- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE's retrieval of user's group membership from Active directory.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2018 11:36 PM - edited 02-21-2020 10:49 AM
Hello Experts,
I am quite new to Active directory's integration with Cisco ISE. Have found a document which is quite educative, however still have some doubts.
We are proposing a POC for a networking setup comprising of Cisco Wireless LAN Controller, ISE and Microsoft Active Directory.
a) We have a requirement to map multiple user groups defined on AD with multiple authorization policies defined on ISE.
b) The wireless users part of different user groups will associate through single WLAN SSID.
c) Authentication of wireless users takes at AD, while the authorization at ISE.
Based on the AD attribute tokenGroups, ISE evaluates the user's group member ship and accordingly applies authorization profile mapped against the user's group.
d) Authorization profiles will have each unique user's group with different privileges: Internet access/ Internet and Exchange Server Access / Internet, Exchange Server and Complete Enterprise Servers Access....
Below is the concern:
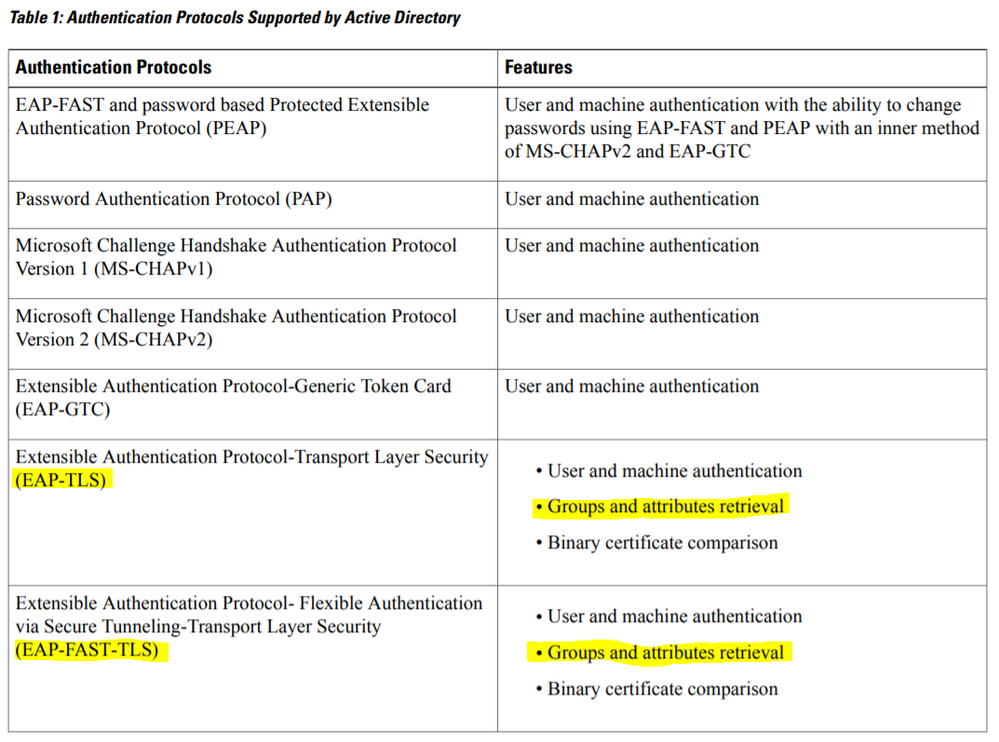
The authentication protocol that we are proposing is EAP-PEAP (MSCHAPv2). However if we see the table 1 of Cisco doc, it appears "User Groups and attributes retrieval" can take place only for EAP-TLS/ EAP-FAST-TLS.
Could someone please share the inputs on the POC that we are planning have, its limitations, repercussions and recommendations?
Can user group retrieval from AD to ISE happen when EAP-PEAP (MSCHAPv2) is the authentication method in use?
Excerpts from the document:
1. Cisco ISE uses the AD attribute tokenGroups to evaluate a user’s group membership. Cisco ISE machine account must have permission to read tokenGroups attribute.
2. You must configure Active Directory user groups for them to be available for use in authorization policies. Internally, Cisco ISE uses security identifiers (SIDs) to help resolve group name ambiguity issues and to enhance group mappings.SID provides accurate group assignment matching.
3. Authentication protocols supported by Active directory.
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2018 02:30 AM
Hi,
I wouldn't worry about that. Just configure your authentication/authorization rules to use the groups you've configured in AD.(after you've previsouly imported them into ISE - AD connector section groups/attributes)
Regarding this phrase -
c) Authentication of wireless users takes at AD, while the authorization at ISE.
The authentication will be dealt also by ISE (as in an authentication request) but using AD as a backend authentication server.
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 10:33 PM
Hi,
All your users have to belong to a specific group (HR, IT, etc).
Your SSID will have 802.1x configured for it. From ISE perspective, it's receiving 802.1x authentication requests from WLC/SSID_X.
Authentication policy:
Wireless_802.1x + SSID_X and
PEAP_MSCAPv2 - use Identity Source Seq LOCAL&AD
EAP_TLS - if issuer eq MyCA - use CA Source Seq
For the above its just an example showing you that for the same SSID you can actually use different eap authentication methods.
Authorization policy:
Wireless_8021x + SSID_X + (Internal ISE Group IT OR External AD Group IT) = IT_AUTHZ (that contains your specific/extra attributes)
Wireless_8021x + SSID_X + External AD Group HR = HR_AUTHZ (that contains your specific/extra attributes)
IT_AUTHZ = dACL name (it has to be configure on WLC) + extra attributes that you can push via radius vsa
BR,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2018 05:10 AM
. Answer is below:-
All your users have to belong to a specific group (HR, IT, etc).
Your SSID will have 802.1x configured for it. From ISE perspective, it's receiving 802.1x authentication requests from WLC/SSID_X.
Authentication policy:
Wireless_802.1x + SSID_X and
PEAP_MSCAPv2 - use Identity Source Seq LOCAL&AD
EAP_TLS - if issuer eq MyCA - use CA Source Seq
For the above its just an example showing you that for the same SSID you can actually use different eap authentication methods.
Authorization policy:
Wireless_8021x + SSID_X + (Internal ISE Group IT OR External AD Group IT) = IT_AUTHZ (that contains your specific/extra attributes)
Wireless_8021x + SSID_X + External AD Group HR = HR_AUTHZ (that contains your specific/extra attributes
IT_AUTHZ = dACL name (it has to be configure on WLC) + extra attributes that you can push via radius vsa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2018 02:30 AM
Hi,
I wouldn't worry about that. Just configure your authentication/authorization rules to use the groups you've configured in AD.(after you've previsouly imported them into ISE - AD connector section groups/attributes)
Regarding this phrase -
c) Authentication of wireless users takes at AD, while the authorization at ISE.
The authentication will be dealt also by ISE (as in an authentication request) but using AD as a backend authentication server.
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 11:43 PM
Thanks Octavian for your valuable inputs.
I am struggling to comprehend the flow of how things would work in my scenario.
Scenario:
Single SSID mapped with Multiple User Groups. Each User group may have unique user database (ISE local database/ AD), unique QoS requirement, unique Network Access privileges.....
I am basically looking for the flowchart, starting from client attempting association on an SSID, getting authenticated with ISE/ AD database and most importantly the role assignment handling at ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 10:33 PM
Hi,
All your users have to belong to a specific group (HR, IT, etc).
Your SSID will have 802.1x configured for it. From ISE perspective, it's receiving 802.1x authentication requests from WLC/SSID_X.
Authentication policy:
Wireless_802.1x + SSID_X and
PEAP_MSCAPv2 - use Identity Source Seq LOCAL&AD
EAP_TLS - if issuer eq MyCA - use CA Source Seq
For the above its just an example showing you that for the same SSID you can actually use different eap authentication methods.
Authorization policy:
Wireless_8021x + SSID_X + (Internal ISE Group IT OR External AD Group IT) = IT_AUTHZ (that contains your specific/extra attributes)
Wireless_8021x + SSID_X + External AD Group HR = HR_AUTHZ (that contains your specific/extra attributes)
IT_AUTHZ = dACL name (it has to be configure on WLC) + extra attributes that you can push via radius vsa
BR,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2018 03:59 AM
Thank you Octavian Szolga for your precious time in responding to the query :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2018 05:10 AM
. Answer is below:-
All your users have to belong to a specific group (HR, IT, etc).
Your SSID will have 802.1x configured for it. From ISE perspective, it's receiving 802.1x authentication requests from WLC/SSID_X.
Authentication policy:
Wireless_802.1x + SSID_X and
PEAP_MSCAPv2 - use Identity Source Seq LOCAL&AD
EAP_TLS - if issuer eq MyCA - use CA Source Seq
For the above its just an example showing you that for the same SSID you can actually use different eap authentication methods.
Authorization policy:
Wireless_8021x + SSID_X + (Internal ISE Group IT OR External AD Group IT) = IT_AUTHZ (that contains your specific/extra attributes)
Wireless_8021x + SSID_X + External AD Group HR = HR_AUTHZ (that contains your specific/extra attributes
IT_AUTHZ = dACL name (it has to be configure on WLC) + extra attributes that you can push via radius vsa
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide