.100.246 : octets=32 temps<1ms TTL=128
Réponse de 192.168.100.246 : octets=32 temps<1ms TTL=128
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Réponse de 192.168.100.250 : Impossible de joindre l'hôte de destination.
Réponse de 192.168.100.250 : Impossible de joindre l'hôte de destination.
Réponse de 192.168.100.250 : Impossible de joindre l'hôte de destination.
Réponse de 192.168.100.250 : Impossible de joindre l'hôte de destination.
Réponse de 192.168.100.250 : Impossible de joindre l'hôte de destination.
Réponse de 192.168.100.250 : Impossible de joindre l'hôte de destination.
Réponse de 192.168.100.250 : Impossible de joindre l'hôte de destination.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
Délai d'attente de la demande dépassé.
While the authentication is not finished ping is NOK with message "Impossible de joindre l'hôte de destination". and when authentication on RADIUS is done I'm in TIMEOUT with the message "Délai d'attente de la demande dépassé."
----------------
No authentication port-control + No MAB = Connection OK, ping possible in both directions, shared folder access OK
No authentication port-control + MAB = Connection OK, ping possible in both directions, access to the shared folder OK but windows is in limited connection (display no internet)
Authentication port-control + No MAB = No connection, ping not possible in both directions, the server is totally alone.
Authentication port-control + MAB = Connection is not fully OK. Ping only possible from server to anywhere but it cannot be contacted from LAN (ping or shared folder)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 04:09 AM
Hi
I'd say your problem can be related to this:
#show authentication session interface gig 1/0/10 detail
Interface: GigabitEthernet1/0/10
IIF-ID: 0x162AE369
MAC Address: d08e.790f.ca63
IPv6 Address: Unknown
IPv4 Address: UnknownI expected to see the IP address there and not Unknown.
When dealing with Radius, first you need to be authenticated and then you get an IP address.
Can you share the output of " show aaa servers" ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 05:37 AM
My RADIUS server is only used to validate that the MAC address is authorized to connect to the switch. VLAN is hard set on port configuration and never change with radius authentication.
Then a DHCP service is set up on the Fortigate firewall to distribute the IP addresses.
This server is out of DHCP range and has a fixed IP.
Here is the log you asked for.
The first one "yyyyyyyyyyy" is an oldest RADIUS server that is not set in the "aaa group server radius rad_access"
#show aaa servers
RADIUS: id 1, priority 1, host 192.168.100.250, auth-port 1812, acct-port 1813, hostname yyyyyyyyyyy
State: current UP, duration 1969545s, previous duration 0s
Dead: total time 0s, count 0
Platform State from SMD: current UP, duration 13s, previous duration 0s
SMD Platform Dead: total time 0s, count 979
Platform State from WNCD (1) : current UP
Platform State from WNCD (2) : current UP
Platform State from WNCD (3) : current UP
Platform State from WNCD (4) : current UP
Platform State from WNCD (5) : current UP
Platform State from WNCD (6) : current UP
Platform State from WNCD (7) : current UP
Platform State from WNCD (8) : current UP, duration 0s, previous duration 0s
Platform Dead: total time 0s, count 0UP
Quarantined: No
Authen: request 9824, timeouts 9824, failover 0, retransmission 7368
Response: accept 0, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 2456
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Dot1x transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
MAC auth transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 2456, failover 0
Transaction: total 2456, success 0, failure 2456
Author: request 0, timeouts 0, failover 0, retransmission 0
Response: accept 0, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
MAC author transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
Account: request 0, timeouts 0, failover 0, retransmission 0
Request: start 0, interim 0, stop 0
Response: start 0, interim 0, stop 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Elapsed time since counters last cleared: 3w1d19h5m
Estimated Outstanding Access Transactions: 0
Estimated Outstanding Accounting Transactions: 0
Estimated Throttled Access Transactions: 0
Estimated Throttled Accounting Transactions: 0
Maximum Throttled Transactions: access 0, accounting 0
Consecutive Response Failures: total 2455
SMD Platform : max 2455, current 2455 total 2455
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 0, current 0 total 0
Consecutive Timeouts: total 9823
SMD Platform : max 9823, current 9823 total 9823
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 0, current 0 total 0
Requests per minute past 24 hours:
high - 19 hours, 5 minutes ago: 0
low - 19 hours, 5 minutes ago: 0
average: 0
RADIUS: id 2, priority 2, host 192.168.100.248, auth-port 1812, acct-port 1813, hostname xxxxxxPP01
State: current UP, duration 1469897s, previous duration 0s
Dead: total time 0s, count 0
Platform State from SMD: current UP, duration 1464626s, previous duration 0s
SMD Platform Dead: total time 0s, count 6
Platform State from WNCD (1) : current UP
Platform State from WNCD (2) : current UP
Platform State from WNCD (3) : current UP
Platform State from WNCD (4) : current UP
Platform State from WNCD (5) : current UP
Platform State from WNCD (6) : current UP
Platform State from WNCD (7) : current UP
Platform State from WNCD (8) : current UP, duration 0s, previous duration 0s
Platform Dead: total time 0s, count 0UP
Quarantined: No
Authen: request 2507, timeouts 68, failover 2456, retransmission 51
Response: accept 118, reject 2321, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 955ms
Transaction: success 2439, failure 17
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Dot1x transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
MAC auth transactions:
Response: total responses: 2439, avg response time: 955ms
Transaction: timeouts 17, failover 2456
Transaction: total 2456, success 118, failure 2338
Author: request 0, timeouts 0, failover 0, retransmission 0
Response: accept 0, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
MAC author transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
Account: request 0, timeouts 0, failover 0, retransmission 0
Request: start 0, interim 0, stop 0
Response: start 0, interim 0, stop 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Elapsed time since counters last cleared: 2w3d18m
Estimated Outstanding Access Transactions: 0
Estimated Outstanding Accounting Transactions: 0
Estimated Throttled Access Transactions: 0
Estimated Throttled Accounting Transactions: 0
Maximum Throttled Transactions: access 0, accounting 0
Consecutive Response Failures: total 16
SMD Platform : max 16, current 0 total 16
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 0, current 0 total 0
Consecutive Timeouts: total 67
SMD Platform : max 67, current 0 total 67
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 0, current 0 total 0
Requests per minute past 24 hours:
high - 0 hours, 18 minutes ago: 0
low - 0 hours, 18 minutes ago: 0
average: 0
If that can help to investigate, I've this problem only for this server.
As example, I've an user that is connected today on port gi1/0/15 with MAC adress c81f663e7709 and IP 192.168.100.232
Here is the details on Cisco
#show mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
All 0100.0ccc.cccc STATIC CPU
All 0100.0ccc.cccd STATIC CPU
All 0180.c200.0000 STATIC CPU
All 0180.c200.0001 STATIC CPU
All 0180.c200.0002 STATIC CPU
All 0180.c200.0003 STATIC CPU
All 0180.c200.0004 STATIC CPU
All 0180.c200.0005 STATIC CPU
All 0180.c200.0006 STATIC CPU
All 0180.c200.0007 STATIC CPU
All 0180.c200.0008 STATIC CPU
All 0180.c200.0009 STATIC CPU
All 0180.c200.000a STATIC CPU
All 0180.c200.000b STATIC CPU
All 0180.c200.000c STATIC CPU
All 0180.c200.000d STATIC CPU
All 0180.c200.000e STATIC CPU
All 0180.c200.000f STATIC CPU
All 0180.c200.0010 STATIC CPU
All 0180.c200.0021 STATIC CPU
All ffff.ffff.ffff STATIC CPU
1 6026.aad9.da19 DYNAMIC Po3
1 6026.aad9.da1a DYNAMIC Po3
66 0009.0f09.0006 DYNAMIC Po3
66 04bd.97a5.854b STATIC Vl66
2 0000.5e00.0105 DYNAMIC Po3
2 0009.0f09.0006 DYNAMIC Po3
12 001a.a006.e6db DYNAMIC Po3
18 0009.0f09.0006 DYNAMIC Po3
18 c81f.663e.7709 STATIC Gi1/0/15
18 d08e.790f.ca63 DYNAMIC Gi1/0/10
18 f01f.afe1.886b DYNAMIC Po3
18 f01f.afe3.256d DYNAMIC Po3
Total Mac Addresses for this criterion: 33
#show authentication session interface gig 1/0/15 detail
Interface: GigabitEthernet1/0/15
IIF-ID: 0x13357A83
MAC Address: c81f.663e.7709
IPv6 Address: Unknown
IPv4 Address: Unknown
User-Name: c81f663e7709
Status: Authorized
Domain: DATA
Oper host mode: single-host
Oper control dir: both
Session timeout: N/A
Common Session ID: 0142C80A000004F608B9130B
Acct Session ID: Unknown
Handle: 0x8e000074
Current Policy: POLICY_Gi1/0/15
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecured
Server Policies:
Method status list:
Method State
mab Authc Success
# show run int Gi1/0/15
Building configuration...
Current configuration : 153 bytes
!
interface GigabitEthernet1/0/15
switchport access vlan 18
switchport mode access
authentication port-control auto
mab
spanning-tree portfast
end
There is no IP in the authentication details but I can ping it without problem
>ping 192.168.100.232
Envoi d'une requête 'Ping' 192.168.100.232 avec 32 octets de données :
Réponse de 192.168.100.232 : octets=32 temps=1 ms TTL=128
Réponse de 192.168.100.232 : octets=32 temps<1ms TTL=128
Réponse de 192.168.100.232 : octets=32 temps<1ms TTL=128
Statistiques Ping pour 192.168.100.232:
Paquets : envoyés = 3, reçus = 3, perdus = 0 (perte 0%),
Durée approximative des boucles en millisecondes :
Minimum = 0ms, Maximum = 1ms, Moyenne = 0ms
Ctrl+C
Thank you for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 06:23 AM
Hello,
As per the logs, I'd say the authentication is not happening.
Authen: request 9824, timeouts 9824, failover 0, retransmission 7368
Response: accept 0, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 2456
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Dot1x transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
MAC auth transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 2456, failover 0
Transaction: total 2456, success 0, failure 2456
Basiacally all the communication is failling between switch and Radius.
Which Radius server you have?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 06:43 AM - edited 03-23-2023 06:44 AM
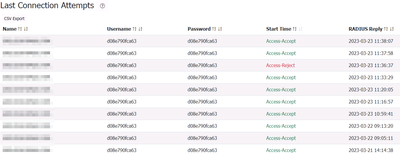
I use DaloRADIUS a web management application It is based on a FreeRADIUS deployment with a database server serving as the backend.
Here is the logs that I've on the connexion for this mac adress. All other MAC are in Access-Accept too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 07:45 AM
But as we can see almost all packets for authentication in failure status, the radius may receive the authentication packets, authorize but not reply to switch or reply and the switch is not receive or yet receiving but not processing.
Try to run some debugs
debug mab all & debug authentication all
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 07:52 AM
Also, as this is a FreeRadius, if you have access to the Linux server, run tcpdump to make sure you see packets in out from servr to switch and vice-versa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 09:10 AM
Here is the log for debug mab all & debug authentication all
XXXXXXSWPP01#term mon
XXXXXXSWPP01#show debug
Packet Infra debugs:
Ip Address Port
------------------------------------------------------|----------
XXXXXXSWPP01#debug mab all
All MAC Authentication Bypass debugging is on
XXXXXXSWPP01#debug authentication all
All Auth Manager debugging is on
XXXXXXSWPP01#
XXXXXXSWPP01#
*Mar 23 15:53:34.846: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
*Mar 23 15:53:34.846: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
*Mar 23 15:53:34.846: AUTH-EVENT: [Gi1/0/10] mac seen: 1 authz count[DATA]: 0 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
*Mar 23 15:53:36.443: %LINK-3-UPDOWN: Interface GigabitEthernet1/0/10, changed state to up
*Mar 23 15:53:37.444: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/10, changed state to up
*Mar 23 15:53:54.859: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
*Mar 23 15:53:54.859: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
*Mar 23 15:53:54.859: AUTH-EVENT: [Gi1/0/10] mac seen: 1 authz count[DATA]: 1 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
*Mar 23 15:53:54.862: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
*Mar 23 15:53:54.862: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
*Mar 23 15:53:54.862: AUTH-EVENT: [Gi1/0/10] mac seen: 1 authz count[DATA]: 1 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
*Mar 23 15:53:54.863: AUTH-EVENT: [Gi1/0/10] Incremented Session Count, new Count = 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 07:51 AM
Post 'show run aaa' (cleaned of your shared secrets of course)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 08:26 AM - edited 03-23-2023 08:26 AM
#show run aaa
!
aaa authentication dot1x default group radius
aaa authorization network default group radius local
username xxxxxxxxx secret 9 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
!
!
!
!
!
!
radius server yyyyyyyyyy
address ipv4 192.168.100.250 auth-port 1812 acct-port 1813
key procurve
!
radius server xxxxxxPP01
address ipv4 192.168.100.248 auth-port 1812 acct-port 1813
key procurve
!
!
aaa group server radius rad_access
server name xxxxxxPP01
!
!
!
!
aaa new-model
aaa session-id common
!
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 09:25 AM
Change:
aaa authentication dot1x default group radius
aaa authorization network default group radius local
To:
aaa authentication dot1x default group rad_access
aaa authorization network default group rad_access
Then try again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 09:29 AM
Also, ensure your shared secret for both radius servers is the same as what you have configured on the switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 10:01 AM
xxxxxxSWPP01(config)#aaa authentication dot1x default group rad_access
xxxxxxSWPP01(config)#aaa authorization network default group rad_access
xxxxxxSWPP01(config)#end
xxxxxxSWPP01#
xxxxxxSWPP01#
xxxxxxSWPP01#
xxxxxxSWPP01#
xxxxxxSWPP01#
Mar 23 16:42:30.601: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
Mar 23 16:42:30.601: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
Mar 23 16:42:30.601: AUTH-EVENT: [Gi1/0/10] mac seen: 0 authz count[DATA]: 0 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
Mar 23 16:42:30.603: AUTH-EVENT: [Gi1/0/10] Decremented Session Count, new Count = 0
Mar 23 16:42:30.604: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
Mar 23 16:42:30.604: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
Mar 23 16:42:30.604: AUTH-EVENT: [Gi1/0/10] mac seen: 0 authz count[DATA]: 0 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
Mar 23 16:42:31.589: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/10, changed state to down
Mar 23 16:42:32.589: %LINK-3-UPDOWN: Interface GigabitEthernet1/0/10, changed state to down
Mar 23 16:42:34.577: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
Mar 23 16:42:34.577: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
Mar 23 16:42:34.577: AUTH-EVENT: [Gi1/0/10] mac seen: 1 authz count[DATA]: 0 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
Mar 23 16:42:34.589: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
Mar 23 16:42:34.589: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
Mar 23 16:42:34.589: AUTH-EVENT: [Gi1/0/10] mac seen: 1 authz count[DATA]: 1 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
Mar 23 16:42:34.592: AUTH-EVENT: [Gi1/0/10] No session limit or profile present on interface
Mar 23 16:42:34.593: AUTH-EVENT: [Gi1/0/10] Got Session limit as 0 for interface Gi1/0/10
Mar 23 16:42:34.593: AUTH-EVENT: [Gi1/0/10] mac seen: 1 authz count[DATA]: 1 authz count[UNKNOWN]: 0 open access: 0 replace open set: 0 notify all: 1 block notification: 0
Mar 23 16:42:34.593: AUTH-EVENT: [Gi1/0/10] Incremented Session Count, new Count = 1
Mar 23 16:42:36.401: %LINK-3-UPDOWN: Interface GigabitEthernet1/0/10, changed state to up
Mar 23 16:42:37.402: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/10, changed state to up
I understand my error but I don't understand why my radius works.
So if I understand the correction that was made, I had configured the radius to query the wrong group.
I misunderstood the command and for me "aaa authentication dot1x default group radius" queries by default the group configured for the radius method when it is the name of the group itself.
On the other hand I do not understand why my RADIUS server received requests, accepted them or rejected them and that the stations were authorized or not to connect in spite of that. It remains a mystery.
Thank you very much for the time you took to help me.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide