- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE 2.6 and Juniper Device Administration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2020 02:41 PM - edited 05-18-2020 02:43 PM
Could anyone give me some assistance or at least some pointers on this one?
I'm running ISE 2.6.0.156.
I'm trying to figure out how to get it working so that our Juniper devices (we have several, like the SRX550 for example) can use ISE with RADIUS for device administration authentication. Currently these Juniper devices are using my Freeradius installation.
I've gotten part way there with old guides like https://www.redelijkheid.com/blog/2014/1/22/use-cisco-ise-for-radius-authentication-with-juniper-junos-devices and https://community.cisco.com/t5/security-documents/juniper-with-ise-2-0-configuration-guide/ta-p/3639809 and a few others. All the references I can find are for much older versions of ISE, which has changed considerably, so it's been a challenge to translate screenshots of the old ISE interface to the new one.
I've loaded the RADIUS dictionary successfully for Juniper, I've created an entry under Policy -> Policy Elements -> Results that sets up the Juniper:Juniper-Local-User-Name value so that I can point it do the appropriate identity on the Juniper for super user access.
Under Device Admin Policy Sets, I've got an entry set up to match devices in the juniper group that I created.
But this is basically where I'm at the end of what I can figure out.
My problem is that I can't figure out how to make it so that some users have access to the super users class, while others only get applied to a readonly class or operator class. I already have this worked out in Freeradius, certain ldap groups get certain classes, super user, readonly, or operator.
I just can't figure out how to do it in ISE.
Can anyone point me in the right direction?
Thanks!
--
Andy
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2020 04:51 PM
Hi @AHinNH
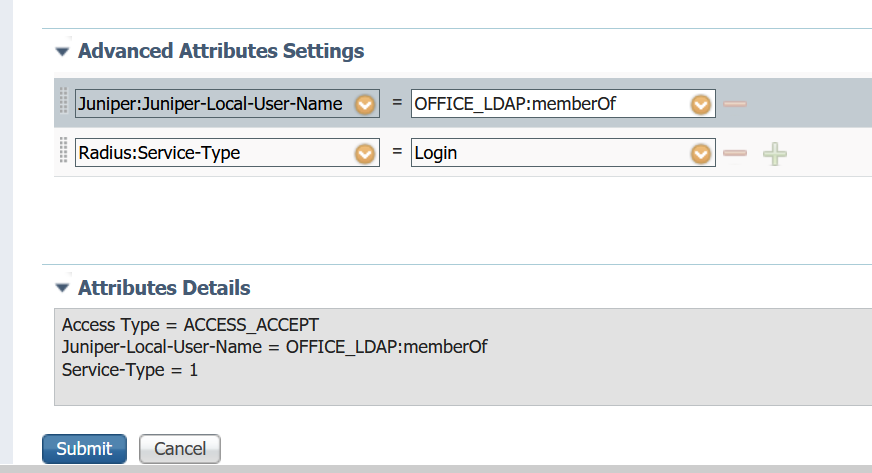
Ok I understand. The good news is that the ISE RADIUS Dictionary already contains the Juniper attribute
Juniper-Local-User-Name
that you're after. If that had not been the case then you would have had to create that as the first step. The other attribute is a standard IETF attribute.
Assuming your LDAP config is all good, and also assuming you have found the correct attribute in the LDAP directory that will return the AD group, then the rest is quite simple:
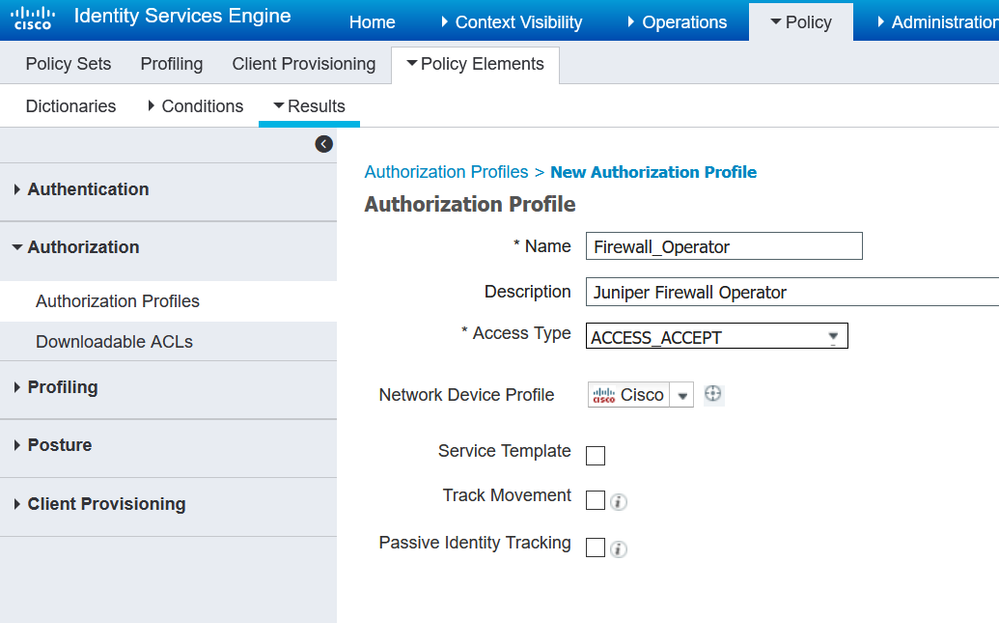
Step 1: Create and Authorization Profile - e.g. Firewall Operator (I don't have a Juniper Device Type, but Cisco will also work, assuming that you have added your Juniper Device and tagged it as a Cisco device - you should always match the device type that you gave the RADIUS client during Device Creation in ISE, with the device type that is shown in the Authorization Result - if these two don't match, then ISE won't return anything (unless the Auth result type is set to "Any" instead of a vendor)
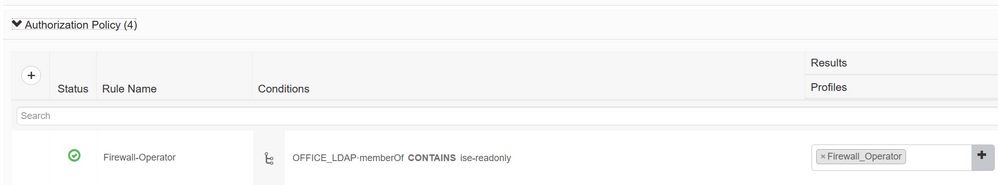
Step 2: Create/Edit your Authorization Policy Set
Then repeat that exercise for the admin role and other roles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2020 03:40 PM
Hi @AHinNH
It sounds like you're stuck on the Authorization part of the Policy Set.
The Authentication part should be easy, because you can reference the LDAP identity source.
The next step after that is the Authorization Policy.
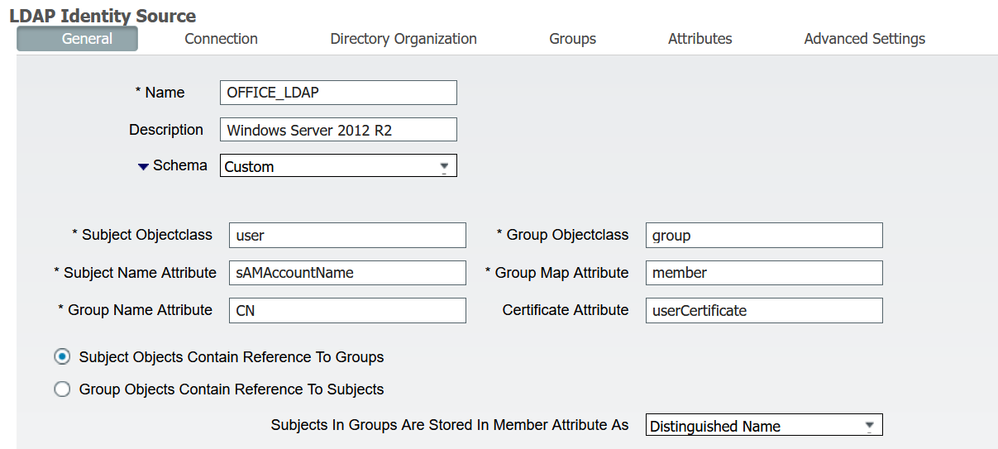
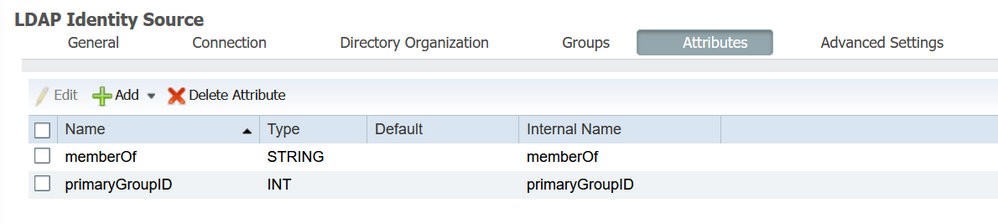
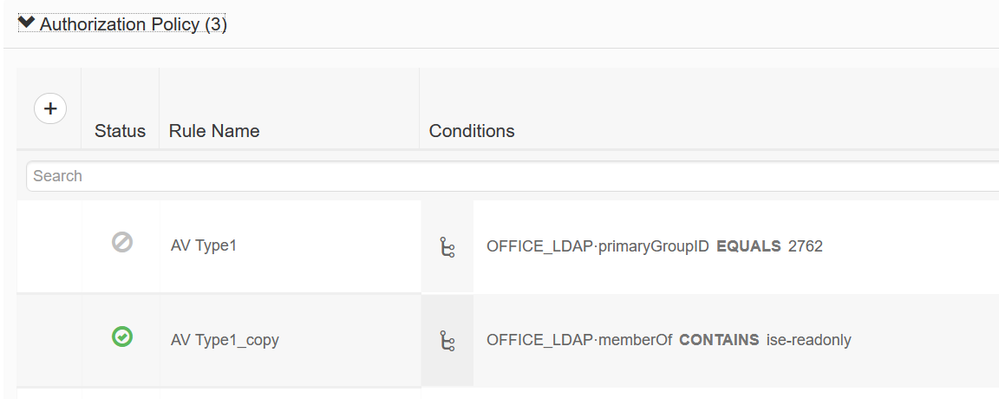
Here you will most likely have to refer to the user's LDAP Group(s) or Attribute(s). This might be where you are getting stuck, because you first have to add those Groups/Attributes during the LDAP configuration. Once you have those, you can use them in your Policy set. e.g.
You can browse the LDAP directory to retrieve the attributes you need for your Policy Set Logic
And then apply those in your Authorization Policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2020 08:00 PM
Thanks for the reply, though I already had that part set up.
Let me demonstrate what I mean with my freeradius configuration. In freeradius, this works:
DEFAULT ldap_firewall_virtual_server-LDAP-Group == "operator_ldap_group_name"
Service-Type = Login-User,
Juniper-Local-User-Name = "juniper_operator_user"
DEFAULT ldap_firewall_virtual_server-LDAP-Group == "admin_ldap_group_name"
Service-Type = Login-User,
Juniper-Local-User-Name = "juniper_admin_user"
The first line of each definition is for matching, the consecutive lines are in the radius response. So in this example, if you're a member of the corresponding LDAP group, the radius response will contain the appropriate value for the Juniper-Local-User-Name radius attribute. Works perfectly.
What I can't figure out how to do is to get ISE to send a radius response containing the appropriate attribute and value based on that LDAP group membership.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2020 04:51 PM
Hi @AHinNH
Ok I understand. The good news is that the ISE RADIUS Dictionary already contains the Juniper attribute
Juniper-Local-User-Name
that you're after. If that had not been the case then you would have had to create that as the first step. The other attribute is a standard IETF attribute.
Assuming your LDAP config is all good, and also assuming you have found the correct attribute in the LDAP directory that will return the AD group, then the rest is quite simple:
Step 1: Create and Authorization Profile - e.g. Firewall Operator (I don't have a Juniper Device Type, but Cisco will also work, assuming that you have added your Juniper Device and tagged it as a Cisco device - you should always match the device type that you gave the RADIUS client during Device Creation in ISE, with the device type that is shown in the Authorization Result - if these two don't match, then ISE won't return anything (unless the Auth result type is set to "Any" instead of a vendor)
Step 2: Create/Edit your Authorization Policy Set
Then repeat that exercise for the admin role and other roles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2020 06:33 AM
Thanks, Arne. I'll have to adapt that to my own environment, but I think that fills in that missing piece. I didn't notice it was possible to use an LDAP attribute as the value for the Juniper-Local-User-Name attribute. I can work with that.
I'm just wondering what version of ISE you're running? I'm running 2.6. In my version, where you show the screen clip for "Step 2: Create/Edit your Authorization Policy Set" mine looks slightly different. And not only does it look different, the only things I can choose from for the Results are the TACACS command sets and shell profiles.
In order to make your advice work, I just have to use a Device Profile instead of an Authorization Policy Set. So I was just wondering if you were using a version newer than mine and that the newer version allows you to choose more than just the TACACS command sets and shell profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2020 01:43 PM
Hello again - you mentioned FreeRADIUS and gave those examples. My examples are also RADIUS examples.
What you're describing to me is the ISE TACACS+ configuration screens (Cisco confusingly calls this "Device Admin" - I say confusingly, because TACACS is not the only device administration protocol in the world! They should have called that menu "TACACS+" instead).
If it's RADIUS you're after then you need to configure your stuff under /Policy/Policy Sets
TACACS+ is buried under the menu /Work Centers/Device Administration/Device Admin Policy Sets
BTW I am still on ISE 2.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2020 02:58 PM
#FACEPALM
Thanks for that tip. I've been focused almost exclusively on the TACACS+ support. Our Juniper devices we have can only do RADIUS and the weird division in ISE between TACACS+ and RADIUS configuration is definitely confusing. Starting to make more sense now. Thanks again!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide